PRE2016 3 Groep12: Difference between revisions
| Line 192: | Line 192: | ||
'''Specific Category''' | '''Specific Category''' | ||
Operators should submit an operational declaration to the competent authority. The EASA shall provide standard scenarios, for which a risk assessment has been conducted, and mitigating measures have been identified. | Operators should submit an operational declaration to the competent authority. | ||
The EASA shall provide standard scenarios, for which a risk assessment has been conducted, and mitigating measures have been identified. | |||
If the operation does not correspond to any of the standard scenarios, the operator shall conduct a risk assessment and identify mitigation measures in order to limit the risk to an acceptable level. The operator should consider key factors such as operational area and conditions, and the category of airspace. The operator should also provide an operations manual adapted to the type of operation. | If the operation does not correspond to any of the standard scenarios, the operator shall conduct a risk assessment and identify mitigation measures in order to limit the risk to an acceptable level. The operator should consider key factors such as operational area and conditions, and the category of airspace. The operator should also provide an operations manual adapted to the type of operation. | ||
Revision as of 11:22, 20 March 2017
Group members
- Bibi Huijgen - 0906203
- Jamiro Leander
- Jari de Kroon - 0888168
- Juan van der Heijden - 0898805
- Plamen Pasliev - 0890518
- Stan Roelofs - 0892914
Introduction
In the year 2015 over 500000 cases of burglary and theft were recorded in the Netherlands [1]. It is by far the most common type of crime, around 57% of all crimes recorded in 2015 were related to burglaries. A recent trend is to setup neighbourhood prevention systems through mobile applications, however the effectiveness of this is limited due to the fact that most people will sleep at night when most burglary cases occur. Our aim is to reduce the big number of burglaries through the application of surveillance / security drones in areas where criminal rates are high. The drones should detect inappropriate behavior using an anomaly detection system.
Several issues arise in the application of drones:
- Legal issues regarding no fly zones and privacy.
- Technical issues related to the safety of the drone, since it will be flying near people.
- Using drones might be costly.
Besides the decreased rate of crimes, the introduction of this technology will allow for faster response times to other related crimes and hazards. The goal is to give the citizens an increased sense of security and safety.
Objectives
- Research what the effects on society will be when security drones are deployed.
- Research what the financial benefit would be to deploy surveillance drones.
- Research the legal issues regarding surveillance drones.
- Find out what the police thinks about surveillance drones.
- Find out what people think about surveillance drones.
Approach
- Research state of the art technologies using books and articles.
- Make an analysis of the current legislation regarding relevant topics such as filming humans and flying drones. Find out how privacy can be preserved and finally investigate if the current laws can be changed and how.
- Find out what people think of drones surveilling their neighbourhoods by making a survey and interviewing people.
- Make a financial model in Java where the input is an area and level of security and the output is the number of drones, cameras, or people that are needed to watch the area. To make the model we first have to use a drone to find out how high a drone can fly while still detecting humans without issues. We also need to know the costs of drones, security cameras, and people, and how long drones can fly before they have to be charged.
Product idea
We plan to use state-of-the art drones which are already equipped with cameras able to film in high resolution and framerate. We drafted a list of requirements for the product which you can find here. Afterwards we found a suitable drone candidate: DJI Phantom Pro 4. The drone is already programmable and supports autonomous flying, which means that they will follow a certain preprogramed map, and will deliver the footage to a human operator who will be responsible for detecting criminal activity and can take control of the device at any time. We also think to implement state-of-the art human detection software which will highlight humans filmed by a surveillance drone. We learnt that currently TU/e cameras do not have such software implemented so it would be a good addition to our system.
Security issues
In order to make the process secure enough we have to add some sort of encryption on multiple levels of the communication. We asked Tanja Lange, who is a cryptology proffessor in TU/e, to share some of her insight about this issue.
Stakeholders
There are several parties involved and every party has its own particular position. We will define how all are involved:
Government TU/e security Campus citizens and visitors
Financial Model
Human detection software
For the Human detectin software we found a framework called openCV: http://opencv.org/
We are going to try and implement this framework so that we can see from how far the drone's camera can still recognize a human.
