PRE2016 4 Groep3: Difference between revisions
| Line 102: | Line 102: | ||
Most current research focuses on tracking of the people in the crowds. The individual tracking of people has proven to be difficult in a crowd context. Many different methods have been proposed for individual tracking and while these tend to work satisfactory for low to moderately crowded situations, they tend fall flat in higher density crowds. There are also models which try to use general crowd characteristics to detect anomalies, but these tend to ignore singular abnormalities and are better suited for detecting general locations in the scene which contain anomalies, for example where a fire has broken out. | Most current research focuses on tracking of the people in the crowds. The individual tracking of people has proven to be difficult in a crowd context. Many different methods have been proposed for individual tracking and while these tend to work satisfactory for low to moderately crowded situations, they tend to fall flat in higher density crowds. There are also models which try to use general crowd characteristics to detect anomalies, but these tend to ignore singular abnormalities and are better suited for detecting general locations in the scene which contain anomalies, for example where a fire has broken out.<ref name="crowd analysis techniques survey" /> | ||
Revision as of 16:42, 2 May 2017
Group members
| Student ID | Name |
| 0900940 | Ryan van Mastrigt |
| 0891024 | René Verhoef |
| 0854765 | Lisselotte van Wissen |
| 0944862 | Sjanne Zeijlemaker |
| 0980963 | Michalina Tataj |
Introduction
Problem description
Definitions
- Abnormal behaviour
- [explanation]
- Biometrics
- [explanation]
Objectives (/ TO DO list)
Goal: Develop a model for a video-based abnormal behaviour detection program
Objectives of this project:
- Formulate concrete problem statement
- Develop overview of the State-of-the-Art
- List of possible biometrics for detecting abnormal/suspicious behaviour
- List of different methods available for measuring biometrics (pros/cons, what method works best for what purpose/setting)
- Current areas of research
- Problems with current technologies
- Develop model scenarios for determining abnormal behavior
- Determine what constitutes abnormal behavior (heavily dependent on context)
- Determine what scenarios should be looked at (airports, sports stadia, banks)
- What techniques could be used (pros/cons, possible new ideas)
- Develop USE aspects
- Users:
- Develop easy-to-understand graphical interface for primary users
- Maintain sense of participation in primary users
- Conduct survey among general public to research support of such an application and to probe stance on privacy vs security
- Incorporate findings into design
- Society:
- Look into societal advantages (decreased criminal/terrorist activity, global sense of security, decrease in racial/religious tensions)
- Look into societal disadvantages (decrease in (perceived) privacy)
- Incorporate findings into design
- Enterprise:
- Make sure model is economically feasible and can compete with current systems
- Look into advantages/disadvantages for enterprises
- Incorporate findings into design
- Users:
- Finalize actual model design
- Create final presentation
The main goal of the model is to provide a general structure of a program which is capable of identifying suspicious persons for security applications. The method should be based on biometrics which can be used to determine abnormal behavior in order to obtain a higher success rate than comparable human-based surveillance.
The objectives of the model are:
- Technical objectives:
- Decrease false-negative rate compared to human-based surveillance
- Decrease false-positive rate compared to human-based surveillance
- Provide results to primary user(s) (security guards/police)
- USE objectives:
- Users:
- Provide easy-to-understand information to primary user
- Provide a higher sense of security (secondary user)
- Society:
- Decrease terrorist activity
- Higher global sense of security
- Higher crime prevention
- Decrease racial/religious tensions
- Enterprise:
- Create a system which is better than current systems, in order to sell to users
- Be economically feasible
- Decrease damage caused to assets (such as buildings) and maintain company reputation
- Users:
State-of-the-art
Possible biometrics for detecting abnormal behavior in crowds
In order to be able to detect abnormal behavior certain characteristics are required in order to identify agents in a a scene. Such characteristics are based on either physiological or behavioral characteristics and are generally referred to as biometrics. In order to asses the biometric the following conditions can be used:[1]
- Universality (every person in the scene should posses the trait)
- Uniqueness (it has to be sufficiently unique so that the agents can be distinguished between one another)
- Permanence (the trait should not vary too much over time)
- Measurability (the trait should be relatively easy to measure)
- Performance (relates to the speed, accurateness and robustness of the technology used)
- Acceptability (the subjects should be accepting towards the technology used)
- Circumvention (It should not be easy to imitate the metric)
Most research on identifying behavior via computer vision techniques are focused on non-crowded situations. The subject is either isolated or only a very small number of people are present. However, most of the conventional computer vision methods are not appropriate for use in crowded areas. This is partly due to the fact that people display different behavior in crowd context. As a result, some individual characteristics can no longer be used, but new collective characteristics of the crowd as a whole now emerge. Another big factor is the difficulty of identifying and tracking individuals in a crowd context. This is mostly due to occlusion of (parts of) the subject(s) by objects or other agents. The quality of the video image and the increased processing power needed to track individuals are also important factors.
