PRE2019 4 Group10: Difference between revisions
TUe\20181442 (talk | contribs) |
|||
| (63 intermediate revisions by 4 users not shown) | |||
| Line 18: | Line 18: | ||
! Study | ! Study | ||
|- | |- | ||
| Ezra Leeuwenhage || | | Ezra Leeuwenhage || 1313568 || Computer Science and Engineering | ||
|- | |- | ||
| Paulien Teuwen || 1337904 || Industrial Design | | Paulien Teuwen || 1337904 || Industrial Design | ||
|- | |- | ||
| Yorn Thijssen || | | Yorn Thijssen || 1342320|| Industrial Design | ||
|- | |- | ||
| Ries van de Ven || | | Ries van de Ven || 1318578 || Industrial Design | ||
|- | |- | ||
| Kim Wintraecken || | | Kim Wintraecken || 1322842 || Industrial Design | ||
|} | |} | ||
==Problem statement and objectives== | ==Problem statement and objectives== | ||
The issue capturing global attention in recent months is the Covid-19 pandemic, causing great disruption throughout the world in both in terms of health care and economy. Many governments have since the outbreak opted for an approach to combat the virus through limiting all social interactions within society (commonly referred to as a lockdown), putting a halt to its spread at the cost of national economy. In the long term this approach is not sustainable however, leading to the need to find ways to reduce restriction on social interaction in all aspects of society without losing grip of the spread of the virus. To this end, the Dutch government has suggested the nation-wide employment of an application designed to predict/ detect infection with Covid-19 of civilians, enabling them to accurately manage the virus’s impact on society without the need for a type of lockdown. The need for such an app is still being questioned, since it brings a lot of difficulties with it, regarding the violation of the Dutch privacy legislation. | |||
However, there would be no need to check all social implications in detail, if such an app is simply not efficient enough to contribute to the curbing of the virus. Since in this scenario, it would be fruitless to implement such an app. This project will shed light on the requirements that need to be met, to make the app efficient enough to combat the Covid-19 pandemic. | However, there would be no need to check all social implications in detail, if such an app is simply not efficient enough to contribute to the curbing of the virus. Since in this scenario, it would be fruitless to implement such an app. This project will shed light on the requirements that need to be met, to make the app efficient enough to combat the Covid-19 pandemic. | ||
The objectives of this project will be to determine through literary research what the relevant requirements are to the problem and what exactly the desired effectiveness of the application is in order to meet its requirements. Finally, the objective of practical research done thereafter will be to determine what type of implementation of the app satisfies the requirements set by the results from literary research. | The objectives of this project will be to determine through literary research what the relevant requirements are to the problem and what exactly the desired effectiveness of the application is in order to meet its requirements. Finally, the objective of practical research done thereafter will be to determine what type of implementation of the app satisfies the requirements set by the results from literary research. | ||
The results of the project can be found under week 9 of the section 'progress per week'. | |||
===Who are the users?=== | ===Who are the users?=== | ||
| Line 78: | Line 80: | ||
==Approach== | ==Approach== | ||
Solving the problem around the corona app has a difficult set of objectives: first the group should evaluate the existing research about the corona app and the current simulations that exist regarding the efficiency of such an app. Next, different simulations must be compared | Solving the problem around the corona app has a difficult set of objectives: first, the group should evaluate the existing research about the corona app and the current simulations that exist regarding the efficiency of such an app. Next, different simulations must be compared and analyzed to specify a list of requirements and parameters. Also, recommendations will be given about the implementation of technology, and app developers of corona apps were contacted. | ||
These results should confirm or deny earlier research and the goal is to determine if a corona app would be suitable to achieve the combat of the virus. | |||
==Milestones== | ==Milestones== | ||
A certain milestone is | A certain milestone is gathering all the research needed. another milestone is the comparison of the simulation models. | ||
===Week number: Tasks=== | ===Week number: Tasks=== | ||
| Line 92: | Line 93: | ||
|- | |- | ||
| Week 1: | | Week 1: | ||
| | | gathering research | ||
|- | |- | ||
| Week 2: | | Week 2: | ||
| | | gathering research | ||
|- | |- | ||
| Week 3: | | Week 3: | ||
| | | gathering research | ||
|- | |- | ||
| Week 4: | | Week 4: | ||
| | | compare models and contact app developers | ||
|- | |- | ||
| Week 5: | | Week 5: | ||
| | | analyze models and analyze interviews app developers | ||
|- | |- | ||
| Week 6: | | Week 6: | ||
| | | paper writing | ||
|- | |- | ||
| Week 7: | | Week 7: | ||
| | | paper writing | ||
|- | |- | ||
| Week 8: | | Week 8: | ||
| Final presentation and demo (recorded video) | | paper writing, Final presentation, and demo (recorded video) | ||
|} | |} | ||
| Line 122: | Line 123: | ||
===Who is doing what?=== | ===Who is doing what?=== | ||
To create a full detailed planning for the | To create a full detailed planning for the whole course is difficult, especially in situations like these where we do not know what we are capable of and things can change every week. Therefore, we have chosen to divided tasks after each meeting or every week just like in an OGO project. These assigned tasks will be published weekly on the wiki in a table. However, to keep track of the schedule, some team members will be assigned to have a leading role over a part of the project. | ||
| Line 131: | Line 132: | ||
Monday - 09:30 | Monday - 09:30 | ||
Thursday - before after tutoring session | |||
==== | ==== Chairman Minute taker ==== | ||
{| border=1 style="border-collapse: collapse;" | {| border=1 style="border-collapse: collapse;" | ||
! Date | ! Date | ||
| Line 174: | Line 175: | ||
====Weekly hours==== | ====Weekly hours==== | ||
[[File: | [[File:hours&breakdown.pdf]] | ||
=Progress per Week= | =Progress per Week= | ||
==Week 1== | ==Week 1== | ||
During the first week of the project, a decision had to be made on what the subject of our study would be. All group members brainstormed about these ideas and offered several project ideas. Lists of ideas, as well as a mural, were made. (for a more in-depth view of those ideas and the mural, see file: .. | During the first week of the project, a decision had to be made on what the subject of our study would be. All group members brainstormed about these ideas and offered several project ideas. Lists of ideas, as well as a mural, were made. (for a more in-depth view of those ideas and the mural, see file: [[File: Brainstorm_week_1.pdf]], [[File:Mural_week_1.pdf]]) The main suggestions that came out of this session and were considered in this first week were: a healthcare robot, a gardening tool, facial recognition with emotions, or a literature study to already existing technology. | ||
Regarding the situation at hand (the COVID-19 pandemic), we thought it would be interesting to research the current state of the so-called Corona Apps. Our initial plan was to create 2 apps that functioned in a different perspective. one out of the value of efficiency, one out of the value of privacy. Later on, this plan would change, but during week 1 and 2, the first general research was done regarding these apps. | Regarding the situation at hand (the COVID-19 pandemic), we thought it would be interesting to research the current state of the so-called Corona Apps. Our initial plan was to create 2 apps that functioned in a different perspective. one out of the value of efficiency, one out of the value of privacy. Later on, this plan would change, but during week 1 and 2, the first general research was done regarding these apps. | ||
| Line 213: | Line 214: | ||
==Week 4== | ==Week 4== | ||
During the 4th week, app developers were contacted to gain more information regarding the app simulations. (more info can be found in [[File:Antwoorden_app_developers.pdf]] | |||
Furthermore, other simulations were looked at during this period. These include the Simulation of Delft, ASSOCC. | |||
[[File:hw_kim_simulation_simulation_delft.pdf]] | [[File:hw_kim_simulation_simulation_delft.pdf]] | ||
==Week 5== | |||
During week 5, the last efforts for information gathering were made, before we started to write the paper. This included findings regarding contact tracing, covid-19 models, Bluetooth, ... More information on these topics can be found in this Wiki, at Research per Topic. | |||
==Week 6== | |||
In week 6 we redefined why we want to use Bluetooth; wrote the first parts of the report that will be the end deliverable such as related works etc; and finished the contacting people. | |||
===Paper=== | |||
[[File: Wiki_bestand_paper.pdf]] | |||
==Week 7== | |||
This week, everyone has been working on the content of the research paper. Everyone is gathering information from the related works and using this to critique certain decisions of other applications and simulations. We compare applications and simulations in order to find the best solution for each part of the application in order to reach the highest effectivity. | |||
We will be organising the wiki page as of next week. Next to that, we will start working on the presentation for the course and keep on updating the research paper. | |||
What work has been done: | |||
- Reasoning for why Bluetooth is the best possible option for proximity tracing and how this can be improved [INCLUDED IN PAPER] | |||
- Simulation models are being critiqued and compared in order to draw valuable conclusions on what is missing or what is very useful and makes it an effective simulation. [NOT ADDED TO PAPER YET] | |||
- Related works of state of the art applications, critique on them and finding values within the apps. [NOT ADDED TO PAPER YET] | |||
- Referencing every piece of work of others correctly, refining the pieces of text in the related works and adding all the pieces of text to the paper. | |||
- Formulating which approach to use: decentralised or centralised and why. [NOT ADDED TO PAPER YET BUT BELOW IN WIKI PAGE] | |||
==Week 5== | ===Paper=== | ||
Paper (work in progress) : [[File:Wiki_bestand_paper_v2.pdf]] | |||
==Week 8== | |||
Last efforts regarding the paper were made, before a feedback session with the tutor of this course | |||
===Paper=== | |||
paper in progress (as of 9th of June 2020) | |||
[[File:Wiki_bestand_paper_v3.pdf]] | |||
==Week 9 and Deliverables== | |||
During this week, the paper was finalized | |||
'''The final version of the research paper can be found here:''' | |||
[[File:Final_version_paper.pdf]] | |||
'''The link to the video presentation can be found here:''' | |||
[https://www.youtube.com/watch?v=qazIig4W7F4] | |||
'''The peer review as done by the group can be found here:''' | |||
[[File:Peer_review.pdf]] | |||
(keep in mind that a part of the table can be found on the second page) | |||
'''This results in the following adjustments to grades:''' | |||
{| border=1 style="border-collapse: collapse; width: 30%; height: 14em;" | |||
! Name | |||
! Adjustment | |||
|- | |||
| Ezra Leeuwenhage || -1 | |||
|- | |||
| Paulien Teuwen || 0 | |||
|- | |||
| Yorn Thijssen || 0 | |||
|- | |||
| Ries van de Ven || +0.5 | |||
|- | |||
| Kim Wintraecken || +0.5 | |||
|} | |||
=Research per topic= | |||
==App developers== | |||
In this research several models and simulations about the effectiveness of a corona app are investigated and studied. Before the idea of implementing such a track and trace corona app these kinds of simulations were not available yet, so there could not really be stated anything about the effectiveness of such an app. But even though this was not known, app developers already started with bringing ideas about how they could help with an app during this crisis. | |||
On the 11th of April the Dutch government made a call for companies and experts to think about the development of apps in the approach against corona virus. This proposal had to be in of three categories: | |||
*An app that to determines contact between people and notifies when a user was in contact with an infected person. | |||
*An app that makes it easier to have contact with a doctor from home. | |||
*Any other ideas of an app that could help in the fight against corona. | |||
These companies and experts could submit a proposal until Tuesday 14th of April, 12:00. In total there were more than 750 proposals submitted. Eventually 7 teams were chosen to take part in an ‘Appathon’, a digital event to test and improve the working of these corona apps. According to experts, the apps of these 7 teams best match the approach of the Municipal Health Services (GGD) for doing source and contact research, while at the same time meeting requirements that are set in areas such as privacy, data and information security and ease of use. | |||
All seven teams have been contacted for this research to interview them with questions about their approach and if and how they simulated the effectiveness of their app. Not all seven initiatives responded but the ones that did gave very interesting insights and even provided new research. A summary of each interview is given below. | |||
===The DEUS initiative === | |||
The DEUS initiative explores and builds AI services to create a positive impact on our future. They combine data, design and artificial intelligence to solve challenging problems elegantly, ethically and efficiently. | |||
Before the call of the government, Deus was already brainstorming about how they could help during this pandemic. When the opportunity of coming with this proposal was there, the whole team threw themselves into this. Because of the three categories in which they could submit their proposal in, the team thought of a wide range of technological possibilities (even using WhatsApp for having easier contact on distance). Specifically for the track and trace app, the team performed a technical audit to analyze worldwide existing solutions. The result of this audit was that they proposed the open source DP-3T protocol which has one major benefit: privacy is guaranteed. The protocol does not save personal information neither does it track location. This criteria for privacy was the most important aspect for proposing this protocol. However, this benefit is at the same time a big disadvantage because the GGD would want to know this information. Another important aspect in proposing this protocol is the fact that it is open source. Deus thinks when it is developed by a community it can eventually be developed to a European Standard of a track and trace app. | |||
