PRE2024 1 Group2: Difference between revisions
No edit summary |
|||
| Line 203: | Line 203: | ||
== '''Interception''' == | == '''Interception''' == | ||
Drone interception refers to a range of methods used to incapacitate or destroy rogue drones once they have been detected and identified as threats. The rise of small drones, including both off-the-shelf and custom-built UAVs, has led to the development of many counter-drone systems that aim to neutralise drones in a non-destructive or destructive manner. The choice of method depends on various factors, including the environment, threat level, and available technology. | |||
==== Key Approaches to Interception ==== | |||
# Kinetic Interceptors: Kinetic methods physically destroy or incapacitate drones through direct impact. These include missile systems and kinetic projectiles, which engage drones at medium to long ranges. While effective, kinetic interceptors are typically expensive and may pose risks of collateral damage. Systems like the U.S. Army’s 40mm net grenade are non-lethal alternatives that physically trap drones without destruction, and at a low cost. | |||
# Electronic Warfare (Jamming and Spoofing): One of the most common drone neutralization techniques involves electronic warfare, such as radio frequency (RF) and GNSS jamming. These methods disrupt the drone’s control signals or GPS navigation, forcing it to lose connectivity and potentially crash. Spoofing, on the other hand, involves hijacking the drone’s communication system, allowing operators to redirect it. While jamming is non-lethal, it may affect other nearby electronics and is ineffective against autonomous drones that don’t rely on external control signals. | |||
# Directed Energy Weapons (Lasers and Electromagnetic Pulses): Directed energy systems like lasers and electromagnetic pulses (EMP) are designed to disable drones by damaging their electrical components or destroying them outright. Lasers offer precision and instant engagement but are costly and susceptible to environmental conditions like rain or fog. EMP systems can disable multiple drones at once but may also interfere with other electronics in the vicinity. | |||
# Net-Based Capture Systems: These systems use physical nets to ensnare drones, rendering them incapable of flight. The nets can be launched from ground-based platforms or other drones and are highly effective against low-speed, low-altitude UAVs. This method is non-lethal and minimizes collateral damage but has limitations in range and reloadability. | |||
# Geofencing: Geofencing involves creating virtual boundaries around sensitive areas using GPS coordinates. Drones equipped with geofencing technology are automatically programmed to avoid flying into restricted zones. This method is proactive but can be bypassed by modified or non-compliant drones | |||
==== Objectives of Effective Drone Neutralization ==== | |||
When designing or selecting a drone interception system, several key objectives must be prioritised: | |||
# Low Cost-to-Intercept: Cost-effectiveness is critical, as these small drones, off-the-shelf and custom-built UAVs are costing a lot more to intercept than to build, thus incurring a net negative cost on militaries. For example, using a $2 million Standard Missile-2 to intercept a drone that may cost as little as $2,000 is a clear example of this asymmetry. (<nowiki>https://www.csis.org/analysis/cost-and-value-air-and-missile-defense-intercepts</nowiki>) especially in environments where multiple drones may need to be intercepted over time. Some methods, such as net-based systems, offer a low-cost solution, while others, like lasers or kinetic interceptors, are more expensive(1-s2.0-S266737972200023…). | |||
# Portability: The ideal counter-drone system should be portable, lightweight, and collapsible for easy transportation and deployment in various settings. Systems like RF jammers and net throwers are typically more portable than missile-based solutions(AeroDefense Blog). | |||
# Ease of Deployment: The ability to quickly set up and deploy a system is vital, particularly in fast-moving scenarios such as military operations or protecting large events. Systems that can be operated from vehicles or drones provide greater flexibility in dynamic environments(Counter_Drone_Technolog…). | |||
# Quick Reloadability or Automatic Reloading: In high-threat environments, rapid reloading or automatic reloading capabilities ensure continuous protection against multiple drone incursions. Systems like laser-based or RF jammers offer this advantage, whereas net throwers and kinetic projectiles may need manual reloading(Counter_Drone_Technolog…). | |||
# Minimal Collateral Damage: Especially in civilian areas, minimizing collateral damage is critical. Non-lethal methods such as jamming, spoofing, and net-based systems are preferred in such environments, as they neutralize threats without causing widespread damage(Counter_Drone_Technolog…)(1-s2.0-S266737972200023…). | |||
==== Pros and Cons of Drone Interception Methods ==== | |||
=== Is it ethical to deflect or redirect drones and projectiles? === | === Is it ethical to deflect or redirect drones and projectiles? === | ||
Revision as of 07:43, 16 September 2024
Group Members
| Name | Student ID | Department |
|---|---|---|
| Max van Aken | 1859455 | Applied Physics |
| Robert Arnhold | 1847848 | Mechanical Engineering |
| Tim Damen | 1874810 | Applied Physics |
| Ruben Otter | 1810243 | Computer Science |
| Raul Sanchez Flores | 1844512 | Computer Science / Applied Mathematics |
Problem Statement
The goal of this project is to create an easily portable system that can be used as the last line of defense against incoming projectiles.
Objectives
To come up with a solution for our problem we have the following objectives in mind:
- Determine how drones and projectiles can be detected.
- Determine how a drone or projectile can be intercepted and/or redirected.
- Build a prototype of this portable device.
- Build a simulation of the usage of this system.
- Explore and determine ethical implications of the portable device.
- Prove the system’s utility.
Planning
Within the upcoming 8 weeks we will be working on this project. Below are the projects tasks layed out over these 8 weeks and when they will be performed.
| Week | Task |
|---|---|
| 1 | Initial planning and setting up the project. |
| 2 | Literary research. |
| 3 | Create ethical framework. |
| Conduct an interview with an expert to confirm and construct the use cases. | |
| Start constructing prototype, software and simulation concepts. | |
| Determine potential problems. | |
| 4 | Continue constructing prototype, software and simulation. |
| 5 | Finish prototype, software and simulation. |
| 6 | Testing prototype to verify its effectiveness and use cases. |
| Evaluate testing results and make final changes. | |
| 7 | Finish Wiki page. |
| 8 | Create final presentation. |
Users and their Requirements
We currently have two main usages for this project in mind, which are the following:
- Military forces facing threats from drones and projectiles.
- Privately-managed critical infrastructure in areas at risk of drone-based attacks.