[2]
Most current research focuses on tracking of the people in the crowds. The individual tracking of people has proven to be difficult in a crowd context. Many different methods have been proposed for individual tracking and while these tend to work satisfactory for low to moderately crowded situations, they tend to fall flat in higher density crowds. There are also models which try to use general crowd characteristics to detect anomalies, but these tend to ignore singular abnormalities and are better suited for detecting general locations in the scene which contain anomalies, for example where a fire has broken out.[2]
There are promising models that try to combine a bit of both extremes. There is a model which uses a set of low-level motion features to form trajectories of the people in the crowd, but uses an additional rule-set computed based on the longest common sub-sequences [3]. This results in a system that is capable of highlighting individual movements not coherent with the dominant flow. Another paper created an unsupervised learning framework to model activities and interactions in crowded and complicated scenes [4]. They used three elements: low-level visual elements, "atomic" activities and interactions. This model was capable of completing challenging visual surveillance tasks such as determining abnormalities.
Approach
Planning
In order to keep track of the progress of the project and set deadlines for our goals we have made a Gantt chart. This chart shows what tasks are done during what time.
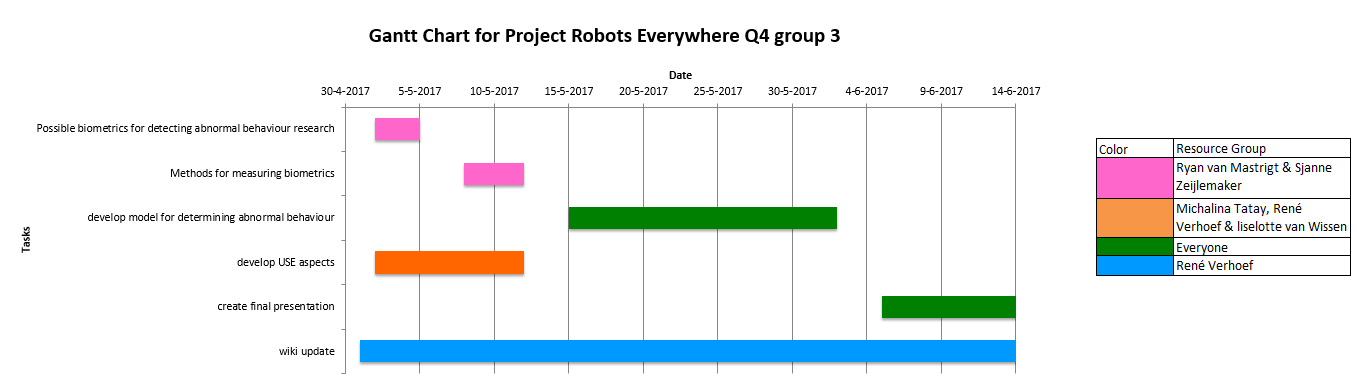
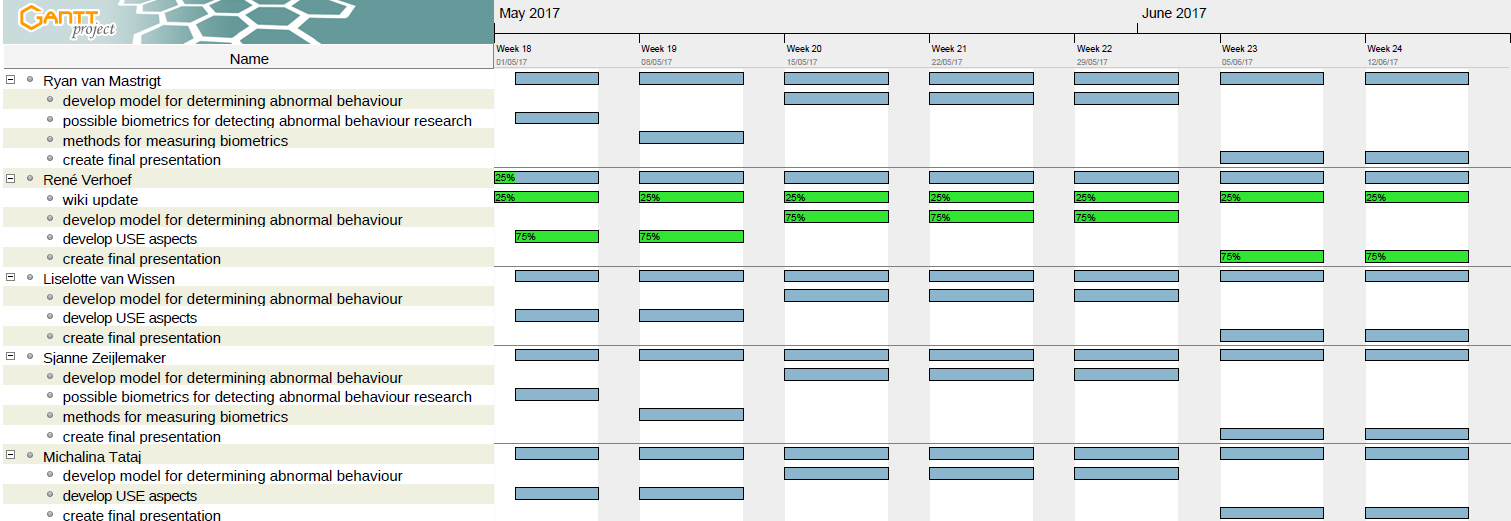
We also made a Resource Gantt chart that shows how tasks are divided over the group members.
Milestones
We consider several milestones based on the tasks that lay before us as can be seen in the Gantt chart in the Planning section:
- Finished the research into what defines abnormal Behaviour. (planned by the end of week 2)
- Finished the research into the existing methods for biometric scanning. (planned by the end of week 3)
- Finished analysing the USE aspects that our project brings with it. (planned by the end of week 3)
- Having developed a model for the detection of abnormal behaviour based on previous research and analyses. (planned by the end of week 6)