During the ‘appathon’ Deus showed how a Dutch version of an application with use of the DP-3T protocol would look and work. The application exchanges a digital handshake with use of Bluetooth. It does so when a user has been within a particular distance for a particular time. This distance and time would be determined by the GGD which has a vision about when risk of contamination is higher. The handshakes would be saved and when a user would be tested positive with the disease, this user gets a code from the GGD and enters this in the application. The app then notifies all the other users who saves a ‘handshake’ with this user in the last 10 or 14 days. | |||
This app would support or automate the way the contact research is done now. Currently, when someone is tested positive, he or she will sit down with someone from the GGD and will make an excel sheet with all the people with whom you remember you have been in contact with in the last 14 days, together with their e-mail and phone numbers. The app would reduce work pressure. | |||
Unfortunately, The DEUS team does not have tested their app on effectiveness, simply because there was no time for that. | |||
===ITO=== | |||
Ito is a team of individuals with varied experience who are forming a global alliance of privacy-focused open source projects working on decentralized tracing solution, for example for a tracing corona app. The goal of Ito is to create a unanimous privacy-protecting protocol that different countries and institutions can build their contact tracing apps on. They work entirely voluntarily. The team is built up by several teams that participated in the Appathon/Hackathon in Germany. | |||
Unfortunately for Ito, the German government ignored any suggestion of tracing apps and therefore also the Ito team. The Ito team saw this as motivation to show that it can be done better. On the moment of writing, the Ito team has not yet reached their goal. Things are continuously changing and they adjust towards this. However, they do have a working android app but it is not secure yet. | |||
The app works with the TCN (Temporary Contact Numbers) protocol. It is very similar to the DP-3T protocol and also works with Bluetooth and handshakes. They have to work on privacy, and eventually want to have a free software alternative for the google and apple framework. | |||
Within their goal it is clear what their most important value is in developing this app. Privacy. The team wants to reach this by i.a. making everything as transparent as possible. Everything is posted online, from research to source code. Even their meetings which take place every 2 days, and their notes can be viewed back. | |||
Ito works in collaboration with the technical university of Munich. At this university, some physicists and Mathematicians work on simulations and models. These simulations are not tight to the app, but rely on variables. It for instance tells how many people would need to download the app to have effect. | |||
==Contact tracing== | |||
=== Effectivness of Contact Tracing === | |||
Knowing when contact tracing is effective is of great importance. The probability of detecting every individual contact of an infected person is therefore composed of two factors [1]: | Knowing when contact tracing is effective is of great importance. The probability of detecting every individual contact of an infected person is therefore composed of two factors [1]: | ||
| Line 271: | Line 387: | ||
[6] Becker, N. G., Glass, K., Li, Z., & Aldis, G. K. (2005). Controlling emerging infectious diseases like SARS. Mathematical biosciences, 193(2), 205-221. DOI: https://doi.org/10.1016/j.mbs.2004.07.006 | [6] Becker, N. G., Glass, K., Li, Z., & Aldis, G. K. (2005). Controlling emerging infectious diseases like SARS. Mathematical biosciences, 193(2), 205-221. DOI: https://doi.org/10.1016/j.mbs.2004.07.006 | ||
===Digital Contact Tracing Service === | |||
The paper focusses on verifying and improving the impact of tracking based on epidemiological models. It hereby presents an improved decentralized, privacy preserving approach of a digital contact tracing service. This tracing of infectious contacts, digital or not, is an epidemiological tool which will only work and be effective if coupled with the ability to test potentially infected people quickly. | The paper focusses on verifying and improving the impact of tracking based on epidemiological models. It hereby presents an improved decentralized, privacy preserving approach of a digital contact tracing service. This tracing of infectious contacts, digital or not, is an epidemiological tool which will only work and be effective if coupled with the ability to test potentially infected people quickly. | ||
| Line 335: | Line 451: | ||
[4] ContacTUM consortium, Digital contact tracing and its impact on the sars-cov-2 pandemics, tba, work in progress (2020). | [4] ContacTUM consortium, Digital contact tracing and its impact on the sars-cov-2 pandemics, tba, work in progress (2020). | ||
=== | ===Interventions=== | ||
====passive interventions ==== | |||
passive interventions = those which do not involve testing or contact tracing. | |||
* Hospitalization: | |||
**Patient stops interacting with household and workplace networks | |||
**Reduction of number of random interactions | |||
**Don’t model interactions within hospitals (this is planned for future work) | |||
*Self-quarantine upon symptoms: | |||
**Stopping interactions on the individual's workplace network | |||
**Reducing their number of interactions on the random network | |||
**Option: everybody in household will be asked to self-quarantine | |||
*Lock-down: | |||
**Reducing number of contact that people have | |||
**Reducing number of interactions that people have by 80% on work-place and random networks | |||
**Increase transmission rate for interactions on the household network | |||
*Shield group: fatality rate is highly skewed towards the over 70s – applying a lock-down just to this demographic group | |||
**Reducing number of contact that people have | |||
**interactions on the household network are not increased | |||
Insert picture table 7 with text: Table 7. Proportion of people in each stage of illness whose disease progresses further; mean and standard deviation for density functions of the times that each transition { disease progression or recovery { takes. Parameter values match the OpenABM-Covid19 baseline parameters, April 28, 2020 | |||
Insert table 8 with text: Table 8. Parameters corresponding to passive interventions (hospitalization and self-quarantine upon symptoms). Parameter values match the OpenABMCovid19 baseline parameters, April 28, 2020 | |||
=== | ====Active interventions ==== | ||
= | Active interventions = involve contact tracing or testing | ||
3 events in the ABM which can be the initial trigger for an active intervention: | |||
*Developing symptoms (true covid-19 or not) in the community | |||
*Testing positive for covid-19 | |||
*Hospitalization (clinical diagnosis alone, or combined with a positive test result) | |||
3 types of active intervention which can be triggered: | |||
*Testing for covid-19 infection: | |||
**delays in the testing procedure between ordering and taking a test, and then getting results are modelled | |||
* | *Self-quarantining: | ||
**stopping interactions on the individual's workplace network | |||
**reducing their number of interactions on the random network | |||
*Digital contact tracing: app-based contact tracing | |||
====Implementation details ==== | |||
* Events: an event-based system is used to drive disease progression in individuals and interventions. At each decision point it is calculated when the next event will occur and it is added to an event list for that day. For each type of event, there is an eventlist structure which contains an array of linked lists for each day of the simulation. | |||
*Individuals: each person in the population is represented by an individual structure and the population is static. It contains the following information: | |||
**Demographic: age, house number, network membership | |||
**Interaction diary: list of all interactions over a period of days | |||
**Disease: current status and pointers to both current and future disease events | |||
**Quarantine: the person is currently quarantined, and pointers to that event and the release moment | |||
*Network Construction: Each interaction network has an associated network structure which contains an array of edges | |||
**Can be static, static but down-sampled or dynamic | |||
**Modular at any network | |||
*Transmission: transmitting the pathogen across today's interaction network, which is done as a push from all infected people (by disease status). | |||
**For every infection status the transmission rate for someone who has been infected for that length of time is pre-calculated | |||
**At each time-step go through all the interactions the infected person had for that day and calculate whether transmission has occurred | |||
**each individual gets a quantity of hazard at the start of the simulation | |||
= | **hazard < 0 = infected | ||
** insert formula here | |||
When | * Digital Tracing and Release: When an individual self-reports symptoms or tests positive, they become an index case and are assigned an index token | ||
**Digital tracing: performed by looping through all contacts in the interaction diary and if the app recorded the interaction a quarantine message is sent along with the index token | |||
**Individuals store this for 14 days | |||
**Negative test: individuals receive message to remove index token | |||
**Released from quarantine if token is removed | |||
*Performance: | |||
**96% of CPU usage: rebuilding daily interaction networks and updating the individual’s interaction diaries | |||
**60% of memory usage: storing the interaction diaries | |||
**20% of memory usage: storing the semi-static networks | |||
* | **20% of memory usage: storing individuals and their states in event list | ||
[1] Dignum, F. (2020). Exit Strategieën [Slides]. Retrieved from https://simassocc.files.wordpress.com/2020/04/nlexitstrategies-190420-1.pdf | |||
[2] Hinch, R., Probert, W., Nurtay, A., Kendall, M., Wymant, C., Hall, M., Lythgoe, K., Cruz, A. B., Zhao, L., STEWART, A., FERRETTI, L., ABELER-DORNER, L., BONSALL, D., & FRASER, C. (2020). COVID-19 AGENT-BASED MODEL WITH INSTANTANEOUS CONTRACT TRACING. BIG DATA INSTITUTE, NUFFIELD DEPARTMENT OF MEDICINE, UNIVERSITY OF OXFORD | |||
==ASSOCC== | |||
===Analysis simulation model Delft ASSOCC=== | |||
The ASSOCC model (Agent-based Social Simulation for the COVID-19 Crisis), is a model that has specifically been designed and implemented by European researchers from Umeå University, TU Delft, Malmö University, Utrecht University, Caen University and Stockholm University to address the societal challenges of the COVID-19 pandemic. | |||
'''What exactly is it?''' | |||
both | This model uses “corona in Simcity” approach to ''study individual and social reactions to the containment policies.'' It is a tool for decision makers to ''explore different scenarios and their effects''. It is not a model to ''generate predictions''. It simulates the behavior of a synthetic population given a set of policies (for example when in a lock-down or voluntary isolation). It enables to study the effects on both the spread of the contagion and on how people can be expected to react to the policies (e.g. potential violations or workarounds). | ||
'''What answers does it provide?''' | |||
It models both the ''possible effects on the spread of the coronavirus'' and the ''socio-economic effects'' of the policies, providing possible answers to: | |||
• How might policies based on achieving drastic behavioral change go ''wrong''? | |||
• How might one ''work with existing social norms and habits'' to effectively limit virus spread (what will work with populations and what will not?) | |||
• How might we ''reintroduce people'' who have recovered from the disease back into society to help others and revive the economy without this leading to ''social division'' and a general breakdown of social distancing? | |||
• What are the possible dangers of ''social polarization'' between vulnerable older people and the young who want to get together, how might we keep younger people “on board”, how might we stop them losing contact with other generations? | |||
• For particular groups within societies, at particular times of year or day are there safe gathering ''activities with very low risk of contagion''? Are there practices that are particularly dangerous. | |||
• What ''new social practices'' might we develop that allow life in a world susceptible to waves of new infection (e.g. red and blue teams in hospital so there is no overlap)? | |||
• ''Timing and consequences'' of lifting the restrictions | |||
'''How does it work? ''' | |||
ASSOCC is made in ''NetLogo''. It is based on a set of ''artificial individuals, each with given needs, demographic characters, and attitude towards regulations and risks''. All the agents decide each time what they should be doing and because of this, many different possible effect of policies can be analyzed. | |||
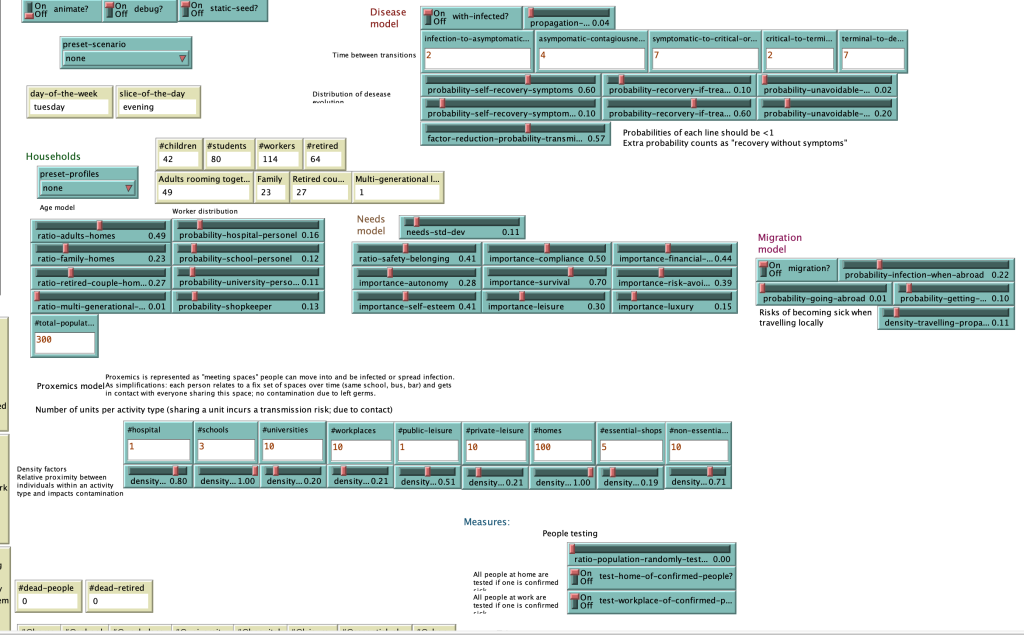
[[File:parameter.png]] | |||
This figure is a screenshot of the parameter setting in the NetLogo model. (ASSOCC, 2020) | |||
More information about what each parameter means can be found in the pdf: “Hw Kim simulation delft’. | |||
The framework is based on the fact that individuals have to balance their needs over many ''contexts''. | |||
The following image shows how people manage this balancing act in their daily life: | |||
[[File:balancing of needs.png]] | |||
More information about this image can be found in the pdf: 'Hw Kim simulation delft’. | |||
'''Agents selecting an action:''' | |||
1. an agent creates a ''list of all possible places'' (gathering-points) it can go with different motivations = an action | |||
this list is based on their current age, time of day, day in week, parameters set in the model | |||
2. for all these actions, the global ''expected effect'' on the needs is calculated | |||
(summing over the expected effects x the desire for each main need) | |||
3. the action that satisfied the ''highest number of needs'' is selected to be acted upon | |||
after all agents have moved to the location where they want to execute their action, the actions get executed, and the needs get updated | |||
'''Track and trace apps''' | |||
ASSOCC has looked at the policy of implementing the ‘corona app’ into society. In their scenario, they assumed a perfect app aligned with all functional, legal and ethical requirements. They studied the effectiveness of such an app by performing 3 experiments: | |||