The users of the system will require the following:
- Minimal maintenance
- High reliability
- System should not pose additional threat to surrounding
- System must be personally portable
- System should work reliably in dynamic, often extreme, environments
- System should be scalable and interoperable in concept
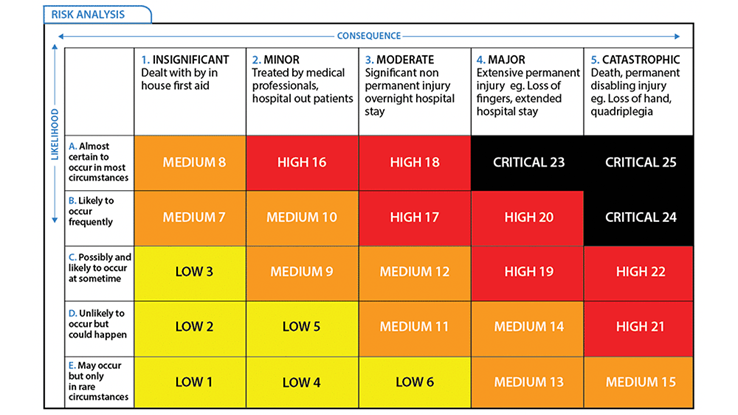
Risk Evaluation
A risk evaluation matrix can be used to determine where the risks are within our project. This is based on two factors: the consequence if a task is not fulfilled and the likelihood that this happens. Both of these factors are rated on a scale from 1 to 5 and using the matrix below a final risk is determined. This can be a low, medium, high or critical risk. Knowing the risks beforehand gives the ability to prevent failures from occurring as it is known where special attention is required.
| Task | Consequence (1-5) | Likelihood (1-5) | Risk |
| Collecting 25 articles for the SoTA | 1 | 1 | Low |
| Interviewing front line soldier | 1 | 2 | Low |
| Finding features for our system | 4 | 1 | Medium |
| Creating a simulation | 4 | 3 | High |
| Making a prototype | 3 | 3 | Medium |
| Make the wiki | 5 | 2 | High |
| Finding a detection method for drones and projectiles | 4 | 1 | Medium |
| Determine (ethical) method to intercept or redirect drones and projectiles | 5 | 1 | Medium |
| Prove the systems utility | 5 | 2 | High |
Detection
Drone Detection
The Need for Effective Drone Detection
With the rapid advancement and production of unmanned aerial vehicles (UAV), particularly small drones, new security challenges have emerged for the military sector.[2] Drones can be used for surveillance, smuggling, and launching explosive projectiles, posing threats to infrastructure and military operations.[2] Within our project we will be mostly looking at the threat of drones launching explosive projectiles. We have as an objective to develop a portable, last-line-of-defense system that can detect drones and intercept and/or redirect the projectiles they launch. An important aspect of such a system is the capability to reliably detect drones in real-time, while possibly in dynamic environments.[3] The challenge here is to create a solution that is not only effective but also lightweight, portable, and easy to deploy.
Approaches to Drone Detection
Numerous approaches have been explored in the field of drone detection, each with its own set of advantages and disadvantages.[4][3] The main methods include radar-based detection, radio frequency (RF) detection, acoustic-based detection, and vision-based detection.[2][4] It is essential for our project to analyze these methods within the context of portability and reliability, to identify the most suitable method, or combination of methods.
Radar-Based Detection
Radar-based systems are considered as one of the most reliable methods for detecting drones.[4] Radar systems transmit short electromagnetic waves that bounce off objects in the environment and return to the receiver, allowing the system to detect the object's attributes, such as range, velocity, and size of the object.[4][3] Radar is especially effective in detecting drones in all weather conditions and can operate over long ranges.[2][4] Radars, such as active pulse-Doppler radar, can track the movement of drones and distinguish them from other flying objects based on the Doppler shift caused by the motion of propellers (the micro-Doppler effect).[2][3][4]
Despite its effectiveness, radar-based detection systems come with certain limitations that must be considered. First, traditional radar systems are rather large and require significant power, making them less suitable for a portable defense system.[4] Additionally, radar can struggle to detect small drones flying at low altitudes due to their limited radar cross-section (RCS), particularly in cluttered environments like urban areas.[4] Millimeter-wave radar technology, which operates at high frequencies, offers a potential solution by providing better resolution for detecting small objects, but it is also more expensive and complex.[4][2]
Radio Frequency (RF)-Based Detection
Another common method is detecting drones through radio frequency (RF) analysis.[2][3][4][5] Most drones communicate with their operators via RF signals, using the 2.4 GHz and 5.8 GHz bands.[2][4] RF-based detection systems monitor the electromagnetic spectrum for these signals, allowing them to identify the presence of a drone and its controller on these RF bands.[4] One advantage of RF detection is that it does not require line-of-sight, implying that the detection system does not need to have a view of the drone.[4] It can also operate over long distances, making it effective in a large pool of scenarios.[4]
However, RF-based detection systems do have their limitations. They are unable to detect drones that do not rely on communication with another operator, as in autonomous drones.[3] Also, the systems are less reliable in environment where many RF signals are presents, such as cities.[4] Therefore in situations where high precision and reliability are a must, RF-based detection might not be too suitable.