Drone charging
Costs
Listed below are the factors we think will play a role in the costs of implementing this system in society:
Drones
One time costs
- Cost of a drone
- Cost of camera
- Cost of charging stations
- Amount of drones needed
- Amount of charging stations needed
Continues costs
- Range drone can search (height detection, speed)
- Battery life
- Cost of electricity
- Lifetime of a drone
- Detection efficiency
Cameras
- Cost of cameras
- Lifetime of a camera
- Amount of cameras needed
- Percentage of ground covered
- Detection efficiency
Police
- Police salary
- Cost of police car
- Amount of police needed
- Amount of police cars needed
- Covered ground
- Detection efficiency
Model
Conclusion
Law analysis
Current legislation
Filming humans
Currently, cameras film the campus almost everywhere. The footage is watched by security people in the control room and they decide whether action has to be taken. Footage is preserved for 7 days and then automatically deleted. In case there has been reported a crime, the relevant footage is filtered and used for security objectives. This footage is locked and only shared with responsible and legal authorities.
In case of drones instead of standing cameras, the footage will be treated equally. It will remain available for 7 days and after that all is deleted. Without detected anomalies, nobody sees the footage anymore.
Thus, the subject of privacy is comparable to current standards. Nowadays, all footage is filmed and analyzed and this will be the same situation using drones.
Flying drones
Legislation about flying drones can be found in "Regeling modelvliegen", which is about aircraft that is not able to carry a human, and is strictly used for demonstration, recreation, or sport.
Where can you fly drones ?
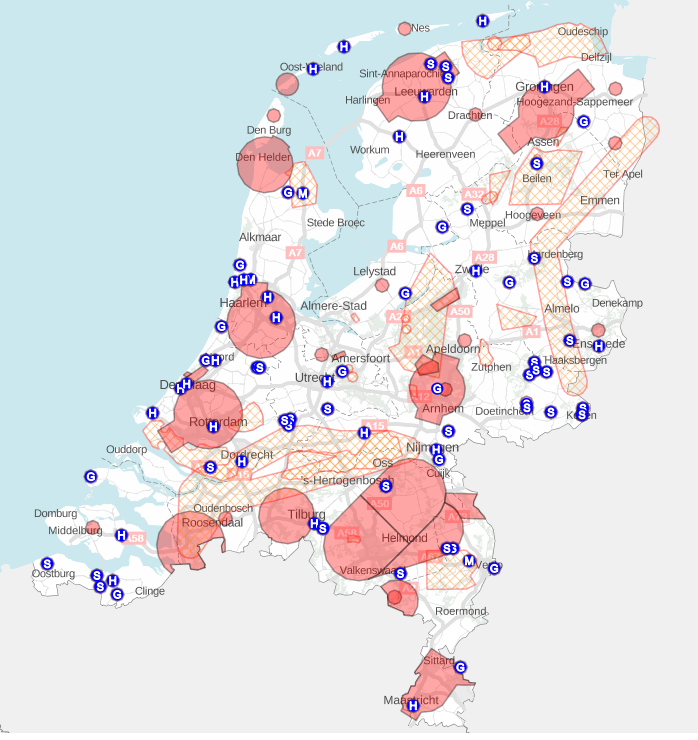
Certain areas are restricted for drones for example near airports. You are only allowed to fly drones in airspace category G, which is the free airspace. Sometimes there is a temporary restriction for example at big events. The red areas in the following image are restricted zones.
Apart from flying in airspace category G, there are some more general rules about flying drones:
- You are not allowed to fly higher than 120 meters above the ground or water.
- You have to give way to all other aircraft.
- You have to fly at a safe distance from people and buildings.
- You always have to be able to see the drone.
- You cannot fly in the dark.
Rules about drone specifications:
- Weight of the drone must not exceed 25 kilograms. (Will be changed to 4 kilograms)
Rules for business use of drones
The following rules hold if you want to use a drone to generate income. For example video production companies filming using a drone equipped with a camera, or inspection companies that want to inspect places that are difficult to reach.
If you want to use drones for business, you need a permit. There are different kinds of permits, it depends on the situation which one you need. If you are the pilot, you need a pilot license. The company that wants to use the drone needs a RPAS Operator Certificate (ROC). There are two kinds of ROC’s, ROC and ROC-light, which one you need depends on the weight of the drone and the height or distance you want to fly the drone at. The owner of the drone needs a proof of airworthiness and a proof of registration to the aviation register.
Penalties:
- Fines
- Confiscation
- Jail
How can privacy be preserved
Footage is stored only 7 days. Without any report of anomalies, the footage is deleted forever. In case people detect crimes or theft etc, the relevant footage is securily distributed to the parties involved (government security, police). Nobody has access to these images but the head of security, all footage is locked safely.
Obviously, safety is considered more important than privacy in case of an offense.
Can the law be changed, if so, how?