1. The effect of the app depending on ''different percentages of the population using the app'' | |||
2. Comparing the effect of using the app with that of ''random testing'' a percentage of the population | |||
3. Effect of the app depending on the ''characteristics'' of the users (percentage of risk-avoiding agents that use that app) | |||
The following conditions were used: | |||
• Percentage of app users = (0%, 60%, 80% or 100%) | |||
• Percentage of app users = 0.0 and percentage of population tested randomly daily = (0% or 20%) | |||
• Percentage of app users = 60% and percentage of risk avoidance app users = (0%, 30% or 60%) | |||
'''Results | |||
Experiment 1: Differing amounts of population using the app''' | |||
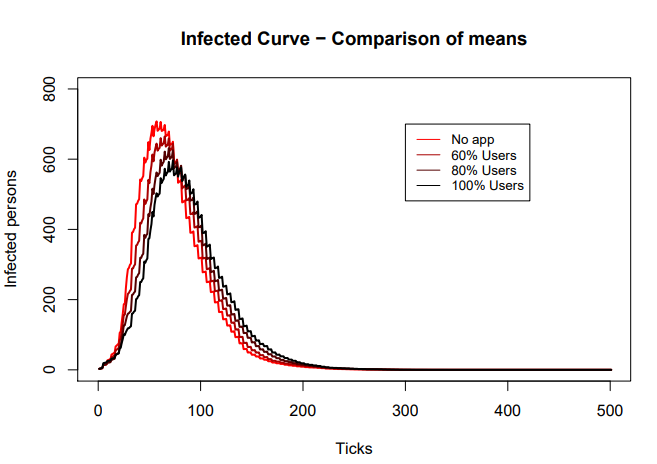
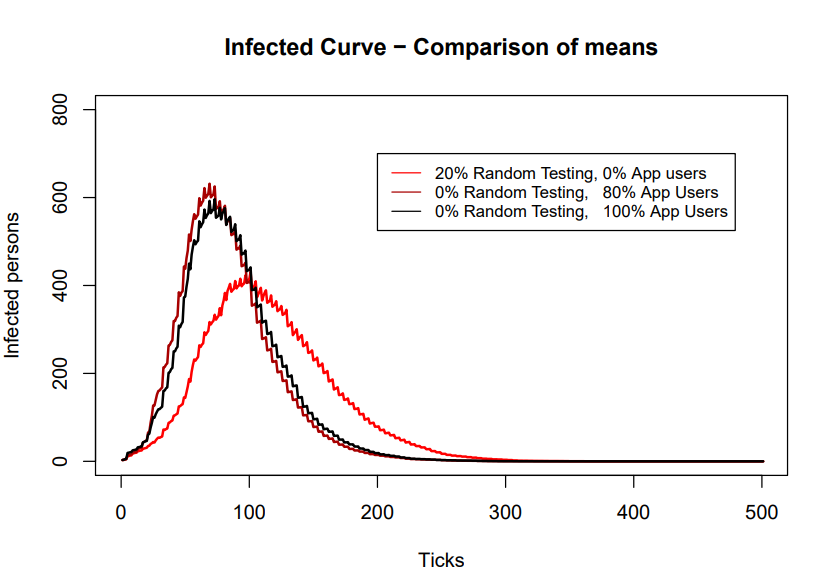
According to ASSOCC, using the app results in a lower infection peak. However, the differences are not significant in a test using 15 randomised runs for each setting, as depicted in curve1.png comparing the settings for no app users, 60% app users, 80% app users and 100% app users, with a population of 1000 agents. | |||
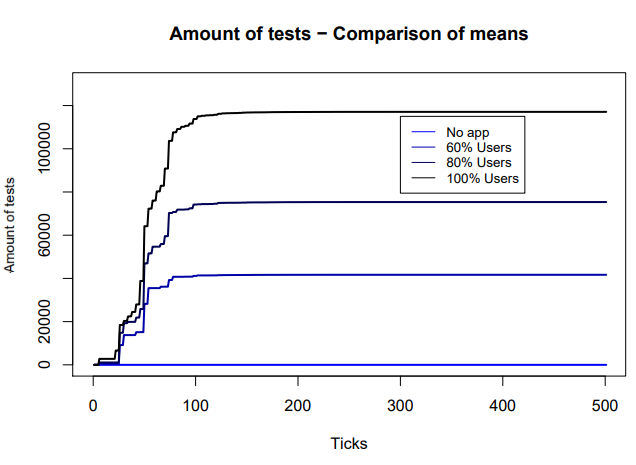
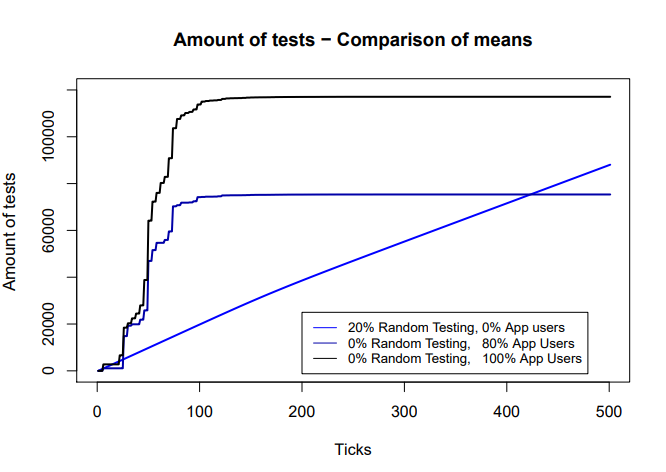
However, as depicted in curve2.png, increasing the number of users results in a sharp increase of testing given that all those that are alerted of being in contact with an infected agent will need to be tested (or required to quarantine themselves). | |||
These results left ASSOCC with the question how does the usage of the app compare with a similar amount of random testing. This gave the basis for experiment 2. | |||
[[File:curve1.png]] | |||
[[File:curve2.png]] | |||
'''Experiment 2: comparing tests performed through app with random testing''' | |||
According to ASSOCC, random testing raises infection awareness even when the tested agent had no reason to suspect infection. The differences on number of infected agents under different conditions is shown if curve3.png | |||
[[File:curve3.png]] | |||
[[File:curve4.png]] | |||
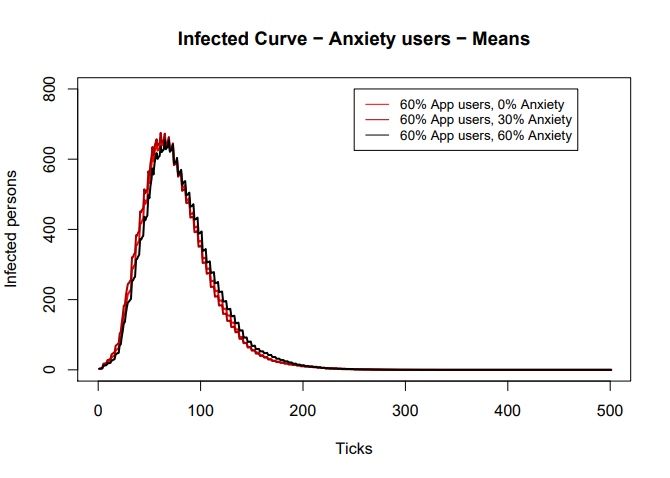
'''Experiment 3: effect of the type of app users.''' | |||
Next, ASSOCC hypothesized that the people who are most likely to use the app are probably those that are more risk averse. However, in initial tests, they were not able to see a significant difference under this condition. | |||
[[File:curve5.png]] | |||
'''Conclusion: ''' | |||
The effectiveness of tracking and tracing apps on lowering the number of infected agents is limited and lower than that of random testing. The use of the app results in a sharp increase on the number of agents that need to be tested, which may be above the capacity available in the system. | |||
''ASSOCC therefore concludes from this data that the app (with around 60% use) makes no significant contribution to a virus-free Netherlands.'' | |||
Results show that by themselves these apps have none or minimal effect on the spread of the virus. Besides all legal, constitutional and ethical issues, their use may lead to a false feeling of security which ultimately can contribute to a second wave of the contagion [3]. | |||
Other studies, based on large scale mathematical models of epidemics show the opposite effect. I.e. according to those studies, track and trace apps do have a positive effect on the containment of the virus [3]. | |||
''It is important to compare these types of studies and see why they lead to different results.'' | |||
The major difference between the ASSOCC model and those used by many epidemiologists is that ASSOCC has a simulation based on human behavior which is used together with the epidemiological model [3]. | |||
The important difference between ASSOCC model and other models, lies in a number of specific properties of the corona virus: | |||
1. The time between becoming infected and possibly showing symptoms is quite long. In an epidemiological model, this is translated by giving a parameter a different value. However, when looking at how many interactions people have, and with which other people, probabilistic model in a mathematical model can be used that divides the interactions uniformly or normally over all possibilities. That differs somewhat from reality if the interval in which this happens is short, but not so much that it disturbs the results a lot. However, if that interval becomes longer, the mathematical model is no longer correct. This is often seen in macroeconomic models: they do reasonably well in normal situations, but in crisis situations people do not behave according to expectations and the deviations are too great to make those models even of value. | |||
2. Another issue is the skewed age distribution of the corona virus infection: relatively many young people are asymptomatic. So they are infected without knowing it and spread (with lower chance, but still) the virus. Because they are not being tested, this distribution continues. Young people also meet more other young people on average, so the contagion can go on for quite some time before being noticed. From the perspective of the track and trace apps, this means that people have already fallen from the contact list that is about a week long. In this way, there are a lot of points along which the virus still spreads despite the use of the app. | |||
3. Demographics and living arrangements are also a determining factor. For example people lives who live in Italy look a little different than in the Netherlands. So the results are slightly different, but the conclusion remains. In the Italian case, the positive effect of testing randomly 20% of the population is even greater than in the Netherlands. | |||
The issues above are not easy to capture in macro level models, as those used in epidemiology. ASSOCC considers the difference between people’s ages, backgrounds, living situation and behavioral motives. Many scientific studies point out that the lack of a human behavior model in the epidemic models is a problem. ASSOCC is one of the few in the world that ''combines the human models with the epidemic models''. It would be nice if a lot ''more research'' was done, because then this type of models would improve greatly and there would be ''more comparative studies''. | |||
[1]ASSOCC. (2020, April 20). The simulation. Retrieved from https://simassocc.org/assocc-agent-based-social-simulation-of-the-coronavirus-crisis/the-simulation/ | |||
[2] ASSOCC. (2020b, April 21). Scenario: effect of track&trace apps. Retrieved from https://simassocc.org/scenario-effect-of-tracktrace-apps/ | |||
[3] Dignum, F. (2020, April 19). Mathematics vs. social models: how to understand the sociology of corona virus spread. Retrieved from https://simassocc.org/assocc-agent-based-social-simulation-of-the-coronavirus-crisis/news-and-publications/ | |||
===More information ASSOCC=== | |||
“The success of exit strategies does NOT depend on the track and tracing mechanism” [1] | |||
“Using a track and tracing app does NOT give us back our freedom” [1] | |||
An app does help to shorten the time between infection and detection on average, however, the spread of the coronavirus is therefore not controllable. The R0 of the coronavirus is now about 2.2. By using the apps, the simulation of ASSOCC never gives a R0 below approximately 2. That is approximately twice as high what is necessary for spreading control (R0 = 1). | |||
ASSOCC is not against the use of technology, however it should not crease false expectations. Also, the quantity of tests is getting out of hand when using the apps. (see figures last document) | |||
====Exit strategies: what does work? ==== | |||
test risk groups in a targeted and regular manner | |||
find out which areas are most likely to pose a risk of infection and illness (hot spots) and what can be done there | |||
For each measure or relaxation of a measure, check which possible consequences this has for public health, society, fundamental rights and economics (use e.g. simulations) | |||
Ask social groups what measures would work for them to restore normal life and use that to check the feasibility and consequences of measures | |||
Then, look at those points and look where the use of technology can make most positive contributions | |||
=== | ====Conclusion==== | ||
Tracking and tracing apps are NEVER a complete solution | |||
Exit strategies should be focused on specific target groups | |||
Exit strategies have to be combined and then tested before being applied so that any bottlenecks can be found | |||
Situations in countries differ, so strategies can not just be taken over from other countries | |||
====Contact with Frank Dignum about the comparison of ASSOCC with other simulations ==== | |||
“Hi Kim, | |||
Take a look at the paper attached. The Dutch government based their decision of implementing a track and tracing app on the model described in this paper (see below). | |||
I must warn you that comparing the models is not simple. We will publish an article about this soon. But it took us a lot of time to make a precise comparison where all the assumptions are clear and parameters and functions are explicit such that one can compare the results. We did all that and can now show that the apps still will not be effective if you take into account the human behavior as it is known. | |||
Good luck, | |||
Frank.” | |||
==COVID-19 agent-based Model with instantaneous contract tracing== | |||
=== | ===What is it? === | ||
The | The agent-based model (ABM) from the Dutch government was developed to simulate the spread of COVID-19 in a city, and to analyze the effect of both passive and active intervention strategies. | ||
ABM explores the effectiveness of contact-tracing app intervention by modelling five alternative scenarios which differ in how far the contact tracing extends through the contact network and the conditions on which individuals are released from app-instructed quarantine. | |||
===What is its purpose? === | |||
To assist the design and evaluation of approaches to instantaneous contact tracing using a mobile phone app that measures proximity events between phones with the app. | |||
===Why is it good? === | |||
An ABM is well-suited to quantifying the effects of combinations of non-pharmaceutical interventions in an epidemic because, unlike a simple epidemiological model, it records a history of previous events | |||
===How does it work? === | |||
It includes the three major domains of interaction: the home, the workplace (or school for children, or a regular social environment for older individuals), and the random interactions of daily life and travel. | |||
*The ABM is age-stratified | |||
*It is not spatially stratified at this stage | |||
*The contact processes are currently parameterized based previous work interviewing participants; they will be updated based on contact data collected by phone. | |||
The model of infection spread via interactions between individuals is parameterized based on the current literature of COVID-19 epidemiology and can be updated as more data emerges. | |||
== | ===Demographics === | ||
The demographics of the ABM are based upon UK national data from 2018 from the Office of National Statistics (ONS). | |||
Individuals are categorized into nine age groups by decade, from age group (0-9 years) to (80+ years). | |||
Every individual is part of a household, which forms an important part of their daily interactions. | |||
Since the duration of the simulated epidemic is less than a year, we do not consider changes in the population due to births, deaths due to other causes, and migration. (Migration is taken into account in ASSOCC) | |||
insert picture table here with this text: | |||
Table 1. Age-stratified population of the UK and number of households containing n people, with n = 1; 2; : : : 6, provided by the ONS. Parameter values match the OpenABM-Covid19 baseline parameters, April 28, 2020 | |||
===Interaction Network=== | |||
Every individual in the population is represented by a node in the simulation. Interactions between individuals are modelled via connections between nodes. The connections form | |||
networks, which are generated to represent different types of daily interactions. | |||
3 types of network: household, workplace, miscellaneous interactions | |||
Some of these networks are static and recur daily (e.g. household), whilst others are transient and are regenerated daily (e.g. miscellaneous). | |||
A previous study of social contacts for infectious disease modelling has estimated the mean number of interactions that individuals have by age group. This study is based on participants being asked to recall their interactions over the past day. We estimate mean interactions by age group by aggregating data (see Table 2). | |||
insert picture table 2 here with text: Table 2. Average number of interactions for an individual in each age group acquired from empirical estimates (14). Parameter values match the OpenABM-Covid19 baseline parameters, April 28, 2020 | |||
===Household network === | |||
There are two important population-level aggregate statistics that we match: the householdsize structure and the population age-structure. | |||
A reference panel with 10,000 households containing the household composition by age, produced by down-sampling UK-wide household composition data from the 2011 Census produced by the ONS is used to form the households. | |||
=== | ===Workplace network=== | ||
Each individual is a member of one workplace network (including e.g. schools for children and social activities for older adults). | |||
When on workplace the absence of overlaps between the household interactions and the local interactions on the small-world network is ensured. | |||
Parameters and values corresponding to the workplace network are shown in Table 3. | |||
insert picture table 3 here with text:Table 3. Mean numbers of daily connections for members of each age group, fraction of adults involved in occupational networks for children and for elderly people, and rewiring parameters for randomisation of daily interactions (14). Parameter values match the OpenABM-Covid19 baseline parameters, April 28, 2020 | |||
===Random Network === | |||
The number of random connections an individual makes is the same each day (without interventions) and is drawn at the start of the simulation from a negative-binomial distribution, an over-dispersed skew distribution. | |||
The mean numbers of connections were chosen so that the total number of daily interactions matched that from a previous study of social interaction | |||
Insert picture table 4 here with text: Table 4. Parameters for numbers of random connections that members of each age group have per day. Parameter values match the OpenABMCovid19 baseline parameters, April 28, 2020 | |||
===Infection Dynamics === | |||
The infection is spread by interactions between infected and susceptible individuals. | |||
The | The rate of transmission is determined by three factors: | ||
*the status of the infector; | |||