Acoustic-Based Detection
Acoustic detection systems rely on the unique sound signature produced by drones, patricularly the noise generated by their propellers and motors.[4] These systems use highly sensitive microphones to capture these sounds and then analyze the audio signals to identify the presence of a drone.[4] The advantage of this type of detection is that it is rather low cost and also does not require line-of-sight, therefore this type of detection is mostly used for detecting drones behind obstacles in non-open spaces.[4][2]
However, it also has its disadvantages. In environments with a lot of noise, as in a battlefields, these systems are not as effective.[3][4] Additionally, some drones are designed to operate silently.[3] Also, they only work on rather short range, since sound weakens over distance.[4]
Vision-Based Detection
Vision-based detection systems use camera, either in the visible or infrared spectrum, to detect drones visually.[2][4] These system rely on image recognition algotihms, often by use of machine learning.[4][5] Drones are then detected based on their shape,size and movement.[5] The main advantage of this type of detection is that the operators themselves will be able to confirm the presence of a drone, and are able to differentiate between a drone and other objects such as birds.[4]
However, there are also disadvantages when it comes to vision-based detection systems.[3][4] These systems are highyl dependent on environmental conditions, they need a clear line-of-sight and good lightning, additionally weather conditions can have an impact on the accuracy of the systems.[3][4]
Best Approach for Portable Drone Detection
For our project, which focuses on a portable system, the ideal drone detection method must balance between effectiveness, portability and ease of deployment. Based on this, a sensor fusion approach appear to be the most appropriate.[4]
Sensor Fusion Approach
Given the limitations of each individual detection method, a sensor fusion approach, which would combine radar, RF, acoustic and vision-based sensors, offers the best chance of achieving reliable and accurate drone deteciton in a portable system.[4] Sensor fusion allows the strengths of each detection method to complement the weaknesses of the others, providing more effective detection in dynamic environments.[4]
- Radar Component: A compact, millimeter-wave radar system would provide reliable detection in different weather conditions and across long ranges.[3] While radar systems are traditionally bulky, recent advancements make it possible to develop portable radar units that can be used in a mobile systems.[4] These would most likely be less effective, therefore to compensate a sensor fusion approach would be used.[4]
- RF Component: Integrating an RF sensor will allow the system to detect drones communicating with remote operators.[4] This component is lightweight and relatively low-power, making it ideal for a portable system.[4]
- Acoustic Component: Adding acoustric sensors can help detect drones flying at low altitudes or behind obstacles, where rader may struggle.[2][4] Also this component is mainly just a microfone and the rest is dependent on software, and therefore also ideal for a portable system.[4]
- Vision-Based Component: A camera system equipped with machine learning algorithms for image recognition can provide visual confirmation of detected drones.[5][4] This component can be added by use of lightweight, wide-angle camera, which again does not restrict the device from being portable.[4]
Conclusion
To achieve portability in our system we have to restrict certain sensors and/or components, therefore to still achieve effectivity when it comes to drone detection, the best apporach is sensor fusion. The system would integreate radar, RF, acoustic and vision-based detection. These together would compensate for eachothers limitations resulting in an effective, reliable and portable system.
Interception
Drone interception refers to a range of methods used to incapacitate or destroy rogue drones once they have been detected and identified as threats. The rise of small drones, including both off-the-shelf and custom-built UAVs, has led to the development of many counter-drone systems that aim to neutralise drones in a non-destructive or destructive manner. The choice of method depends on various factors, including the environment, threat level, and available technology.
Key Approaches to Interception
- Kinetic Interceptors: Kinetic methods physically destroy or incapacitate drones through direct impact. These include missile systems and kinetic projectiles, which engage drones at medium to long ranges. While effective, kinetic interceptors are typically expensive and may pose risks of collateral damage. Systems like the U.S. Army’s 40mm net grenade are non-lethal alternatives that physically trap drones without destruction, and at a low cost.
- Electronic Warfare (Jamming and Spoofing): One of the most common drone neutralization techniques involves electronic warfare, such as radio frequency (RF) and GNSS jamming. These methods disrupt the drone’s control signals or GPS navigation, forcing it to lose connectivity and potentially crash. Spoofing, on the other hand, involves hijacking the drone’s communication system, allowing operators to redirect it. While jamming is non-lethal, it may affect other nearby electronics and is ineffective against autonomous drones that don’t rely on external control signals.
- Directed Energy Weapons (Lasers and Electromagnetic Pulses): Directed energy systems like lasers and electromagnetic pulses (EMP) are designed to disable drones by damaging their electrical components or destroying them outright. Lasers offer precision and instant engagement but are costly and susceptible to environmental conditions like rain or fog. EMP systems can disable multiple drones at once but may also interfere with other electronics in the vicinity.
- Net-Based Capture Systems: These systems use physical nets to ensnare drones, rendering them incapable of flight. The nets can be launched from ground-based platforms or other drones and are highly effective against low-speed, low-altitude UAVs. This method is non-lethal and minimizes collateral damage but has limitations in range and reloadability.
- Geofencing: Geofencing involves creating virtual boundaries around sensitive areas using GPS coordinates. Drones equipped with geofencing technology are automatically programmed to avoid flying into restricted zones. This method is proactive but can be bypassed by modified or non-compliant drones
Objectives of Effective Drone Neutralization
When designing or selecting a drone interception system, several key objectives must be prioritised:
- Low Cost-to-Intercept: Cost-effectiveness is critical, as these small drones, off-the-shelf and custom-built UAVs are costing a lot more to intercept than to build, thus incurring a net negative cost on militaries. For example, using a $2 million Standard Missile-2 to intercept a drone that may cost as little as $2,000 is a clear example of this asymmetry. (https://www.csis.org/analysis/cost-and-value-air-and-missile-defense-intercepts) especially in environments where multiple drones may need to be intercepted over time. Some methods, such as net-based systems, offer a low-cost solution, while others, like lasers or kinetic interceptors, are more expensive(1-s2.0-S266737972200023…).
- Portability: The ideal counter-drone system should be portable, lightweight, and collapsible for easy transportation and deployment in various settings. Systems like RF jammers and net throwers are typically more portable than missile-based solutions(AeroDefense Blog).
- Ease of Deployment: The ability to quickly set up and deploy a system is vital, particularly in fast-moving scenarios such as military operations or protecting large events. Systems that can be operated from vehicles or drones provide greater flexibility in dynamic environments(Counter_Drone_Technolog…).
- Quick Reloadability or Automatic Reloading: In high-threat environments, rapid reloading or automatic reloading capabilities ensure continuous protection against multiple drone incursions. Systems like laser-based or RF jammers offer this advantage, whereas net throwers and kinetic projectiles may need manual reloading(Counter_Drone_Technolog…).
- Minimal Collateral Damage: Especially in civilian areas, minimizing collateral damage is critical. Non-lethal methods such as jamming, spoofing, and net-based systems are preferred in such environments, as they neutralize threats without causing widespread damage(Counter_Drone_Technolog…)(1-s2.0-S266737972200023…).
Pros and Cons of Drone Interception Methods
Is it ethical to deflect or redirect drones and projectiles?
The goal in this project is to deflect or redirect drones and projectiles for soldiers to be safe. But by deflecting or redirecting these drones and projectiles they do not disappear. Chances are that other people get injured by doing such acts. So is it even ethical to deflect or redirect these drones or projectiles?