- Holding the final presentation presenting our product.(planned by the end of week 8)
- Finalized the wiki for judging. (planned by the end of week 8)
Deliverables
At the end of the project we aim to produce the following deliverables:
- A software model of a biometric scanner that detects suspicious behaviour
- Full documentation of the development and research process on this wiki
- A final presentation explaining said model and process
- A peer review of all group members
USE aspects
User
Primary users
- Security Guards
- Police officers
- Military personnel
Secondary users
- Persons being filmed
Tertiary users
- The people manufacturing the product
- The management responsible for buying the product
User friendliness
Sense of participation
Public survey
Society
Advantages
Terrorist/criminal activity
Security
Racial/religious tensions
Disadvantages
Privacy concerns
Enterprise
Feasibility
Advantages
Disadvantages
Model
[explanation of concept/pseudocode] [link to actual code?]
Results
References
- ↑ Jain, A., Bolle, R., & Pankanti, S. (Eds.). (2006). Biometrics: personal identification in networked society (Vol. 479). Springer Science & Business Media.
- ↑ 2.0 2.1 Junior, J. C. S. J., Musse, S. R., & Jung, C. R. (2010). Crowd analysis using computer vision techniques. IEEE Signal Processing Magazine, 27(5), 66-77.
- ↑ Cheriyadat, A. M., & Radke, R. J. (2008). Detecting dominant motions in dense crowds. IEEE Journal of Selected Topics in Signal Processing, 2(4), 568-581.
- ↑ Wang, X., Ma, X., & Grimson, W. E. L. (2009). Unsupervised activity perception in crowded and complicated scenes using hierarchical bayesian models. IEEE Transactions on pattern analysis and machine intelligence, 31(3), 539-555.
Minutes
26-04-2017
The subject of the project has been chosen and the deliverables and objectives (as found on the wiki) have been determined.
30-04-2017
- Orientary research has been performed to develop a better understanding of the subject and better define our goals.
- A planning and milestones have been determined (see the Approach section)
- A wiki page has been created, including a template for the documentation with the already available information filled in.