*the susceptibility of the infectee to infection, according to age; | |||
*the type of interaction (i.e. on which network it occurred). | |||
currently the model does not have data on the distribution of the duration of interactions, so the effect of this on transmission is not modelled. | |||
= | Infectiousness starts at zero at the precise moment someone is infected (t = 0), reaches a peak at some intermediate time, and tends to zero a long time after infection (large t ). | ||
Asymptomatic individuals are those who never develop symptoms during their infection | |||
pre-symptomatic individuals are those who do not currently have symptoms but will do so later | |||
both types may infect others | |||
To model the susceptibility to infection of a contact according to their age there was referred to the literature where close contacts of confirmed cases were monitored and tested. The number tested and the number of positive results was reported within each age group, with the ratio of the latter to the former defining the per-age attack rate. | |||
Model the type of interaction, (on which network it took place): Whilst we do not have data on the length of interactions, interactions which take place within a person's home are likely to be closer than other types of interactions leading to higher rates of transmission. This is modelled using a multiplicative factor. | |||
Combining all effects, the rate at which the virus is transmitted in a single interaction is modelled by | |||
Insert picture formula | |||
t = time since infection | |||
si = infector’s symptom status (asymptomatic, mild, moderate/severe) | |||
as = age of susceptible | |||
n = type of network where the interaction occurred | |||
Ias = mean number of daily interactions for somebody of the age of the susceptible | |||
Fr(u;u, o2) = probability density function of a gamma distribution | |||
ui and qi = mean and width of the infeciousness curve | |||
R = scales the overall infection rate | |||
SaS = scale-factor for the age of the susceptible | |||
= | Ast = scale-factor for the infector being asymptomatic | ||
Bn = scale-factor for the network in which the interaction occurred | |||
Insert table 6 with text: Table 6. Description of infection parameters and their values. The infection rate x was determined by fitting the simulation to have an epidemic doubling time of 3 days. Relative susceptibility values* were derived by merging and fitting to data from sources as explained in the text. Parameter values match the OpenABM-Covid19 baseline parameters, April 28, 2020 | |||
The rate of virus transmission is converted to a probability of transmission: | |||
Insert formula P(t,si,as,n) = 1- e^l(t,st,as,n) | |||
Insert table 5 with text Table 5. Steps in our calculation of susceptibility by age. The attack rate (the fraction of close contacts of a confirmed case infected) was merged from references. We fit to these values, and then scale them all identically to give a normalized susceptibility to infection. Parameter values match the OpenABM-Covid19 baseline parameters, April 28, 2020 | |||
insert figure 1, with text Figure 1. The attack rate, defined as the fraction of close contacts of a confirmed case infected, as a function of the contacts' age. Open circles show data merged from references. the line shows the fit A+B x (age)k. | |||
===Natural History of infection === | |||
Disease state transitions are shown in figure 2 | |||
insert figure 2, with text Figure 2. The disease status of an individual and the probability and time distribution of transitions. The _xxx(age) variables are the probability of transition to a particular state when there is a choice, where the probability depends upon the age of the individual. The _xxx are the gamma distributed variables of the time taken to make the transition. | |||
Upon infection, an individual enters a disease progression cascade where the outcome and rates of progression depend on the age of the infected person. | |||
Once an individual is recovered it is assumed that they have immunity and cannot be re-infected. | |||
pre-symptomatic state= in which a person is infectious but does not have symptoms | |||
==Bluetooth== | |||
=== | ===Why use Bluetooth?=== | ||
For | For contact tracing, solutions such as WiFi MAC address sniffing, GPS, and cellular network geolocationg have hall been proposed. However, the most suitable for use in CTA is often believed to be Bluetooth tracing. Many point to the effectiveness for proximity detection, that has already been demonstrated (Berke et al, 2020; Brack et al, 2020). They also claim that while Bluetooth has an effective range of around 25-30 metres, signal strength can be used to effectively identify whether another device is within the 2-metre rule promoted as a component of social distancing. [1] | ||
However, for many proposing CTA, the idea of using an app instead of just network tracing via the cellular network or other means is not as much about Bluetooth being more accurate, it is about the idea of claiming to have informed consent: that by downloading the app and clicking through a privacy agreement they have received ‘informed consent’ to access and monitor an individual through their device. [1] | |||
Smartphone apps for Bluetooth-based contact tracing, such as the European PEPP-PT project, the British NHSX, or the Swiss D3PT, can help to identify individuals that have recently had an infection-relevant contact (i.e. one that confers a risk of transmission) with known Covid-19 cases and might therefore have been infected. [2] | |||
Since a large percentage of the world’s population carries smartphones, these approaches make use of the BLE technology. Contact advertisements regularly emitted from these devices are used to assess the proximity of encounters [4] | |||
===How does it work?=== | |||
There are several different ways on how to tackle the use of Bluetooth. Below, you can see some different examples of how the process is tackled | |||
== | ====First example==== | ||
= | |||
== | |||
The | The data being collected Drawn from many of the cited papers in this work, most apps will collect and transmit some subset of the following data fields: | ||
* MAC address of your device’s Bluetooth or Wi-Fi chip | |||
* Your Phone number (or IMEI number if the device does not easily report the subscriber phone number) | |||
* The MAC address of other people your phone sees (Bluetooth handshakes with everything it sees that is also Bluetooth, even when it doesn’t know the device and has never been paired with it) | |||
* The time, date and in some cases, location data from your GPS for each new interaction with another in-range device (accurate to about 15 meters). A new interaction is when your device sees another device move into its broadcast area. Note that in a corporate office the app might see the device of someone in the next room move into and out of range tens or hundreds of times over the course of a working day. | |||
* The Bluetooth or device name of the smartphone that is running the app, and every other Bluetooth device that crosses into its broadcast range. This last point can more easily enable re-identification as people often name their smartphone ‘Tim’s iPhone’ or similar. [1] | |||
====Second example==== | |||
This second example focusses more on the “privacy by design” COVID-19 tracing approach. It is the TraceTogether app from the Singaporean government. Unlike the contact point system, it only requires users to enable Bluetooth on their phone. Pan-European Privacy-Preserving Proximity Tracing (PEPP-PT) by the European consortium , as well as Google and Apple’s recently announced joint initiative, are following a very similar concept. | |||
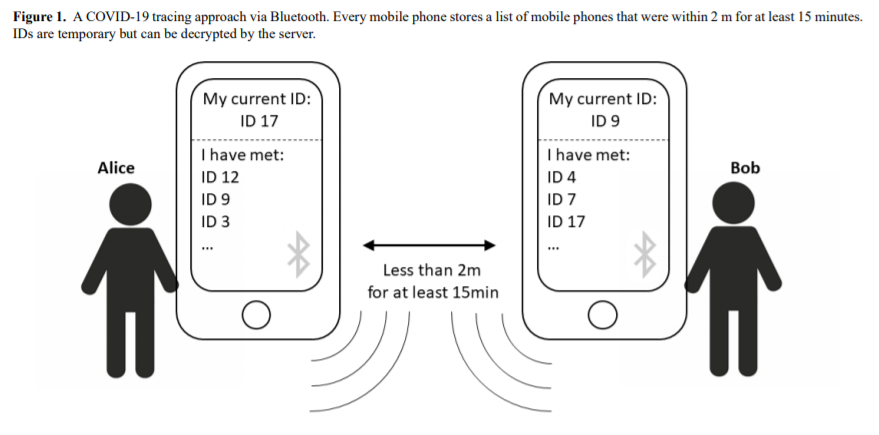
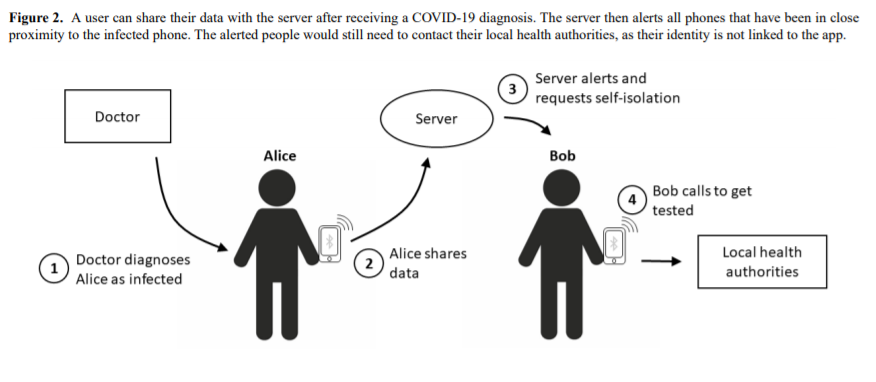
We present a slightly modified version below. In order to detect whether two people have come into close enough physical proximity to risk an infection, one can use Bluetooth low energy technology. The general drawback of Bluetooth—that it can only reach across a few meters—becomes an advantage here. The tracking itself would work as follows: as many people as possible voluntarily install the app on their phone. The app cryptographically generates a new temporary ID every half hour. As soon as another phone with the same app is in close proximity, both phones receive the temporary ID of the respective other app and record it. This list of logged IDs is encrypted and stored locally on the users’ phones | |||
[[File:Bt.PNG]] | |||
As soon as an app user is diagnosed with COVID-19, the doctor making the diagnosis asks the user to share their locally stored data with the central server (Figure 2). If the user complies, the central server receives information on all the temporary IDs the “infected” phone has been in contact with. The server is not able to decrypt this information in a way that allows for the identification of individuals. However, it is able to notify all affected phones. This is because the server does not need any personal data to send a message to someone’s phone. The server only needs a so-called PushToken, a kind of digital address of an app installation on a particular phone. This PushToken is generated when the app is installed on the user’s phone. At the same time, the app will send a copy of the PushToken, as well as the temporary IDs it sends out over time, to a central server. The server could be hosted, for example, by the Robert Koch Institute for Germany or by the National Health Service for the United Kingdom. This way, it would be possible to contact phones solely based on temporary IDs and PushTokens whilst completely preserving the privacy of the person using the phone. | |||
[[File: Bt_2.PNG]] | |||
If a phone has been in close proximity to an “infected” phone, the user of that phone receives a notification together with the request to immediately go into quarantine at home. The user will then need to contact the local health authorities to get tested for the virus as soon as possible so that, depending on the outcome, the user is either able to stop quarantining or all their contacts can be informed (Figure 2). | |||
During the entire process, no one learns the identity of the app user (eg, other users who got in close contact with them, the local health authorities, the central server) since the app is not linked to an identity. Location data is neither recorded nor stored at any point of the process [3] | |||
[1] https://arxiv.org/ftp/arxiv/papers/2005/2005.06621.pdf | |||
[2] https://www.medrxiv.org/content/10.1101/2020.03.27.20045237v2.full.pdf | |||
[3] https://mhealth.jmir.org/2020/4/e19359/pdf | |||
[4] https://arxiv.org/pdf/2004.11841.pdf | |||
===What goes in the paper=== | |||
====Why use Bluetooth?==== | |||
For contact tracing, solutions such as WiFi MAC address sniffing, GPS, and cellular network geolocationg have hall been proposed. However, the most suitable for use in CTA is often believed to be Bluetooth tracing. Many point to the effectiveness for proximity detection, that has already been demonstrated [a,b]. They also claim that while Bluetooth has an effective range of around 25-30 metres, signal strength can be used to effectively identify whether another device is within the 1,5-metre rule promoted as a component of social distancing. [c] | |||
However, the original Bluetooth BR/EDR protocol, while it was designed for primarily “pairing” phones with other devices such as computers, Bluetooth speakers, or keyboards for the purpose of data communication, it was a non-time sensitive process. It was not designed to have a reliable and sustainable contact tracing, as what currently is looked into as a solution for this pandemic. In the traditional pairing process, if the pairing is not successful then the user has to reset one of the devices and try again. This manual intervention is not sustainable in the context of contact tracing, where two or more phones are always expected to “pair” reliably. | |||
In comparison, the Bluetooth Low Energy (BLE) protocol, has been designed for continuously scanning in the background and is therefore the main choice for neighbor discovery on smartphones. The main reason why contact tracing apps choose for continual transmission and listening instead of continuous is energy [d]. The energy costs would be higher when using continuous transmission and listening. | |||
====How to optimize Bluetooth? ==== | |||
[ | There is however a problem that arises with the use of BLE. It can namely travel through a wall. Even though the more objects there are in between the devices, the less overall range a device will have [e], it can lead to some troubling scenarios. | ||
One of these scenarios is tracing through your neighbors wall. Imagine your neighbor, who you don’t come in contact with, tests positive for the virus. Both phones, yours and theirs, connect with each other via Bluetooth through the wall, it can lead to possible quarantine for you, even though you haven’t come in contact with each other. This leads to some problems especially in heavily populated areas, such as in cities and apartment complexes. | |||
One solution that we propose, would be the use of sound in combination with this BLE. While the BLE detects the phones at a continuous pace, the sound application could act as a safe switch to check whether there is an object such as a wall in between both phones. | |||
References | |||
[a] Berke, A., Bakker, M., Vepakomma, P., Raskar, R., Larson, K., & Pentland, A. (2020). Assessing disease exposure risk with location histories and protecting privacy: A cryptographic approach in response to a global pandemic. arXiv preprint arXiv:2003.14412. | |||
[ | [b] Brack, S., Reichert, L., & Scheuermann, B. (2020). Decentralized Contact Tracing Using a DHT and Blind Signatures. Last accessed: 01st May, 2020. Sourced from: https://eprint.iacr.org/2020/398.pdf | ||
[c] Mclachlan, Scott & Lucas, Peter J. & Dube, Kudakwashe & Hitman, Graham & Osman, Magda & Kyrimi, Evangelia & Neil, Martin & Fenton, Norman. (2020). Bluetooth Smartphone Apps: Are they the most private and effective solution for COVID-19 contact tracing?. Sourced from: https://arxiv.org/ftp/arxiv/papers/2005/2005.06621.pdf | |||
[d] P.H. Kindt, T. Chakraborty, & S. Chakraborty. 2020. How Reliable is Smartphone-based Electronic Contact Tracing for COVID-19?. arXiv preprint arXiv:2005.05625. DOI: https://arxiv.org/abs/2005.05625 | |||
[e] TechWalla. (n.d.). What are the limitations of bluetooth. Retrieved May 27, 2020, from https://www.techwalla.com/articles/what-are-the-limitations-of-bluetooth | |||
==Decentralized Approach== | |||
For this app there is a choice between handling with a centralized or a decentralized approach. In a centralized approach, the government authority will control the personal data. With a decentralized approach, the collected data will be stored locally with the user [a]. The choice regarding the use of a centralized or decentralized approach lies mainly within the arguments regarding data protection and privacy. | |||