According to the International Humanitarian Law (IHL), article 49 specifically, an attack is seen as any act of violence, whether in offence or defense. This means that the deflection or redirection of drones and projectiles is seen as an attack. But since this piece of technology is used in warzones, attacks are really common there, so this should not be a big problem. By deflecting or redirecting an attack, it is simply a continuation of an already ongoing attack. This would simply lead to the conclusion that it is ethical to deflect or redirect drones and projectiles. However, deflection or redirection can also cause harm to other people on the defending side or even civilians. It is not a guarantee that the attack will be deflected or redirected to the attacking side. As for a deflection or redirection to other people on the defending side, it raises the idea of the trolley problem, where an attack is deflected or redirected to save a large number of people by sacrificing some others. As for a deflection or redirection to civilians, you are attacking people who are no harm to you is simply unethical and also, for that reason, forbidden by law.
For now this technology must be used with caution and the risks should be clear for anyone using this technology. Since there is no guarantee yet where projectiles will go, it should not be allowed in areas with civilians. It is important however to keep developing this technology as it can save a lot of lives in the future, as when technology develops further it may be possible to accurately determine the path where the drones or projectiles go.
Ethical Framework
Description
The goal of this project is to create an easily portable system that can be used as the last line of defence against incoming projectiles. In order to come up with a sufficient ethical framework this description needs to be more specified and categorised. The device under consideration is capable of neutralising an incoming projectile. However, an incoming projectile doesn’t always have to be neutralised and this can differ between situations. In order to describe the ethical implications of this device three different situations are going to be described with each its own ethical framework which together will form the total ethical framework of the device.
- Construction work is a dangerous job when it comes to the number of fatal work injuries [1]. Fatal injuries on construction sites in the U.S are roughly 1000 per year with around 11% due to falling objects. There are roughly 80.000 non-fatal injuries with around 20% due to falling objects. This could be prevented by the device under consideration. If the net is strong enough and has enough momentum it could be able to redirect certain falling objects, such as bricks or a hammer, such that it does not hit a worker.
- Watching live sports can be surprisingly dangerous, and organising large events in stadiums is no easy task. Evacuation plans and logistics for a packed stadium are a nightmare. Luckily this is overall handled well, but there is one more dangerous aspect to watching sports in the stadium. Foul balls for example can get into the spectators area and potentially harm people [3]. Nearly 75% of spectators who get hit by a hockey game require stitches for their injuries.
- This device could also be used in war zone situations. For example if soldiers are in trenches it is hard for the enemy to hit them, so a solution that is nowadays used in Ukraine is drones [???]. A war zone is in general a rapidly evolving environment so the soldiers and equipment need to be able to adapt to that [4]. In order to give certainty that the device will neutralise the harmful projectile there needs to be an extensive software framework which can distinguish for example birds from drones, but can also detect grenades dropped from higher altitude.
Ethics
Autonomous (decision making)
Soldiers vs civilians (geneva convention)
- To be done
- To be done
(3) In this scenario the device will be actively used in a war zone. Therefore it should comply with the Geneva conventions. It should thus be able to examine the impact its actions would make for civilians and it must be certain it will not do harm to civilians directly or indirectly. To illustrate, if a kamikaze drone is heading towards a military vehicle, the device will either redirect the drone or let the drone explode above the ground based on the type of interception that is chosen. If the drone is redirected to not hit too close to the military vehicle, it might be that the kamikaze drone injures civilians. If the drone explodes above the ground, the fragments will still shoot downwards causing injuries over a larger area, possibly including civilians [???]. This not only violates the Geneva convention, but also misses the point of preventing harm. In order to make sure this is not something that will happen the device must be able to choose a desired and achievable location to redirect an incoming drone towards. If the device is made autonomous in such a situation the question of responsibility and accountability begin to play a role as well. The easiest way to bypass this difficult question is to include a human in the final decision making. This however might take too much time as a result of which the drone will still hit its intended target.
References
[1] https://www.bls.gov/charts/census-of-fatal-occupational-injuries/number-and-rate-of-fatal-work-injuries-by-industry.htm
[2] https://blogs.cdc.gov/niosh-science-blog/2023/04/04/2023-struck-by-stand-down/
[3] https://www.herrmanandherrman.com/blog/safety-stadium-managing-risk/
[4] https://ndupress.ndu.edu/Portals/68/Documents/jfq/jfq-101/jfq-101_78-83_Lynch.pdf?ver=Gu3iNHVHh5wYTbAPOqwd7Q%3d%3d
Simulation
The Use of the Simulation
The simulation for this project is being made to explore the design and functionality of the system. Our main priority will be to bring the system alive throught the means of a prototype, however since this brings with it its limitations when it comes to possible capabilities and time, we will also be looking to bring the project alive throught the means of a simulation. The simulation allows us to represent the prototype in multiple use cases and creates a better understanding as to how it would perform in real-life scenarios.
Simulation Software
There are numerous software to use for our simulation. However for our simulation we do need to consider that the project needs to be finished in a short time span, thus a not too steep learning curve is required. Additionally, we want to focus more on the visual aspect than the physics aspects of the system, but would prefer software that allows the extension of adding aspects of physics in the system.
As we require the above from the software we compared Unity3D and Gazebo with the use of ROS.[6] Unity3D and ROS-Gazebo both are valid options. However, Unity3D scales better to larger environment, has better visual qualities, and is more capable of real-time simulation.[6] On the other hand, ROS-Gazebo has more existing sensor plugins, allowing a more realisitic showing of how the actual device would work.[6]
As we want to focus mostly on the visual aspect of our device and to visualise what it would look like in action we believe Unity3D to be a more suitable option. Additionally, Unity3D does still always allow for extension for more realisitic physics if this extension wants to be made.
Literary Research
Autonomous Weapons Systems and International Humanitarian Law: Need for Expansion or Not[7]
A significant challenge with autonomous systems is ensuring compliance with international laws, particularly IHL. The paper delves into how such systems can be designed to adhere to humanitarian law and discusses critical and optional features such as the capacity to identify combatants and non-combatants effectively. This is directly relevant to ensuring our system's utility in operational contexts while adhering to ethical norms.
Artificial Intelligence Applied to Drone Control: A State of the Art[5]
This paper explores the integration of AI in drone systems, focusing on enhancing autonomous behaviors such as navigation, decision-making, and failure prediction. AI techniques like deep learning and reinforcement learning are used to optimize trajectory, improve real-time decision-making, and boost the efficiency of autonomous drones in dynamic environments.