Plans of European Commission
The European Commission believes unmanned aircraft is a sector that is developing fast, and has a lot of potential for growth and to create jobs. In the next 20 years the drone sector in Europe is expected to employ more than 100,000 people, and have an economic impact of more than 10 billion euros per year. [4] "Unmanned aircraft" includes large aircraft, which resemble in terms of size and complexity manned aircraft, but also small consumer aircraft. Especially those smaller consumer aircraft are being used more frequently in the European Union. However, the rules are different for each country and often not everything is addressed.
Therefore the European Commission is working on new rules regarding drones. They define three categories of unmanned aircraft, each of these categories has different safety requirements which are proportional to the risk of the drones in that category. The categories are:
- “Open” (low risk): no authorization required to operate the aircraft, as long as forbidden or restricted areas, defined by the national aviation authority (NAA) are respected. Safety is ensured by operational limitations, mass limitations, product safety requirements, and a set of operational rules.
- “Specific” (medium risk): authorization required by a NAA, a risk assessment has to be performed by the operator. For certain lower risk scenarios, a simple declaration sent by the operator to the NAA will be sufficient.
- “Certified” (higher risk): requirements are similar to those for manned aviation. The process is comparable the process for manned aviation, oversight by NAA and European Aviation Safety Agency (EASA) will be required.
A prototype regulation[5] was presented in the summer of 2016. The document is a prototype regulation for the operation of drones in the open and specific categories. It does not constitute any formal commitment, its purpose is to inform and consult stakeholders. Feedback will be gathered which will be used to develop the actual regulation. It represents the current views of EASA. There is also an explanatory note[6] which provides the rationale and background for the prototype regulation. This regulation is supposed to enter into force in 2019.
Summary of Prototype Regulation
The prototype regulation addresses the “open” and “specific” categories.
Regulation should be proportionate to the nature and risk of the type of drone operation. It should take into account: the type of operation and whether the operation is open to the public; how dangerous the operation is to other air traffic, or persons and property on the ground; the type of airspace used; the complexity and performance of the aircraft; the type, scale, and complexity of the operation that is performed.
The risk of operating a drone varies depending on the characteristics of the drone and the type of operation. Therefore there should be different rules for different categories, based on risk assessment and performance.
The higher risk operations of unmanned aircraft should regulated similarly to manned aircraft, which includes the certification of the aircraft.
The lower risk operations should be regulated by less strict requirements. These operations will be subdivided into the “open” and “specific category”. Risk assessments should be conducted, in order to reduce the administrative burden for operators and authorities. Standard scenarios should be identified.
Open Category
Operation of unmanned aircraft in this category will fall into one of the following subcategories:
- A0: Operation that poses a negligible risk of severe injury to people on the ground or damage to manned aircraft. Requires neither specific pilot competence nor age limitations. Operations in this category should be conducted up to a height of 50 meters above ground level. Operators should maintain visual line of sight and the drone should not exceed a horizontal distance of 100 meters from the operator. The drone itself should have a weight of at most 250 grams, and a maximum speed of less than 15 meters per second.
- A1: Operation complying with requirements ensuring that they pose a negligible risk of severe injury to people on the ground or damage to manned aircraft. Requires neither specific pilot competence nor age limitations. Operations in this category should be conducted up to a height of 50 meters above ground level. Operators should maintain visual line of sight, and be at least 14 years old. The drone should have a weight of at most 25 kilograms.
- A2: Operation complying with requirements ensuring that they pose a limited risk of severe injury to people on the ground or damage to manned aircraft. Operators should be registered, and equipped with geofencing (virtually defined geographic boundaries) and electronic identification. Operations in this category should be conducted up to a height of 50 meters above ground level. The operator should maintain a minimum horizontal distance of 50 meters from uninvolved persons. Operators should maintain visual line of sight, be at least 14 years old, and have appropriate familiarisation according to the user manual of the drone. The drone must be equipped with geofencing and electronic identification systems. The drone should have a weight of at most 25 kilograms.
- A3: Operation complying with requirements imposing technical mitigations, like geofencing and electronic identification. These operations pose a higher risk of severe injury to people on the ground or damage to manned aircraft, and are operated by registered operators with higher competence. Operations in this category should be conducted up to a height of 150 meters above ground level. The operator should maintain a minimum horizontal distance of 20 meters from uninvolved persons. Operators should either maintain visual line of sight, or have an observer in visual line of sight. Operators should also be at least 14 years old, carry evidence of their competence of flying unmanned aircraft, and have the appropriate familiarisation to minimise the risk to third parties.. The drone must be equipped with geofencing and electronic identification systems. The drone should have a weight of at most 25 kilograms.
Specific Category
Operators should submit an operational declaration to the competent authority.
The EASA shall provide standard scenarios, for which a risk assessment has been conducted, and mitigating measures have been identified.