With centralized structures, the collected data of the app is controlled by the government authority. Centralized apps follow mainly the PEPP-PT (Pan-European Privacy-Preserving Proximity Tracing) [b], but this framework is according to the technical community too academic for practical development. A decentralized structure has the data enclosed or controlled by individuals on only personal devices. Those apps follow DP-3T (Decentralised Privacy-Preserving Proximity Tracing) [c], but this is only partly decentralized. No pooled data is collected, which largely mitigates the privacy risk. The none-infected individuals’ data are decentralised based, and the infected individuals’ information will be collected anonymously to a central database. [a] Google and Apple will release an exclusive decentralized framework which will be more compatible with IOS and Android systems [d]. | |||
There would be a trade-off between the insights gained and the privacy of the data. The decentralised and no GPS solution gives one of the highest level of data protection for users because no personal data is collected unless the individual is infected with the virus. Apps cannot collect the movements and trace them geographically without GPS tracking. This means that the data can’t be traced to an individual. Bluetooth tracing does work as compatible technology for this decentralized approach. However this means that data collected can not be driven into a centralized database for analysis and the government has less information for controlling the self-quarantine and movement of the disease. [a] | |||
In conclusion, a decentralized approach would fit well regarding data issues and be more compatible with a Bluetooth based system. This together with the fact that there is a strongly growing trend globally, and especially in Europe, which shows that the decentralised approach would be preferable [27, 28], finalizes our advice to use a decentralized approach. | |||
[a] Li, J., & Guo, X. (2020). COVID-19 Contact-tracing Apps: A Survey on the Global Deployment and Challenges. arXiv preprint arXiv:2005.03599. | |||
[b] Cooper, D.; Quathem, K.V.; Meneses, A.O. COVID-19 Apps and Websites – The “Pan-European Privacy Preserving Proximity Tracing Initiative” and Guidance by Supervisory Authorities. Available online: https://www.insideprivacy.com/covid-19/covid-19-apps-and-websites-the-pan-european-privacy-preserv ing-proximity-tracing-initiative-and-guidance-by-supervisory-authorities/ (accessed on 5 May 2020). | |||
[c] GitHub. Decentralized Privacy-Preserving Proximity Tracing. Available online: https://github.com/DP-3T/documents/blob/master/README.md (accessed on 5 May 2020). | |||
[d] Apple Newsroom. Apple and Google partner on COVID-19 contact tracing technology. Available online: https://www.apple.com/newsroom/2020/04/apple-and-google-partner-on-covid-19-contact-tracing-techno logy/ (accessed on 5 May 2020). | |||
[27] O. Lynskey, & M. Veale. 2020. Supplementary Written Evidence on COVID-19 Tracing Apps to the Joint Committee on Human Rights. DOI: https://doi.org/10.31228/osf.io/p7kqw | |||
[28] J. Li, & X. Guo. 2020. COVID-19 Contact-tracing Apps: A Survey on the Global Deployment and Challenges. arXiv preprint arXiv:2005.03599. DOI: https://arxiv.org/abs/2005.03599 | |||
==Related works, Models== | |||
A simulation model is one of the methods that is commonly used in Operational Research. Operational research (OR) deals with the application of advanced analytic models to help make better decisions. A simulation model represents the real situation that occurs in a system and tests multiple scenarios based on different behavior [4]. Simulation models can be useful to obtain more of an understanding about a current system by testing scenarios using specific software tools [4]. It can be seen as an incorporating time that reflects to any changes that occurs over time [4]. | |||
Because of the COVID-19 pandemic, the government has to come up with a set of policies to contain the virus. Multiple simulation models are used to see what effect certain policies have on society. The mobile contact-tracing app is one of these policies which can be tested with the simulation models. | |||
The | The ASSOCC model (Agent-based Social Simulation for the COVID-19 Crisis), is a simulation model that has specifically been designed and implemented by European researchers from Umeå University, TU Delft, Malmö University, Utrecht University, Caen University and Stockholm University to address the societal challenges of the COVID-19 pandemic [1]. This model studies the individual and social reactions to containment policies and it is a tool that can be used by decision makes (such as the government) to explore the different scenarios with their effects. The ASSOCC model does not generate predictions, however, it simulates the behavior of a synthetic population given a set of policies (for example the contact-tracing app) [1]. The model enables to study the possible effects on the spread of the virus, how people can be expected to react to the policies and the socio-economic effects of the policies [1]. ASSOCC is built in NetLogo, which is a multi-agent programmable modeling environment [5]. It is based on a set of artificial individuals which each have a set of given needs, attitude towards regulations and risks, and demographic characters [1]. Each artificial individuals decides at each time what they should be doing. These decisions are based on the individual’s profile, state and social, psychological and physical needs [1]. An action is selected by an individual by first making a list of all possible places it can go to with different motivations, which is called an action [1]. It then calculates the global expected effects on the needs of these actions and it lastly selects the action which satisfies the highest number of needs [1]. | ||
The ASSOCC model has looked at the effects of implementing the contact-tracing app policy into society. In this scenario, a perfect app aligned with all functional, legal and ethical requirements is assumed [2]. The effectiveness of such an app was researched by performing three experiments. First, the effect of the app depending on different percentages of population (0%, 60%, 80% or 100%) using the app was studied. According to the ASSOCC model, using the app does result in a lower infection peak, however, these differences are not significant and increasement of app users results in a sharp increasement of needed testing [2]. | |||
Next, the effect of using the app was compared with random studied of a percentage (0% or 20%) of the population. According to the ASSOCC model, random testing raised the awareness of infection, even when the artificial individuals had no reason to suspect infection and is more effective than the app [2]. | |||
Third, The effect of the app depending on the percentage of risk avoiding individuals that use the app (0%, 30% or 60%) was studied. According to the ASSOCC model, the effects of risk averse people were not significantly visible [2]. | |||
It can be concluded from the model that the effectiveness of contact-tracing apps on lowering the rate of infected individuals is limited and lower than that of random testing and that the app makes no significant contribution to the spread of the virus [2]. | |||
The Dutch government based their decision of implementing a contact-tracing app on the COVID-19 agent-based model (ABM) with instantaneous contact tracing. It was developed to simulate the spread of COVID-19 in a city, and to analyze the effect of passive and active policies [6]. The demographics of this model are based upon UK national data for 2018 from the Office of National Statistics [6]. The ABM model is based on a set of artificial individuals which are categorized into nine age groups by decade. Each individual is part of a structural and transient network and is part of a household, which is an important part of their daily activities. Everyday, each individual interacts with a random subset of their connections and has random connections. The status of the infector, the susceptibility of the infected person to infection according to age and the type of interaction determine the rate of transmission of the virus [6]. | |||
The active policy of digital contact-tracing was studied in this model. When contact-tracing, a random number of interactions is assigned to the model. The usage of the app is just as the model age-dependent. According to the ABM, contact tracing is vital to control the spread of COVID-19 for infections with high levels of pre-symptomatic transmission [6]. The ABM allows to explore this policy and its effects and contains the option for recursive tracing of contacts of contacts [6]. | |||
Both the ASSOCC model and the ABM are agent based simulations. This means they are able to handle with the uncertainty and variability of the system [1]. Both models are however constructed differently, which leads to different results of the effectiveness of a contact-tracing app. In this paper, these two models are analyzed and compared to each other to give advice about the effectiveness of contact-tracing apps. | |||
Sources | |||
[1]ASSOCC. (2020, April 20). The simulation. Retrieved from https://simassocc.org/assocc-agent-based-social-simulation-of-the-coronavirus-crisis/the-simulation/ | |||
[2] ASSOCC. (2020b, April 21). Scenario: effect of track&trace apps. Retrieved from https://simassocc.org/scenario-effect-of-tracktrace-apps/ | |||
[3] Dignum, F. (2020, April 19). Mathematics vs. social models: how to understand the sociology of corona virus spread. Retrieved from https://simassocc.org/assocc-agent-based-social-simulation-of-the-coronavirus-crisis/news-and-publications/ | |||
[4] Sumari, S., Ibrahim, R., Zakaria, N. H., & Ab Hamid, A. H. (2013). Comparing three simulation model using taxonomy: System dynamic simulation, discrete event simulation and agent based simulation. International Journal of Management Excellence, 1(3), 54-59. | |||
[5] Wilensky, U. (2016). NetLogo Home Page. Retrieved from https://ccl.northwestern.edu/netlogo/ | |||
[6] Hinch, R., Probert, W., Nurtay, A., Kendall, M., Wymant, C., Hall, M., Lythgoe, K., Cruz, A. B., Zhao, L., STEWART, A., FERRETTI, L., ABELER-DORNER, L., BONSALL, D., & FRASER, C. (2020). COVID-19 AGENT-BASED MODEL WITH INSTANTANEOUS CONTRACT TRACING. BIG DATA INSTITUTE, NUFFIELD DEPARTMENT OF MEDICINE, UNIVERSITY OF OXFORD | |||
=Deliverables= | |||
[[File: | '''The final version of the research paper can be found here:''' | ||
[[File:Final_version_paper.pdf]] | |||
[ | '''The link to the video presentation can be found here:''' | ||
[https://www.youtube.com/watch?v=qazIig4W7F4] | |||
'''The peer review as done by the group can be found here:''' | |||
[[File:Peer_review.pdf]] | |||
(keep in mind that a part of the table can be found on the second page) | |||
''' | '''This results in the following adjustments to grades:''' | ||
{| border=1 style="border-collapse: collapse; width: 30%; height: 14em;" | |||
! Name | |||
! Adjustment | |||
|- | |||
| Ezra Leeuwenhage || -1 | |||
|- | |||
| Paulien Teuwen || 0 | |||
|- | |||
| Yorn Thijssen || 0 | |||
|- | |||
| Ries van de Ven || +0.5 | |||
|- | |||
| Kim Wintraecken || +0.5 | |||
|} | |||
1 | |||
Latest revision as of 19:02, 25 June 2020
Project Robots Everywhere - The Corona App
In these turbulent times, Corona has been affecting our daily lives. It has been such an impactful disease, that the government had to come up with a solution on how to create awareness of those who have had COVID-19 and those who do not. One of the most widely discussed option in the Netherlands would be a Corona Mobile Application (Corona App).
However, there is still a lot of discussion surrounding this app and its applications. The goal of the Corona App is to give an insight into the current spread of the virus, such that regulations can be implemented or improved, based on this spread. In this project, however, the focus will lie solely on the effectivity of such an app and it’s requirements for this. Effectivity will be the focus because if an app can’t be efficient enough, it would be useless to implement. This is also the reason why there will be no focus on other social questions such as privacy.
Based on literature reviews, simulations, and user-testing, these requirements will be listed and a proposal will be formed about the effectivity of such an app.
Groupmembers
| Name | Student Number | Study |
|---|---|---|
| Ezra Leeuwenhage | 1313568 | Computer Science and Engineering |
| Paulien Teuwen | 1337904 | Industrial Design |
| Yorn Thijssen | 1342320 | Industrial Design |
| Ries van de Ven | 1318578 | Industrial Design |
| Kim Wintraecken | 1322842 | Industrial Design |
Problem statement and objectives
The issue capturing global attention in recent months is the Covid-19 pandemic, causing great disruption throughout the world in both in terms of health care and economy. Many governments have since the outbreak opted for an approach to combat the virus through limiting all social interactions within society (commonly referred to as a lockdown), putting a halt to its spread at the cost of national economy. In the long term this approach is not sustainable however, leading to the need to find ways to reduce restriction on social interaction in all aspects of society without losing grip of the spread of the virus. To this end, the Dutch government has suggested the nation-wide employment of an application designed to predict/ detect infection with Covid-19 of civilians, enabling them to accurately manage the virus’s impact on society without the need for a type of lockdown. The need for such an app is still being questioned, since it brings a lot of difficulties with it, regarding the violation of the Dutch privacy legislation.
However, there would be no need to check all social implications in detail, if such an app is simply not efficient enough to contribute to the curbing of the virus. Since in this scenario, it would be fruitless to implement such an app. This project will shed light on the requirements that need to be met, to make the app efficient enough to combat the Covid-19 pandemic.
The objectives of this project will be to determine through literary research what the relevant requirements are to the problem and what exactly the desired effectiveness of the application is in order to meet its requirements. Finally, the objective of practical research done thereafter will be to determine what type of implementation of the app satisfies the requirements set by the results from literary research.
The results of the project can be found under week 9 of the section 'progress per week'.
Who are the users?
Users:
- Smartphone users
- Dutch citizens (who own a smartphone)
Other stakeholders:
- Government
- Public health authorities
- Hospitals
- Healthcare personnel
- Outbreak Management Team
What do they require?