Drone Detection and Defense Systems: Survey and Solutions[2]
This paper provides a comprehensive survey of existing drone detection and defense systems, exploring various sensor modalities like radio frequency (RF), radar, and optical methods. The authors propose a solution called DronEnd, which integrates detection, localization, and annihilation functions using Software-Defined Radio (SDR) platforms. The system highlights real-time identification and jamming capabilities, critical for intercepting drones with minimal collateral effects.
Advances and Challenges in Drone Detection and Classification[4]
This state-of-the-art review highlights the latest advancements in drone detection techniques, covering RF analysis, radar, acoustic, and vision-based systems. It emphasizes the importance of sensor fusion to improve detection accuracy and effectiveness.
Autonomous Defense System with Drone Jamming capabilities[8]
This patent describes a drone defense system comprising at least one jammer and at least one radio detector. The system is designed to send out interference signals that block a drone's communication or GPS signals, causing it to land or return. It also uses a technique where the jammer temporarily interrupts the interference signal to allow the radio detector to receive data and locate the drone's position or intercept its control signals.
Small Unmanned Aerial Systems (sUAS) and the Force Protection Threat to DoD[9]
This article discusses the increasing threat posed by small unmanned aerial systems (sUAS) to military forces, particularly the U.S. Department of Defense (DoD). It highlights how enemies are using these drones for surveillance and delivery of explosives.
The Rise of Radar-Based UAV Detection For Military: A Game-Changer in Modern Warfare[3]
This article discusses how radar-based unmanned aerial vehicle (UAV) detection is transforming military operations. SpotterRF’s systems use advanced radar technology to detect drones in all conditions, including darkness or bad weather. By integrating AI, these systems can distinguish between drones and non-threats like birds, improving accuracy and reducing false positives.
Swarm-based counter UAV defense system[10]
This article discusses autonomous systems designed to detect and intercept drones. It emphasizes the use of AI and machine learning to improve the real-time detection, classification, and interception of drones, focusing on autonomous UAVs (dUAVs) that can neutralize threats. The research delves into algorithms and swarm-based defense strategies that optimize how drones are intercepted.
Small Drone Threat Grows More Complex, Deadly as Tech Advances[11]
The article highlights the growing threat of small UAV to military operations. It discusses how these systems are used by enemies for surveillance and direct attacks, and the various countermeasures the U.S. Department of Defense is developing to stop these attacks. It eplores the use of jamming (interference of connection between drone and controller), radio frequency sensing, and mobile detection systems.
US Army invents 40mm grenade that nets bad drones[12]
This article discusses recently developed technology that involves a 40mm grenade that deploys a net to capture and neutralise hostile drones. This system can be fired from a standard grenade launcher, providing a portable, low-cost method of taking down small unmanned aerial systems (sUAS) without causing significant collateral damage.
Making drones to kill civilians: is it ethical?[13]
Usually, anything where harm is done to innocent people is seen as unethical. This would mean that every company which is somehow providing for items in war would do something which is at least partially unethical. However, during war an international law states that a country is not limited by all traditional ethics. This makes deciding on what is ethical and what not harder.
Sociocultural objections to using killer drones against civilians:
- Civilians (not in war) are getting killed by drones since the drones are not able to see the difference between people in war and people not in war
- We should not see war as a ‘clash of civilizations’ as this would induce that civilians are also part of war
Is it ethical to use drones to kill civilians?:
- As said above, an international law applies during war between countries. This law implies:
o Killing civilians = murder = prohibited
- People getting attacked by drones, say that it is not the drones who kill people, but people kill people
A simple solution is to follow the 3 laws of robotics from Isaac Asimov:
- A robot may not injure a human being or allow a human being to come to harm
- A robot must obey orders given to it by human beings except when such orders conflict with the first law
- A robot must protect its own existence, provided such protection does not conflict with the first or second law
But following these laws would be too simple, as these laws are not actual laws
The current drone killer’s rationale:
- A person is targeted only if harmful to the interests of this country so lang as he/she remains alive
This rationale is objected by:
- This rationale is simply assumed since the international law says nothing about random targeting of individuals
This objection is disproved by:
- If the target is not in warzone, it is not harmful to the interests of the country, thus such a person would not be a random person
Is it legal and ethical to produce drones that are used to kill civilians?:
A manufacturer of killer drones may not assume its drones are only being used peacefully.
The manufacturers of killer drones often have cautionary recommendations, which are there to put these manufacturers in a legally safe place.
Conclusion:
The problem is that drone killing is not covered in the traditional war laws. Literature is not uniform in opposition to drone killing, but the majority states that killing civilians is unethical.
Ethics, autonomy, and killer drones: Can machines do right?[14]
The article looks into the ethics of certain weapons used in war (in the US). Since we can view back on new weapons back then in war (like atomic bombs) we can see if what they thought then, is what we think now is ethical. The article uses two different viewpoints to decide the ethics of a war technology, namely teleology and deontology. Teleology is focused on the outcome of an action, while deontology focusses more on the duty of an action.
The article looks first at the atomic bomb, which according to a teleologic viewpoint could be seen as ethical, as it would bring an end to war quickly which saves lives in the long term. Deontology also says it could be ethical since it would show superiority to have such strong weapons, which intimidates other countries in war.
Next up in discussion in a torture program. According to teleology this is an ethical thing to do, since torturing some people, to extract critical information from them could be used to prevent more deaths in the future.
Now the article questions AI-enabled drones. For AI ethics, the AI should always be governed by humans, bias should be reduced (lots of civilians are getting killed now) and there should be more transparency. As for a country this is more challenging since they also have to focusses on safety and winning a war. This is why, in contrast to with the atomic bomb, where teleology and deontology said the same, there now is a contrast between teleology and deontology. Teleology wants to focus on outcome, thus security and protection. Deontology focusses on global values, like human rights. The article says the challenge is to use AI technologies effective while following ethical principles and letting everyone do this.