If the operation does not correspond to any of the standard scenarios, the operator shall conduct a risk assessment and identify mitigation measures in order to limit the risk to an acceptable level. The operator should consider key factors such as operational area and conditions, and the category of airspace. The operator should also provide an operations manual adapted to the type of operation.
After receiving an application for operational authorisation, the competent authority verifies that the application contains all the required information and documentation. The authority then decides whether or not they give an authorisation. The authorisation can be for limited or unlimited duration. This authorisation can later be suspended, revoked or amended if the operational conditions change.
Survey analysis
Survey
Interview
Analysis of results
Conclusion
Planning
Gantt chart: https://drive.google.com/open?id=1bb1QMkg4TYDTVDhT7nHERBCg_1VZtb98BMwWiS9wT6I
Conclusion
Discussion
Weekly logbook
Week 1 Starting here, the project was introduced and we formed groups. To generate an innovative and feasible idea, we held several brainstorm sessions. Coming up with a realistic approach to cure a relevant problem using technology, we shifted from several perspectives. In the end, we formulated a topic of research that entailed both security issues and privacy legislation. The basic ideas were covered in a presentation, to be given in week 2. We tried to create slides that were concise and complete, without too much text and with use of visuals.
Week 2 The presentation was completed and we started on the Wiki page. We figured that the regular update of the Wiki will contribute strongly to our progress. Besides, this logbook gives a good overview of our objectives and the aspects of the project that were already covered.
On Thursday, the presentation of the chosen project challenge will be given. Feedback from the other students and the expert panel can be implemented.
Week 3 After getting feedback on our first presentation, we had to change important aspects of our research plan. The most important parts that needed attention were stakeholders, privacy and benefit. We devided tasks, related to personal skill. You either work on programming or on the social/public part that considers law. In the future, it will be important to keep close communication between group members to ensure that everybody understands the progress in the two directions. It is obvious that the technology and society must work together to realize success.
Besides deviding tasks and narrowing down the procedure, time management was a very important part of this second week. The planning of the project needed a lot of time but it is a precondition for success. Now we know what, when and how to deliver parts and when we stick to the Gantt chart, we will realize an optimal research project.
We presented our time planning including the deadlines and tasks we defined. This is an important moment for feedback, as this is the last moment to check your project planning and idea in public. Something else that needed attention, was our resource allocation. It was important to check whether our ideas were feasible. After all, we planned out a detailed project and included our feedback.
Week 4 The division of tasks, created together with the Gantt chart, was executed this week for the first time. On Monday, the group was split in two, where three of us started to create the financial model and try the drone while the others focused on law and legislation. This second group also tried to contact the police office. We suspected that officers would have a very realistic view on our project and their opinion should be taken seriously. Unfortunately, one of our group members had an accident so we were working with five for the majority of this week.
On Thursday, we planned a feedback session with our expert panel. Learning goals will be discussed and evaluated.
Feedback on Thursday was mainly focused on following parts: - The target groups for our surveys; - Creating the boundaries for our research, mostly defining an area (e.g. the TU/e campus); - Formulating scenarios to present to the participants in questionnaires; - Find out what the security legislation is with regard to the chosen area; - Check European Commission legislation
Based on these instructions, we chose TU/e campus as target area and we divided tasks again. Two of us (as someone was injured) focused on the financial model to find out what the current costs are when using a drone. Two of us focused on the European Commission and it's legislation concerning privacy and the use of drones. One of us contacted the head of the security department of the TU/e to make an appointment. Besides, a document was created to inventarize all the relevant questions for the head of security. As the current situation is the starting point for development, these questions deserve a lot of attention.
Week 5 This week, we managed to create a solid base for our future studies. We arranged a meeting with the head of the TU/e Security section, mr Becks. He could answer all of our questions concerning surveillance and security on campus. From this point, we had enough information to develop a more reliable and realistic plan.
Also this week we started on the requirements document, we stated what our drone should be able to do and also stated some safety requirements.
On the financial model part, we defined more boundaries concerning the model:
Besides, we concluded that the police office is not that easily reached.
Week 6
This week, we continued working on the financial model, we determined what variables should be in the model and we made functions for some variables (for example the height vs line of sight. We also started to implement this in java so we can set some unknown variables.
Also we started looking for a drone that fits our requirements, as for now it seems that the Phantom 4 Pro fits our requirements the best.
For the law part we are looking into the European Prototype regulation which means the laws for drones might be changed in Europe, we don't only want to look into the current law but also what it could become and what are the possibilities then.
Week 7 Weekly feedback session between individual groups and expert panel. Feedback is on both learning goals (technical content and process).
Week 8 Final presentation and demonstration