Users require:
- Safety check
- Did I come in contact with anybody who is registered with the virus, or who has recovered from the virus?
- Raise own awareness of spreading possibilities
- How can I prevent the spread of the virus myself?
- Current information about situation
- News-updates
- Latest governmental conferences
- Current national measurements
- Healthcare issues and prevention methods
- How can I protect myself?
- What to do if I need to leave the house for necessity?
Stakeholders require:
- Additional data about the spread of virus
- New data can be used to make estimations or inform the country
Approach, milestones, and deliverables
Approach
Solving the problem around the corona app has a difficult set of objectives: first, the group should evaluate the existing research about the corona app and the current simulations that exist regarding the efficiency of such an app. Next, different simulations must be compared and analyzed to specify a list of requirements and parameters. Also, recommendations will be given about the implementation of technology, and app developers of corona apps were contacted.
These results should confirm or deny earlier research and the goal is to determine if a corona app would be suitable to achieve the combat of the virus.
Milestones
A certain milestone is gathering all the research needed. another milestone is the comparison of the simulation models.
Week number: Tasks
| Week 1: | gathering research |
| Week 2: | gathering research |
| Week 3: | gathering research |
| Week 4: | compare models and contact app developers |
| Week 5: | analyze models and analyze interviews app developers |
| Week 6: | paper writing |
| Week 7: | paper writing |
| Week 8: | paper writing, Final presentation, and demo (recorded video) |
Deliverables:
The output of the project should be an analysis of a simulation made to map the effectiveness, as well as a proposal containing the requirements that need to be met. Furthermore, a wiki page containing all information on the process of the project and the final presentation of week 8 will be delivered.
Who is doing what?
To create a full detailed planning for the whole course is difficult, especially in situations like these where we do not know what we are capable of and things can change every week. Therefore, we have chosen to divided tasks after each meeting or every week just like in an OGO project. These assigned tasks will be published weekly on the wiki in a table. However, to keep track of the schedule, some team members will be assigned to have a leading role over a part of the project.
Furthermore, because we are doing the project like an OGO project, we also assigned roles for Chairman and Minute taker for each meeting. This will be according to the following schedule:
Meetings per week:
Monday - 09:30
Thursday - before after tutoring session
Chairman Minute taker
| Date | Chairman | Minute Taker |
|---|---|---|
| 27/04 | Kim | Ries |
| 30/04 | Ries | Yorn |
| 04/05 | Yorn | Ezra |
| 07/05 | Ezra | Paulien |
| 11/05 | Paulien | Kim |
| 14/05 | Kim | Ries |
| 18/05 | Ries | Yorn |
| 21/05 | Yorn | Ezra |
| 25/05 | Ezra | Paulien |
| 28/05 | Paulien | Kim |
| 01/06 | Kim | Ries |
| 04/06 | Ries | Yorn |
| 08/06 | Yorn | Ezra |
| 11/06 | Ezra | Paulien |
| 15/06 | Paulien | Kim |
| 18/06 | Kim | Ries |
Weekly hours
Progress per Week
Week 1
During the first week of the project, a decision had to be made on what the subject of our study would be. All group members brainstormed about these ideas and offered several project ideas. Lists of ideas, as well as a mural, were made. (for a more in-depth view of those ideas and the mural, see file: File:Brainstorm week 1.pdf, File:Mural week 1.pdf) The main suggestions that came out of this session and were considered in this first week were: a healthcare robot, a gardening tool, facial recognition with emotions, or a literature study to already existing technology.
Regarding the situation at hand (the COVID-19 pandemic), we thought it would be interesting to research the current state of the so-called Corona Apps. Our initial plan was to create 2 apps that functioned in a different perspective. one out of the value of efficiency, one out of the value of privacy. Later on, this plan would change, but during week 1 and 2, the first general research was done regarding these apps.
Week 2
During the second week, a lot of research has been gathered. However, after a meeting with our tutor, adjustments to the planning were made. In summary, the project was scaled down to a concise and reachable set of goals and tasks and the emphasis for the first few weeks was shifted towards setting valuable, precise, and well-founded requirements for the implementation of the corona app. This meant we were looking for specific requirements that the app should have.
Details of that particular meeting have been recorded here: File:Notities conference call 1.pdf
Several different topics were researched:
Yorn focused on privacy, as well as on how the different countries in the world handled such a Corona app and what values they found important. For more information, see File:Yorn.pdf
Kim focused more on the app development itself. This includes interface, aesthetics, software, medical apps, similar products and technology, and the ethics regarding a health/medical app. For more information, see File:Kim.pdf
Ezra focused on topics such as privacy, virus spread modeling, and teledermatology applications. For a more in-depth view, see File:Ezra.pdf
Ries focused on exploring contact tracing, as well as an app called TraceTogehter, which is the corona app for Singapore. For more info, see File:Ries.pdf
Paulien focused more on the political views, such as open letters to the government of the Netherlands and Belgium, as well as manifestos. She also looked at the Swedish simulation of the corona app and the Oxford research regarding 60%. More info can be found here: File:Paulien.pdf
Week 3
The requirements to be set were discussed in meeting 4 (File:Minutes 04 05 20.pdf) and these were the main results in terms of the type of requirements to be investigated en quantified:
- Users & habits (of dermatological application software) see more in File:User & Habits.pdf
- Combatting virus spread (more info can be found in File:Bestrijding van verspreiding.pdf)
Other useful leads in advancing the project that were explored:
- Viability and reliability of employment of simulation software (by TU Delft) for testing effectiveness of corona app File:Week 3 Kim eisen.pdf
Week 4
During the 4th week, app developers were contacted to gain more information regarding the app simulations. (more info can be found in File:Antwoorden app developers.pdf
Furthermore, other simulations were looked at during this period. These include the Simulation of Delft, ASSOCC. File:Hw kim simulation simulation delft.pdf
Week 5
During week 5, the last efforts for information gathering were made, before we started to write the paper. This included findings regarding contact tracing, covid-19 models, Bluetooth, ... More information on these topics can be found in this Wiki, at Research per Topic.
Week 6
In week 6 we redefined why we want to use Bluetooth; wrote the first parts of the report that will be the end deliverable such as related works etc; and finished the contacting people.
Paper
Week 7
This week, everyone has been working on the content of the research paper. Everyone is gathering information from the related works and using this to critique certain decisions of other applications and simulations. We compare applications and simulations in order to find the best solution for each part of the application in order to reach the highest effectivity. We will be organising the wiki page as of next week. Next to that, we will start working on the presentation for the course and keep on updating the research paper. What work has been done:
- Reasoning for why Bluetooth is the best possible option for proximity tracing and how this can be improved [INCLUDED IN PAPER]
- Simulation models are being critiqued and compared in order to draw valuable conclusions on what is missing or what is very useful and makes it an effective simulation. [NOT ADDED TO PAPER YET]
- Related works of state of the art applications, critique on them and finding values within the apps. [NOT ADDED TO PAPER YET]
- Referencing every piece of work of others correctly, refining the pieces of text in the related works and adding all the pieces of text to the paper.
- Formulating which approach to use: decentralised or centralised and why. [NOT ADDED TO PAPER YET BUT BELOW IN WIKI PAGE]
Paper
Paper (work in progress) : File:Wiki bestand paper v2.pdf
Week 8
Last efforts regarding the paper were made, before a feedback session with the tutor of this course
Paper
paper in progress (as of 9th of June 2020) File:Wiki bestand paper v3.pdf
Week 9 and Deliverables
During this week, the paper was finalized
The final version of the research paper can be found here: File:Final version paper.pdf
The link to the video presentation can be found here: [1]
The peer review as done by the group can be found here: File:Peer review.pdf (keep in mind that a part of the table can be found on the second page)
This results in the following adjustments to grades:
| Name | Adjustment |
|---|---|
| Ezra Leeuwenhage | -1 |
| Paulien Teuwen | 0 |
| Yorn Thijssen | 0 |
| Ries van de Ven | +0.5 |
| Kim Wintraecken | +0.5 |
Research per topic
App developers
In this research several models and simulations about the effectiveness of a corona app are investigated and studied. Before the idea of implementing such a track and trace corona app these kinds of simulations were not available yet, so there could not really be stated anything about the effectiveness of such an app. But even though this was not known, app developers already started with bringing ideas about how they could help with an app during this crisis.
On the 11th of April the Dutch government made a call for companies and experts to think about the development of apps in the approach against corona virus. This proposal had to be in of three categories:
- An app that to determines contact between people and notifies when a user was in contact with an infected person.
- An app that makes it easier to have contact with a doctor from home.
- Any other ideas of an app that could help in the fight against corona.
These companies and experts could submit a proposal until Tuesday 14th of April, 12:00. In total there were more than 750 proposals submitted. Eventually 7 teams were chosen to take part in an ‘Appathon’, a digital event to test and improve the working of these corona apps. According to experts, the apps of these 7 teams best match the approach of the Municipal Health Services (GGD) for doing source and contact research, while at the same time meeting requirements that are set in areas such as privacy, data and information security and ease of use.
All seven teams have been contacted for this research to interview them with questions about their approach and if and how they simulated the effectiveness of their app. Not all seven initiatives responded but the ones that did gave very interesting insights and even provided new research. A summary of each interview is given below.
The DEUS initiative
The DEUS initiative explores and builds AI services to create a positive impact on our future. They combine data, design and artificial intelligence to solve challenging problems elegantly, ethically and efficiently.
Before the call of the government, Deus was already brainstorming about how they could help during this pandemic. When the opportunity of coming with this proposal was there, the whole team threw themselves into this. Because of the three categories in which they could submit their proposal in, the team thought of a wide range of technological possibilities (even using WhatsApp for having easier contact on distance). Specifically for the track and trace app, the team performed a technical audit to analyze worldwide existing solutions. The result of this audit was that they proposed the open source DP-3T protocol which has one major benefit: privacy is guaranteed. The protocol does not save personal information neither does it track location. This criteria for privacy was the most important aspect for proposing this protocol. However, this benefit is at the same time a big disadvantage because the GGD would want to know this information. Another important aspect in proposing this protocol is the fact that it is open source. Deus thinks when it is developed by a community it can eventually be developed to a European Standard of a track and trace app.
During the ‘appathon’ Deus showed how a Dutch version of an application with use of the DP-3T protocol would look and work. The application exchanges a digital handshake with use of Bluetooth. It does so when a user has been within a particular distance for a particular time. This distance and time would be determined by the GGD which has a vision about when risk of contamination is higher. The handshakes would be saved and when a user would be tested positive with the disease, this user gets a code from the GGD and enters this in the application. The app then notifies all the other users who saves a ‘handshake’ with this user in the last 10 or 14 days.
This app would support or automate the way the contact research is done now. Currently, when someone is tested positive, he or she will sit down with someone from the GGD and will make an excel sheet with all the people with whom you remember you have been in contact with in the last 14 days, together with their e-mail and phone numbers. The app would reduce work pressure.
Unfortunately, The DEUS team does not have tested their app on effectiveness, simply because there was no time for that.
ITO
Ito is a team of individuals with varied experience who are forming a global alliance of privacy-focused open source projects working on decentralized tracing solution, for example for a tracing corona app. The goal of Ito is to create a unanimous privacy-protecting protocol that different countries and institutions can build their contact tracing apps on. They work entirely voluntarily. The team is built up by several teams that participated in the Appathon/Hackathon in Germany.
Unfortunately for Ito, the German government ignored any suggestion of tracing apps and therefore also the Ito team. The Ito team saw this as motivation to show that it can be done better. On the moment of writing, the Ito team has not yet reached their goal. Things are continuously changing and they adjust towards this. However, they do have a working android app but it is not secure yet.
The app works with the TCN (Temporary Contact Numbers) protocol. It is very similar to the DP-3T protocol and also works with Bluetooth and handshakes. They have to work on privacy, and eventually want to have a free software alternative for the google and apple framework.
Within their goal it is clear what their most important value is in developing this app. Privacy. The team wants to reach this by i.a. making everything as transparent as possible. Everything is posted online, from research to source code. Even their meetings which take place every 2 days, and their notes can be viewed back.
Ito works in collaboration with the technical university of Munich. At this university, some physicists and Mathematicians work on simulations and models. These simulations are not tight to the app, but rely on variables. It for instance tells how many people would need to download the app to have effect.
Contact tracing
Effectivness of Contact Tracing
Knowing when contact tracing is effective is of great importance. The probability of detecting every individual contact of an infected person is therefore composed of two factors [1]:
The fraction of the population that uses a smartphone-based contact tracing application or app, i.e., its adoption rate.
Another factor which is determined by the probability with which a smartphone is able to reliably detect a contact.
In order for the device to be reliable in its act, the system needs not to rely on GPS data, since this is not reliable due to its inaccuracy [1]. In [1] the authors proposed to use neighbor discovery (ND) [1]. It is based on the phones emitting and scanning for Bluetooth signals, and a successful reception of an emitted Bluetooth signal by another phone and vice-versa will lead to their mutual discovery. For ND, Bluetooth Low Energy (BLE) will be used, because it is designed for continuously scanning in the background. The main reason why contact tracing apps choose for continual transmission and listening instead of continuous is energy [1]. The energy costs would be higher when using continuous transmission and listening.
Treatment or quarantine of people who have been in contact with each other may be effective because unidentified infected persons are most likely to be found among those people, and efficient because the resources can be directed towards individuals at risk only [3]. In order to get effective quarantining and isolation going and because testing and isolation are expensive, there is a strong need to avoid too many false positives [1].
According to [2], contact tracing using smartphones can considerably reduce the reproduction rate R, even with partial adoption of contact tracing apps. However, according to [1], the adoption of contact tracing apps has to be considerably larger than 60% to contain the spread. Therefore, they believe that next to only smartphone related approaches, approaches other than smartphones need to be pursued in order to reach the highest effectiveness [1].
Looking at effectiveness of contact tracing, the latent period (the time interval between when an individual is infected by a pathogen and when he or she becomes capable of infecting other susceptible individuals) needs to be taken into account. [3] teaches us that, whenever the detection time of an infected person is fixed, a too large latent period (larger than the detection time) results in a situation where every infected person is detected before transmitting the infection, so tracing need not prevent any transmission. Effectiveness may therefore be very sensitive to the latent period, especially if there is little variation [3].