Survey on anti-dron systems: components, designs, and challenges[15]
Requirements an anti-drone system must have:
- Drone specialized detection (detect the drone)
- Multi drone defensibility (Defend for multiple drones)
- Cooperation with security organizations (Restrictions to functionality should be discussed with public security systems (police/military)
- System portability (lightweight and use wireless networks)
- Non-military neutralization (Don’t use military weapons to defend for drones)
Ways to detect drones:
- Thermal detection (Motors, batteries and internal hardware produce heat)
o Works in all weather
o Affordable
o Not too much range
- RF scanner (capture wireless signals)
o Can’t detect drones what don’t produce RF signals
o Long range
- Radar detection (Detect objects and determine the shape)
o Long range
o Can’t see the drone if it is not moving since it thinks it is an obstacle
- Optical camera detection (detect from a video)
o Short range
o Weather dependant
Hybrid detection systems to detect drones
- Radar + vision
- Multiple RF scanners
- Vision + acoustic
Drone neutralization:
- Hijacking/spoofing (Create fake signal to prevent drone from moving)
- Geofencing (Prevent drone from approaching a certain point)
- Jamming (Stopping radio communication between drone and controller)
- Killer drones (Using drones to damage attacking drones)
- Capture (Physically capture a drone) (for example with a net)
o Terrestrial capture systems (human-held or vehicle-mounted)
o Aerial capture systems (System on defender drones)
Determination of threat level:
- Object
- Flight path
- Available time
(NOTE: The article goes into more depth about some mathematics to determine the threat level, which could be used in our system)
Artificial intelligence, robotics, ethics, and the military: a Canadian perspective[16]
The article not only looks at the ethics, but also the social and legal aspects of using artificial intelligence in the military. For this it looks at 3 main aspects of AI, namely Accountability and Responsibility, Reliability and Trust.
Accountability and Responsibility:
The article states that the accountability and responsibility of the actions of an AI system are for the operator, which is a human. However, when the AI malfunctions it becomes challenging to determine who is accountable.
Reliability:
AI now is not reliable enough and only performs well in very specific situations where it is made for. During military usage you never know in what situation an AI will be in, thus causing a lack in reliability. A verification of AI technologies is necessary, especially when you are dealing with live and death of humans.
Trust:
People who use AI in military should be thought how the AI works and to what extend they can trust the AI. Too much or too little trust in AI can lead to big mistakes. The makers of these AI systems should be more transparent so it can be understood what the AI does.
We need to have a proactive approach to minimize the risks we have with AI. This means that everyone who uses or is related to AI in military should carefully consider the risks that AI brings.
When AI goes to war: Youth opinion, fictional reality and autonomous weapons[17]
The article looks into the responsibilities and risks of fully autonomous robots in war. It does this by asking youth participants about this together with other research and theory.
The article found that the participants felt that humans should be responsible for actions of autonomous robots. This can be supported by theory which says that since robots do not have emotions like humans do, they cannot be responsible for their actions in the same way as humans. If autonomous robots were programmed with some ethics in mind, the robot could in someway be accounted for its actions as well. How this responsibility between humans and robots should be divided became unclear in this article. Some said responsibility was purely for the engineers, designs and government, while others said that the human and robot had a shared responsibility.
The article also found that there were still fears for fully autonomous robots. This came from old myths and social media which say that autonomous robots can turn against humans to destroy them.
As for the legal part of autonomous robots, they can potentially violate laws during war, especially if they are not accounted responsible for their actions. This causes worries for the youth.
The threats that fully autonomous robots bring outweigh the benefits for the youth. This is a sign for the scientific community to further develop and implement norms and regulations in autonomous robots.
Advances and Challenges in Drone Detection and Classification Techniques: A State-of-the-Art Review[18]
Summary:
•The paper provides a comprehensive review of drone detection and classification technologies. It delves into the various methods employed to detect and identify drones, including radar, radio frequency (RF), acoustic, and vision-based systems. Each has their strengths and weaknesses, after which the author discusses 'sensor fusion', where the combination of detection methods lead to improvements of system performance and robustness.
Key takeaways:
•Sensor fusion should be incorporated into system to improve performance and robustness
Counter Drone Technology: A Review[19]
Summary:
•The article provides a comprehensive analysis of current counter-drone technologies and categorizes counter-drone systems into three main groups: detection, identification, and neutralization technologies. Detection technologies include radar, RF detection, etc. Once a drone is detected, it must be identified as friend or foe. The review discusses methods such as machine learning algorithms and signature signal libraries. It covers various neutralization methods, including jamming (RF and GPS), laser-based systems, and kinetic solutions like nets or projectiles, and the challenges each method faces.
Key takeaways:
•Integration of multiple sensor technologies is critical
•Non-kinetic neutralization methods should be prioritized where possible to avoid unintended consequences
A Soft-Kill Reinforcement Learning Counter Unmanned Aerial System (C-UAS) with Accelerated Training[20]
Summary:
•This article discusses the development of a counter-drone system that utilizes reinforcement learning using non-lethal (“soft-kill") techniques. The system is designed to learn and adapt to various environments and drone threats using simulated environments.
Key takeaways:
•C-UAS systems must be rapidly deployable
•C-UAS systems should be trained in simulated environments to improve robustness and adaptability
Terrorist Use of Unmanned Aerial Vehicles: Turkey's Example[21]
Summary:
•The article examines how terrorist organizations have utilized drones for surveillance, intelligence gathering, and attacks. It highlights the growing accessibility of consumer drones, which are repurposed for malicious use and various counter-UAV technologies and tactics employed by Turkish forces to mitigate this threat.
Key takeaways:
•Running costs must be kept minimal. Access to affordable drones is widespread.
•Both kinetic and non-kinetic interception must be available if the system is to be used in urban or otherwise populated environments
Impact-point prediction of trajectory-correction grenade based on perturbation theory[22]
Summary:
•The article discussed trajectory prediction and correction methods for the use case of improving the accuracy of artillery projectiles. By modeling and simulating the effects of small perturbations in projectile flight, the study proposes an impact-point prediction algorithm. While this algorithm can be applied to improving artillery accuracy, it could potentially be used to predict the trajectory and impact location of drone-dropped explosives.
Key takeaways:
•Detailed description of real-time trajectory prediction corrections
•Challenge to balance efficiency with accuracy in path prediction algorithms
Armed Drones and Ethical Policing: Risk, Perception, and the Tele-Present Officer[23]
This paper talks about the tele-officier on ‘unmanned drones’. This paper looks at it from the point of view of attacking, but it can be looked at from the point of view of ‘attacking’ incoming drones where still a person should or should not ‘pull the trigger’ to intercept a drone, with the potential risks of redirecting it at another crowd.
The Ethics and Legal Implications of Military Unmanned Vehicles[24]
This papers states that human soldiers/marines also do not agree on what is ethical warfare. They give a few examples on which questions have controversial answers under the soldiers/marines. (we may use this to argue why/why not our device should be autonomous or not.
Countering the drone threat implications of C-UAS technology for Norway in an EU an NATO context[25]
This paper gives clear insight in different scenarios where drones can be a threat. For example on large crowds but also in warfare. This paper does however not give a concrete solution.
An anti-drone device based on capture technology[26]
This paper explores the capabilities of capturing a drone with a net. It also addresses some other forms of anti drone devices, such as lasers, hijacking, rf jamming…
For the rest is this paper very technical in the net captering.
Four innovative drone interceptors.[27]
This paper states 5 different ways of detecting drones. Acoustic detection and tracking with microphones positioned in a particular grid, video detection by cameras, thermal detection, radar detection and tracking and as last the detection through radio emissions from the drone. Because we want to also be able to catch ‘off-the-shelf’ drones we have to investigate which ones are appropriate. For taking down the drone they give 6 options: missile launch, radio jamming, net throwers, machine guns, lasers, drone interceptors. The 4 drone interceptors they introduce are for us a bit above budget, as they are real drones with various kinds of generators to take down a drone (for example with a high electric pulse), but we could still look into this.
Comparative Analysis of ROS-Unity3D and ROS-Gazebo for Mobile Ground Robot Simulation[6]
This paper examines the use of Unity3D with ROS versus the more traditional ROS-Gazebo for simulating autonomous robots. It compares their architectures, performance in environment creation, resource usage, and accuracy, finding that ROS-Unity3D is better for larger environments and visual simulation, while ROS-Gazebo offers more sensor plugins and is more resource-efficient for small environments.
Interview Preparation
Interview 1: Introductory interview with F.W.
General understanding:
- What types of anti-drone systems are currently used in the military?
- What are key features that make an anti-drone system effective in the field?
- What are the most common types of drones that these systems are designed to counter?
- What are the most common types of drone interception that these systems employ?
- Are there any specific examples of successful or failed anti-drone operations you could share
- DroneShield
- Anduril
Limitation of current systems:
- What are the most significant limitations of current anti-drone systems?
- Are there any specific environments (urban, desert, etc.) where anti-drone systems struggle to perform well?
Cost-related:
- Can you give a rough idea of the costs involved in deploying these systems?
- Purchase cost
- Maintenance cost
- Cost-to-intercept
- What are usual price ranges for systems like these?
- Affordable options
- Full-scale, full-feature systems (military-grade, fully-equipped, etc.)
Ethics discussion:
- Which ethical concerns may be associated with the use of anti-drone systems, particularly regarding urban, civilian areas?
- How does the military handle ethical issues when deploying these technologies?
Potential improvements:
- What improvements do you think are necessary to make anti-drone systems more effective? What are current shortcomings?
- Are there specific threats (related to the build of the drone or other factors) that these systems are weak against?
- Do you think AI or machine learning could help enhance anti-drone systems? To what extent is it currently being used?
Technical questions:
- Is significant training required for personnel to effectively operate anti-drone systems?
- Time required for training
- Infrastructure required for training
- Cost?
- How do these systems usually handle multiple drone threats or swarm attacks?
- Can you explain how systems differentiate between hostile and non-hostile drones?
- How are these systems tested and validated before they are deployed in the field?
Logbook
| Name | Total | Break-down |
|---|---|---|
| Max van Aken | 10h | Attended lecture (2h), Attended meeting with group (2h), Analysed papers/patents [21], [22], [23], [24], [25] (5h), Summarized and described key takeaways for papers /patents [21], [22], [23], [24], [25] (1h) |
| Robert Arnhold | 16h | Attended lecture (2h), Attended meeting with group (2h), Analysed papers/patents [11], [12], [13], [14], [15] (10h), Summarized and described key takeaways for papers/patents [11], [12], [13], [14], [15] (2h) |
| Tim Damen | 16h | Attended lecture (2h), Attended meeting with group (2h), Analysed papers [12], [13], [14], [15], [16] (10h), Summarized and described key takeaways for papers [12], [13], [14], [15], [16] (2h) |
| Ruben Otter | 17h | Attended lecture (2h), Attended meeting with group (2h), Analysed papers/patents [1], [2], [3], [4], [5] (10h), Summarized and described key takeaways for papers/patents [1], [2], [3], [4], [5] (2h), Set up Wiki page (1h) |
| Raul Sanchez Flores | 16h | Attended lecture (2h), Attended meeting with group (2h), Analysed papers/patents [6], [7], [8], [9], [10] (10h), Summarized and described key takeaways for papers/patents [6], [7], [8], [9], [10] (2h), |
| Name | Total | Break-down |
|---|---|---|
| Max van Aken | 13h | Attended lecture (30min), Attended meeting with group (1h), Research kinds of situations of device (2h), wrote about situations (1,5h), research ethics (6h), write ethics (2h) |
| Robert Arnhold | Attended lecture (30min), Attended meeting with group (1h), Worked on interview questions, Organizing introductory interview, Preparing interviews for next weeks | |