The sensitivity of tracing effectiveness to the latent period and tracing delay may be large, especially in the case of single-step tracing [4, 5, 6]. If the same happens with a small delay, reliability of parameter estimates will be of great importance to establish whether tracing is of any help. If it is only the case with larger delays, it could only be effective if it is done quick enough [3]. In most situations single-step and iterative tracing are almost equally effective. A great difference can only be seen if single-step tracing is not or hardly effective, which is also when the sensitivity to the latent period and tracing delay is largest [3]. A variable detection time would therefore improve the effectiveness of the contact tracing [3].
Looking at the ND approach, there are however a few restrictions when looking at the use of smartphones [1]:
When using larger delays than specified in BLE will further improve the reliability in crowded scenarios where multiple phones are present and send beacons, will accordingly introduce an overhead of a factor of approximately six times the energy spent for transmission.
The use of Android and iOS hardware might force the vary fixed values for parameters during the runtime. Next to that, the device might need to run other Bluetooth related tasks in parallel, so overlap will be happening. Because the device can carry out only one task at a time, some scheduling is needed to resolve this conflict. Smartphones share certain hardware components like radio and/or antenna, which needs to be considered.
There are also other limitations present when looking at the ND approach, which do not necessarily have to do with smartphone use [1]:
Because of the use of wireless signals for distance estimations which is subjected to a distance-dependent attenuation, and on the assumption that the distance can be estimated from the measured attenuation, there may occur several errors.
A smartphone might not me carried on the body.
Bluetooth needs to be persistently granted and the app should be activated.
The ND procedure on smartphones consumes more energy than necessary.
Even though the correct hardware and software may be available to make the ND approach work and reliable, it will always get limited in some way, potentially leading to false positives and/or missed contacts [1].
REFERENCES:
[1] Kindt, P. H., Chakraborty, T., & Chakraborty, S. (2020). How Reliable is Smartphone-based Electronic Contact Tracing for COVID-19?. arXiv preprint arXiv:2005.05625. DOI: https://arxiv.org/abs/2005.05625
[2] Ferretti, L., Wymant, C., Kendall, M., Zhao, L., Nurtay, A., Abeler-Dörner, L., ... & Fraser, C. (2020). Quantifying SARS-CoV-2 transmission suggests epidemic control with digital contact tracing. Science, 368(6491). DOI: https://doi.org/10.1126/science.abb6936
[3] Klinkenberg, D., Fraser, C., & Heesterbeek, H. (2006). The effectiveness of contact tracing in emerging epidemics. PloS one, 1(1). DOI: https://dx.doi.org/10.1371%2Fjournal.pone.0000012
[4] Fraser, C., Riley, S., Anderson, R. M., & Ferguson, N. M. (2004). Factors that make an infectious disease outbreak controllable. Proceedings of the National Academy of Sciences, 101(16), 6146-6151. DOI: https://doi.org/10.1073/pnas.0307506101
[5] Eichner, M. (2003). Case isolation and contact tracing can prevent the spread of smallpox. American journal of epidemiology, 158(2), 118-128. DOI: https://doi.org/10.1093/aje/kwg104
[6] Becker, N. G., Glass, K., Li, Z., & Aldis, G. K. (2005). Controlling emerging infectious diseases like SARS. Mathematical biosciences, 193(2), 205-221. DOI: https://doi.org/10.1016/j.mbs.2004.07.006
Digital Contact Tracing Service
The paper focusses on verifying and improving the impact of tracking based on epidemiological models. It hereby presents an improved decentralized, privacy preserving approach of a digital contact tracing service. This tracing of infectious contacts, digital or not, is an epidemiological tool which will only work and be effective if coupled with the ability to test potentially infected people quickly.
The paper ultimately presents a secure solution for a digital contact tracing service (DCTS) that protects the users’ data and identity from attackers. It does this by proposing the use of Bluetooth. and an elaborate explanation of the working of the application.
Each mobile phone equipped with the DCTS app will advertise so called temporary contact numbers (TCNs) to other phones. These TCNs can be seen as tokens. At the same time, it records and stores the TCNs advertised by other phones. Phones will continuously keep advertising their random TCNs and store any observed TCNs from other phones. Whenever a user is infected; they can agree to upload their advertised TCNs to a server. This only happens after approval from medical authorities. Whenever the server matches tokens, it will distribute a notification that contact with an infectious person has happened.
- The following steps will more elaborately discuss how the DCTS app works.
- The app activates Bluetooth and generates a key, which it uses to generate a random TCN, the token which will be given to other nearby phones.
- The phone will be active with this TCN advertised, such that other devices in range of the user can see the TCN. The TCN is updated after a certain amount of time in order to minimize re-identification of the user. Next to that, the TCNs are only stored for a period of two or three weeks, depending on the status of the virus.
- The app stores the observed TCNs and keys from other users.
- Whenever the app spotted another TCN, it will be stored, and phones will exchange their tokens.
- The patient is confirmed infected and is able to upload the advertised TCNs and keys to a server.
- The patient gets the permission by a medical authority to upload the generated TCNs, and keys to a server. The server then regenerates and verifies the patients’ TCNs with the provided keys. For privacy and safety reasons, the server will delete the keys after the verification. The server thus collects newly uploaded TCNs and shuffles their order to avoid the avoid the association of several TCNs to a single user.
- A match occurs within the TCNs on the server.
- The patient’s TCNs are matched against the encountered TCNs registered on the device of the user during the two- or three-week period. If the app detects a match, the user receives a notification that a potentially infectious encounter has been detected. The notification will recommend actions like self-quarantining. The notified user can also be asked to proceed and provide his or her TCNs to allow a recursive tracing.
- Checking whether the user has been in contact with an infected person.
- First approach: The user can download all unchecked TCNs stored on the server and check for matches within their own list of observed TCNs. When encountering matches, the app can perform a risk assessment based on exposure time.
Second approach: in order to prevent attacks on the previous method, it is able to check for the number of TCNs that are both in our set of encountered TCNs and in the set of infected TCNs.
Second order tracing
COVID-19 is infectious before people develop symptoms [2, 3]. So, it might be useful to implement second order tracing. Users who get notified because they have been in contact with an infectious person also uploads their TCNs in order to prevent second order spreading.
The DCTS app uses Bluetooth as a means of contact tracing, because Bluetooth detects only real encounters and works indoors as well as outdoors, where GPS and mobile network data is not reliable. The type of Bluetooth which is used is called Bluetooth Low Energy (BLE). The proposed approach uses BLE for detecting devices in range. The authors suggest that the battery is drained by no more than 5% by contact tracing and that in a situation with 100 devices being close to each other, the probability that all devices discover each other successfully within 10 seconds is close to 100%.
In order to optimize BLE, the most beneficial parameters are used. Thereby their contact tracing is carried out at the highest reliability and the lowest possible energy consumption.
Making use of Bluetooth goes along with the fact that Bluetooth advertises the MAC-address of the device. In order to cope with this, the app stops and restarts advertising immediately when updating the TCN, such that the advertised MAC-addresses change at the same time as the TCNs. These changing TCNs keep the user anonymous and complicate tracking.
Looking at the effectiveness of the DCTS app, the authors mention several things. First, there should be psychologists consulted about the exact wording and information of the notification which would be send to the user, in order to achieve the desired effect. The notification includes possible measures which should be taken en thus is crucial for stopping the spread of the virus.
The DCTS is being evaluated together with intervention strategies. The results are being crosschecked using both deterministic and Monte Carlo based model approaches [4]. The modeling substantiates the following:
- The DCTS needs a broad acceptance among the population of more than 70% in order to have an impact to control an outbreak. The authors believe that “this can be achieved by a decentralized, secure and privacy preserving design where the users own their data” [1].
- Tracing only people who have been in contact with confirmed infectious persons might not be enough. Therefor the paper wants to enable both first order contact tracing and additionally second order contact tracing. “Tracing second order contacts increases significantly the number of traced potentially infected people. If every direct and indirect contact stayed in quarantine, a huge percentage of the population would be affected” [1].
“Achieving widespread acceptance and trust among the population is the key factor for any digital contact tracing systems' success. Only if the potential users trust in the app’s privacy architecture, they will actually use and follow the app in their daily lives. Against this background, it is crucial to obtain the endorsement of trustworthy institutions like the data protection agencies.” [1]
A centralized approach would be more efficient and effective than a decentralized approach. However, with the centralized approach the risk of re-identification of affected persons may be greater. Hence why is chosen for a decentralized approach in the paper. To achieve a higher effectiveness, a centralized approach should be chosen.
REFERENCES
[1] ContacTUM Consortium, ITO Consortium: Digital Contact Tracing Service: an improved decentralised design for privacy and effectiveness. April 17, 2020 (Working Paper)
[2] Ma, S., Zhang, J., Zeng, M., Yun, Q., Guo, W., Zheng, Y., ... & Yang, Z. (2020). Epidemiological parameters of coronavirus disease 2019: a pooled analysis of publicly reported individual data of 1155 cases from seven countries. medRxiv. DOI: https://doi.org/10.1101/2020.03.21.20040329
[3] Rothe, C., Schunk, M., Sothmann, P., Bretzel, G., Froeschl, G., Wallrauch, C., ... & Seilmaier, M. (2020). Transmission of 2019-nCoV infection from an asymptomatic contact in Germany. New England Journal of Medicine, 382(10), 970-971. DOI: https://doi.org/10.1056/NEJMc2001468.
[4] ContacTUM consortium, Digital contact tracing and its impact on the sars-cov-2 pandemics, tba, work in progress (2020).
Interventions
passive interventions
passive interventions = those which do not involve testing or contact tracing.
- Hospitalization:
- Patient stops interacting with household and workplace networks
- Reduction of number of random interactions
- Don’t model interactions within hospitals (this is planned for future work)
- Self-quarantine upon symptoms:
- Stopping interactions on the individual's workplace network
- Reducing their number of interactions on the random network
- Option: everybody in household will be asked to self-quarantine
- Lock-down:
- Reducing number of contact that people have
- Reducing number of interactions that people have by 80% on work-place and random networks
- Increase transmission rate for interactions on the household network
- Shield group: fatality rate is highly skewed towards the over 70s – applying a lock-down just to this demographic group
- Reducing number of contact that people have
- interactions on the household network are not increased
Insert picture table 7 with text: Table 7. Proportion of people in each stage of illness whose disease progresses further; mean and standard deviation for density functions of the times that each transition { disease progression or recovery { takes. Parameter values match the OpenABM-Covid19 baseline parameters, April 28, 2020
Insert table 8 with text: Table 8. Parameters corresponding to passive interventions (hospitalization and self-quarantine upon symptoms). Parameter values match the OpenABMCovid19 baseline parameters, April 28, 2020
Active interventions
Active interventions = involve contact tracing or testing
3 events in the ABM which can be the initial trigger for an active intervention:
- Developing symptoms (true covid-19 or not) in the community
- Testing positive for covid-19
- Hospitalization (clinical diagnosis alone, or combined with a positive test result)
3 types of active intervention which can be triggered:
- Testing for covid-19 infection:
- delays in the testing procedure between ordering and taking a test, and then getting results are modelled
- Self-quarantining:
- stopping interactions on the individual's workplace network
- reducing their number of interactions on the random network
- Digital contact tracing: app-based contact tracing
Implementation details
- Events: an event-based system is used to drive disease progression in individuals and interventions. At each decision point it is calculated when the next event will occur and it is added to an event list for that day. For each type of event, there is an eventlist structure which contains an array of linked lists for each day of the simulation.
- Individuals: each person in the population is represented by an individual structure and the population is static. It contains the following information:
- Demographic: age, house number, network membership
- Interaction diary: list of all interactions over a period of days
- Disease: current status and pointers to both current and future disease events
- Quarantine: the person is currently quarantined, and pointers to that event and the release moment
- Network Construction: Each interaction network has an associated network structure which contains an array of edges
- Can be static, static but down-sampled or dynamic
- Modular at any network
- Transmission: transmitting the pathogen across today's interaction network, which is done as a push from all infected people (by disease status).
- For every infection status the transmission rate for someone who has been infected for that length of time is pre-calculated
- At each time-step go through all the interactions the infected person had for that day and calculate whether transmission has occurred
- each individual gets a quantity of hazard at the start of the simulation
- hazard < 0 = infected
- insert formula here
- Digital Tracing and Release: When an individual self-reports symptoms or tests positive, they become an index case and are assigned an index token
- Digital tracing: performed by looping through all contacts in the interaction diary and if the app recorded the interaction a quarantine message is sent along with the index token
- Individuals store this for 14 days
- Negative test: individuals receive message to remove index token
- Released from quarantine if token is removed
- Performance:
- 96% of CPU usage: rebuilding daily interaction networks and updating the individual’s interaction diaries
- 60% of memory usage: storing the interaction diaries
- 20% of memory usage: storing the semi-static networks
- 20% of memory usage: storing individuals and their states in event list
[1] Dignum, F. (2020). Exit Strategieën [Slides]. Retrieved from https://simassocc.files.wordpress.com/2020/04/nlexitstrategies-190420-1.pdf
[2] Hinch, R., Probert, W., Nurtay, A., Kendall, M., Wymant, C., Hall, M., Lythgoe, K., Cruz, A. B., Zhao, L., STEWART, A., FERRETTI, L., ABELER-D?ORNER, L., BONSALL, D., & FRASER, C. (2020). COVID-19 AGENT-BASED MODEL WITH INSTANTANEOUS CONTRACT TRACING. BIG DATA INSTITUTE, NUFFIELD DEPARTMENT OF MEDICINE, UNIVERSITY OF OXFORD
ASSOCC
Analysis simulation model Delft ASSOCC
The ASSOCC model (Agent-based Social Simulation for the COVID-19 Crisis), is a model that has specifically been designed and implemented by European researchers from Umeå University, TU Delft, Malmö University, Utrecht University, Caen University and Stockholm University to address the societal challenges of the COVID-19 pandemic.
What exactly is it?
This model uses “corona in Simcity” approach to study individual and social reactions to the containment policies. It is a tool for decision makers to explore different scenarios and their effects. It is not a model to generate predictions. It simulates the behavior of a synthetic population given a set of policies (for example when in a lock-down or voluntary isolation). It enables to study the effects on both the spread of the contagion and on how people can be expected to react to the policies (e.g. potential violations or workarounds).