| Tim Damen | 13.5h | Attended lecture (30min), Attended meeting with group (1h), Risk evaluation (2h), Important features (1h), Research on ethics of deflection (8h), Writing part about deflection (1h) |
| Ruben Otter | 14.5h | Attended lecture (30min), Attended meeting with group (1h), Analysed papers [2], [3], [4], [5] for research in drone detection (6h), Wrote about drone detection and its relation to our system using papers [2], [3], [4], [5] (4h), Analysed and summarized paper [6] (2h), Wrote about usage of simulation and its software (1h) |
| Raul Sanchez Flores | Attended lecture (30min), Attended meeting with group (1h) |
References
- ↑ How to read a risk matrix used in a risk analysis (assessor.com.au)
- ↑ 2.00 2.01 2.02 2.03 2.04 2.05 2.06 2.07 2.08 2.09 2.10 2.11 Chiper F-L, Martian A, Vladeanu C, Marghescu I, Craciunescu R, Fratu O. Drone Detection and Defense Systems: Survey and a Software-Defined Radio-Based Solution. Sensors. 2022; 22(4):1453. https://doi.org/10.3390/s22041453
- ↑ 3.00 3.01 3.02 3.03 3.04 3.05 3.06 3.07 3.08 3.09 3.10 3.11 The rise of Radar-Based UAV Detection for Military: A Game-Changer in Modern Warfare. (2024, June 11). Spotter Global. https://www.spotterglobal.com/blog/spotter-blog-3/the-rise-of-radar-based-uav-detection-for-military-a-game-changer-in-modern-warfare-8
- ↑ 4.00 4.01 4.02 4.03 4.04 4.05 4.06 4.07 4.08 4.09 4.10 4.11 4.12 4.13 4.14 4.15 4.16 4.17 4.18 4.19 4.20 4.21 4.22 4.23 4.24 4.25 4.26 4.27 4.28 4.29 4.30 4.31 4.32 4.33 4.34 4.35 4.36 Seidaliyeva U, Ilipbayeva L, Taissariyeva K, Smailov N, Matson ET. Advances and Challenges in Drone Detection and Classification Techniques: A State-of-the-Art Review. Sensors. 2024; 24(1):125. https://doi.org/10.3390/s24010125
- ↑ 5.0 5.1 5.2 5.3 5.4 Caballero-Martin D, Lopez-Guede JM, Estevez J, Graña M. Artificial Intelligence Applied to Drone Control: A State of the Art. Drones. 2024; 8(7):296. https://doi.org/10.3390/drones8070296
- ↑ 6.0 6.1 6.2 6.3 Platt, J., Ricks, K. Comparative Analysis of ROS-Unity3D and ROS-Gazebo for Mobile Ground Robot Simulation. J Intell Robot Syst 106, 80 (2022). https://doi.org/10.1007/s10846-022-01766-2
- ↑ Willy, Enock, Autonomous Weapons Systems and International Humanitarian Law: Need for Expansion or Not (NOVEMBER 16, 2020). Available at SSRN: https://ssrn.com/abstract=3867978 or http://dx.doi.org/10.2139/ssrn.3867978
- ↑ Chmielus, T. (2024). Drone defense system (U.S. Patent No. 11,876,611). United States Patent and Trademark Office. https://patentsgazette.uspto.gov/week03/OG/html/1518-3/US11876611-20240116.html
- ↑ Kovacs, A. (2024, February 1). Small Unmanned aerial Systems (SUAS) and the force protection threat to DOD. RMC. https://rmcglobal.com/small-unmanned-aerial-systems-suas-and-the-force-protection-threat-to-dod/
- ↑ Brust, M. R., Danoy, G., Stolfi, D. H., & Bouvry, P. (2021). Swarm-based counter UAV defense system. Discover Internet of Things, 1(1). https://doi.org/10.1007/s43926-021-00002-x
- ↑ Small drone threat grows more complex, deadly as tech advances. (n.d.). https://www.nationaldefensemagazine.org/articles/2023/8/30/small-drone-threat-grows-more-complex-deadly-as-tech-advances
- ↑ Technology for innovative entrepreneurs & businesses | TechLink. (n.d.). https://techlinkcenter.org/news/us-army-invents-40mm-grenade-that-nets-bad-drones
- ↑ Making Drones to Kill Civilians: Is it Ethical? | Journal of Business Ethics (springer.com)
- ↑ Full article: Ethics, autonomy, and killer drones: Can machines do right? (tandfonline.com)
- ↑ IEEE Xplore Full-Text PDF:
- ↑ https://ojs.aaai.org/aimagazine/index.php/aimagazine/article/view/2848
- ↑ When AI goes to war: Youth opinion, fictional reality and autonomous weapons - ScienceDirect
- ↑ Seidaliyeva, U., Ilipbayeva, L., Taissariyeva, K., Smailov, N., & Matson, E. T. (2024). Advances and Challenges in Drone Detection and Classification Techniques: A State-of-the-Art Review. Sensors, 24(1), 125. https://doi.org/10.3390/s24010125
- ↑ Gonzalez-Jorge, Higinio & Aldao, Enrique & Fontenla-Carrera, Gabriel & Veiga Lopez, Fernando & Balvís, Eduardo & Ríos-Otero, Eduardo. (2024). Counter Drone Technology: A Review. 10.20944/preprints202402.0551.v1.
- ↑ Silva, Douglas & Machado, R. & Coutinho, Olympio & Antreich, Felix. (2023). A Soft-Kill Reinforcement Learning Counter Unmanned Aerial System (C-UAS) with Accelerated Training. IEEE Access. PP. 1-1. 10.1109/ACCESS.2023.3253481.
- ↑ Şen, Osman & Akarslan, Hüseyin. (2020). Terrorist Use of Unmanned Aerial Vehicles: Turkey's Example.
- ↑ Wang, Yu & Song, W.-D & Song, X.-E & Zhang, X.-Q. (2015). Impact-point prediction of trajectory-correction grenade based on perturbation theory. 27. 18-23.
- ↑ Armed Drones and Ethical Policing: Risk, Perception, and the Tele-Present Officer https://www.ncbi.nlm.nih.gov/pmc/articles/PMC8367046/ Published online 2021 Jun 19. doi: 10.1080/0731129X.2021.1943844
- ↑ The Ethics and Legal Implications of Military Unmanned Vehicles,y Elizabeth Quintana, Head of Military Technology & Information Studies Royal United Services Institute for Defence and Security Studies https://static.rusi.org/assets/RUSI_ethics.pdf
- ↑ Countering the drone threat implications of C-UAS technology for Norway in an EU an NATO context https://www.researchgate.net/profile/Bruno-Martins-4/publication/348189950_Countering_the_Drone_Threat_Implications_of_C-UAS_technology_for_Norway_in_an_EU_and_NATO_context/links/5ff3240492851c13feeb0e08/Countering-the-Drone-Threat-Implications-of-C-UAS-technology-for-Norway-in-an-EU-and-NATO-context.pdf
- ↑ An anti-drone device based on capture technology Yingzi Chen, Zhiqing Li, Longchuan Li, Shugen Ma, Fuchun Zhang, Chao Fan, https://doi.org/10.1016/j.birob.2022.100060 https://www.sciencedirect.com/science/article/pii/S2667379722000237
- ↑ Four innovative drone interceptors. Svetoslav ZabunovB, Garo Mardirossian,https://doi.org/10.7546/CRABS.2024.02.09