What answers does it provide?
It models both the possible effects on the spread of the coronavirus and the socio-economic effects of the policies, providing possible answers to:
• How might policies based on achieving drastic behavioral change go wrong?
• How might one work with existing social norms and habits to effectively limit virus spread (what will work with populations and what will not?)
• How might we reintroduce people who have recovered from the disease back into society to help others and revive the economy without this leading to social division and a general breakdown of social distancing?
• What are the possible dangers of social polarization between vulnerable older people and the young who want to get together, how might we keep younger people “on board”, how might we stop them losing contact with other generations?
• For particular groups within societies, at particular times of year or day are there safe gathering activities with very low risk of contagion? Are there practices that are particularly dangerous.
• What new social practices might we develop that allow life in a world susceptible to waves of new infection (e.g. red and blue teams in hospital so there is no overlap)?
• Timing and consequences of lifting the restrictions
How does it work?
ASSOCC is made in NetLogo. It is based on a set of artificial individuals, each with given needs, demographic characters, and attitude towards regulations and risks. All the agents decide each time what they should be doing and because of this, many different possible effect of policies can be analyzed.
This figure is a screenshot of the parameter setting in the NetLogo model. (ASSOCC, 2020)
More information about what each parameter means can be found in the pdf: “Hw Kim simulation delft’.
The framework is based on the fact that individuals have to balance their needs over many contexts.
The following image shows how people manage this balancing act in their daily life:
More information about this image can be found in the pdf: 'Hw Kim simulation delft’.
Agents selecting an action:
1. an agent creates a list of all possible places (gathering-points) it can go with different motivations = an action this list is based on their current age, time of day, day in week, parameters set in the model
2. for all these actions, the global expected effect on the needs is calculated (summing over the expected effects x the desire for each main need)
3. the action that satisfied the highest number of needs is selected to be acted upon
after all agents have moved to the location where they want to execute their action, the actions get executed, and the needs get updated
Track and trace apps
ASSOCC has looked at the policy of implementing the ‘corona app’ into society. In their scenario, they assumed a perfect app aligned with all functional, legal and ethical requirements. They studied the effectiveness of such an app by performing 3 experiments:
1. The effect of the app depending on different percentages of the population using the app
2. Comparing the effect of using the app with that of random testing a percentage of the population
3. Effect of the app depending on the characteristics of the users (percentage of risk-avoiding agents that use that app)
The following conditions were used:
• Percentage of app users = (0%, 60%, 80% or 100%)
• Percentage of app users = 0.0 and percentage of population tested randomly daily = (0% or 20%)
• Percentage of app users = 60% and percentage of risk avoidance app users = (0%, 30% or 60%)
Results
Experiment 1: Differing amounts of population using the app
According to ASSOCC, using the app results in a lower infection peak. However, the differences are not significant in a test using 15 randomised runs for each setting, as depicted in curve1.png comparing the settings for no app users, 60% app users, 80% app users and 100% app users, with a population of 1000 agents.
However, as depicted in curve2.png, increasing the number of users results in a sharp increase of testing given that all those that are alerted of being in contact with an infected agent will need to be tested (or required to quarantine themselves).
These results left ASSOCC with the question how does the usage of the app compare with a similar amount of random testing. This gave the basis for experiment 2.
Experiment 2: comparing tests performed through app with random testing
According to ASSOCC, random testing raises infection awareness even when the tested agent had no reason to suspect infection. The differences on number of infected agents under different conditions is shown if curve3.png
Experiment 3: effect of the type of app users.
Next, ASSOCC hypothesized that the people who are most likely to use the app are probably those that are more risk averse. However, in initial tests, they were not able to see a significant difference under this condition.
Conclusion:
The effectiveness of tracking and tracing apps on lowering the number of infected agents is limited and lower than that of random testing. The use of the app results in a sharp increase on the number of agents that need to be tested, which may be above the capacity available in the system.
ASSOCC therefore concludes from this data that the app (with around 60% use) makes no significant contribution to a virus-free Netherlands.
Results show that by themselves these apps have none or minimal effect on the spread of the virus. Besides all legal, constitutional and ethical issues, their use may lead to a false feeling of security which ultimately can contribute to a second wave of the contagion [3].
Other studies, based on large scale mathematical models of epidemics show the opposite effect. I.e. according to those studies, track and trace apps do have a positive effect on the containment of the virus [3].
It is important to compare these types of studies and see why they lead to different results.
The major difference between the ASSOCC model and those used by many epidemiologists is that ASSOCC has a simulation based on human behavior which is used together with the epidemiological model [3].
The important difference between ASSOCC model and other models, lies in a number of specific properties of the corona virus:
1. The time between becoming infected and possibly showing symptoms is quite long. In an epidemiological model, this is translated by giving a parameter a different value. However, when looking at how many interactions people have, and with which other people, probabilistic model in a mathematical model can be used that divides the interactions uniformly or normally over all possibilities. That differs somewhat from reality if the interval in which this happens is short, but not so much that it disturbs the results a lot. However, if that interval becomes longer, the mathematical model is no longer correct. This is often seen in macroeconomic models: they do reasonably well in normal situations, but in crisis situations people do not behave according to expectations and the deviations are too great to make those models even of value.
2. Another issue is the skewed age distribution of the corona virus infection: relatively many young people are asymptomatic. So they are infected without knowing it and spread (with lower chance, but still) the virus. Because they are not being tested, this distribution continues. Young people also meet more other young people on average, so the contagion can go on for quite some time before being noticed. From the perspective of the track and trace apps, this means that people have already fallen from the contact list that is about a week long. In this way, there are a lot of points along which the virus still spreads despite the use of the app.
3. Demographics and living arrangements are also a determining factor. For example people lives who live in Italy look a little different than in the Netherlands. So the results are slightly different, but the conclusion remains. In the Italian case, the positive effect of testing randomly 20% of the population is even greater than in the Netherlands.
The issues above are not easy to capture in macro level models, as those used in epidemiology. ASSOCC considers the difference between people’s ages, backgrounds, living situation and behavioral motives. Many scientific studies point out that the lack of a human behavior model in the epidemic models is a problem. ASSOCC is one of the few in the world that combines the human models with the epidemic models. It would be nice if a lot more research was done, because then this type of models would improve greatly and there would be more comparative studies.
[1]ASSOCC. (2020, April 20). The simulation. Retrieved from https://simassocc.org/assocc-agent-based-social-simulation-of-the-coronavirus-crisis/the-simulation/
[2] ASSOCC. (2020b, April 21). Scenario: effect of track&trace apps. Retrieved from https://simassocc.org/scenario-effect-of-tracktrace-apps/
[3] Dignum, F. (2020, April 19). Mathematics vs. social models: how to understand the sociology of corona virus spread. Retrieved from https://simassocc.org/assocc-agent-based-social-simulation-of-the-coronavirus-crisis/news-and-publications/
More information ASSOCC
“The success of exit strategies does NOT depend on the track and tracing mechanism” [1]
“Using a track and tracing app does NOT give us back our freedom” [1]
An app does help to shorten the time between infection and detection on average, however, the spread of the coronavirus is therefore not controllable. The R0 of the coronavirus is now about 2.2. By using the apps, the simulation of ASSOCC never gives a R0 below approximately 2. That is approximately twice as high what is necessary for spreading control (R0 = 1).
ASSOCC is not against the use of technology, however it should not crease false expectations. Also, the quantity of tests is getting out of hand when using the apps. (see figures last document)
Exit strategies: what does work?
test risk groups in a targeted and regular manner
find out which areas are most likely to pose a risk of infection and illness (hot spots) and what can be done there
For each measure or relaxation of a measure, check which possible consequences this has for public health, society, fundamental rights and economics (use e.g. simulations)
Ask social groups what measures would work for them to restore normal life and use that to check the feasibility and consequences of measures
Then, look at those points and look where the use of technology can make most positive contributions
Conclusion
Tracking and tracing apps are NEVER a complete solution
Exit strategies should be focused on specific target groups
Exit strategies have to be combined and then tested before being applied so that any bottlenecks can be found
Situations in countries differ, so strategies can not just be taken over from other countries
Contact with Frank Dignum about the comparison of ASSOCC with other simulations
“Hi Kim, Take a look at the paper attached. The Dutch government based their decision of implementing a track and tracing app on the model described in this paper (see below). I must warn you that comparing the models is not simple. We will publish an article about this soon. But it took us a lot of time to make a precise comparison where all the assumptions are clear and parameters and functions are explicit such that one can compare the results. We did all that and can now show that the apps still will not be effective if you take into account the human behavior as it is known. Good luck, Frank.”
COVID-19 agent-based Model with instantaneous contract tracing
What is it?
The agent-based model (ABM) from the Dutch government was developed to simulate the spread of COVID-19 in a city, and to analyze the effect of both passive and active intervention strategies.
ABM explores the effectiveness of contact-tracing app intervention by modelling five alternative scenarios which differ in how far the contact tracing extends through the contact network and the conditions on which individuals are released from app-instructed quarantine.
What is its purpose?
To assist the design and evaluation of approaches to instantaneous contact tracing using a mobile phone app that measures proximity events between phones with the app.
Why is it good?
An ABM is well-suited to quantifying the effects of combinations of non-pharmaceutical interventions in an epidemic because, unlike a simple epidemiological model, it records a history of previous events
How does it work?
It includes the three major domains of interaction: the home, the workplace (or school for children, or a regular social environment for older individuals), and the random interactions of daily life and travel.
- The ABM is age-stratified
- It is not spatially stratified at this stage
- The contact processes are currently parameterized based previous work interviewing participants; they will be updated based on contact data collected by phone.
The model of infection spread via interactions between individuals is parameterized based on the current literature of COVID-19 epidemiology and can be updated as more data emerges.
Demographics
The demographics of the ABM are based upon UK national data from 2018 from the Office of National Statistics (ONS).
Individuals are categorized into nine age groups by decade, from age group (0-9 years) to (80+ years).
Every individual is part of a household, which forms an important part of their daily interactions.
Since the duration of the simulated epidemic is less than a year, we do not consider changes in the population due to births, deaths due to other causes, and migration. (Migration is taken into account in ASSOCC)
insert picture table here with this text: Table 1. Age-stratified population of the UK and number of households containing n people, with n = 1; 2; : : : 6, provided by the ONS. Parameter values match the OpenABM-Covid19 baseline parameters, April 28, 2020
Interaction Network
Every individual in the population is represented by a node in the simulation. Interactions between individuals are modelled via connections between nodes. The connections form
networks, which are generated to represent different types of daily interactions.
3 types of network: household, workplace, miscellaneous interactions
Some of these networks are static and recur daily (e.g. household), whilst others are transient and are regenerated daily (e.g. miscellaneous).
A previous study of social contacts for infectious disease modelling has estimated the mean number of interactions that individuals have by age group. This study is based on participants being asked to recall their interactions over the past day. We estimate mean interactions by age group by aggregating data (see Table 2).
insert picture table 2 here with text: Table 2. Average number of interactions for an individual in each age group acquired from empirical estimates (14). Parameter values match the OpenABM-Covid19 baseline parameters, April 28, 2020
Household network
There are two important population-level aggregate statistics that we match: the householdsize structure and the population age-structure.
A reference panel with 10,000 households containing the household composition by age, produced by down-sampling UK-wide household composition data from the 2011 Census produced by the ONS is used to form the households.
Workplace network
Each individual is a member of one workplace network (including e.g. schools for children and social activities for older adults).
When on workplace the absence of overlaps between the household interactions and the local interactions on the small-world network is ensured.
Parameters and values corresponding to the workplace network are shown in Table 3.
insert picture table 3 here with text:Table 3. Mean numbers of daily connections for members of each age group, fraction of adults involved in occupational networks for children and for elderly people, and rewiring parameters for randomisation of daily interactions (14). Parameter values match the OpenABM-Covid19 baseline parameters, April 28, 2020
Random Network
The number of random connections an individual makes is the same each day (without interventions) and is drawn at the start of the simulation from a negative-binomial distribution, an over-dispersed skew distribution.
The mean numbers of connections were chosen so that the total number of daily interactions matched that from a previous study of social interaction
Insert picture table 4 here with text: Table 4. Parameters for numbers of random connections that members of each age group have per day. Parameter values match the OpenABMCovid19 baseline parameters, April 28, 2020
Infection Dynamics
The infection is spread by interactions between infected and susceptible individuals.
The rate of transmission is determined by three factors:
- the status of the infector;
- the susceptibility of the infectee to infection, according to age;
- the type of interaction (i.e. on which network it occurred).
currently the model does not have data on the distribution of the duration of interactions, so the effect of this on transmission is not modelled.
Infectiousness starts at zero at the precise moment someone is infected (t = 0), reaches a peak at some intermediate time, and tends to zero a long time after infection (large t ).
Asymptomatic individuals are those who never develop symptoms during their infection
pre-symptomatic individuals are those who do not currently have symptoms but will do so later
both types may infect others
To model the susceptibility to infection of a contact according to their age there was referred to the literature where close contacts of confirmed cases were monitored and tested. The number tested and the number of positive results was reported within each age group, with the ratio of the latter to the former defining the per-age attack rate.
Model the type of interaction, (on which network it took place): Whilst we do not have data on the length of interactions, interactions which take place within a person's home are likely to be closer than other types of interactions leading to higher rates of transmission. This is modelled using a multiplicative factor.
Combining all effects, the rate at which the virus is transmitted in a single interaction is modelled by
Insert picture formula
t = time since infection
si = infector’s symptom status (asymptomatic, mild, moderate/severe)
as = age of susceptible
n = type of network where the interaction occurred
Ias = mean number of daily interactions for somebody of the age of the susceptible
Fr(u;u, o2) = probability density function of a gamma distribution
ui and qi = mean and width of the infeciousness curve
R = scales the overall infection rate
SaS = scale-factor for the age of the susceptible
Ast = scale-factor for the infector being asymptomatic
Bn = scale-factor for the network in which the interaction occurred
Insert table 6 with text: Table 6. Description of infection parameters and their values. The infection rate x was determined by fitting the simulation to have an epidemic doubling time of 3 days. Relative susceptibility values* were derived by merging and fitting to data from sources as explained in the text. Parameter values match the OpenABM-Covid19 baseline parameters, April 28, 2020
The rate of virus transmission is converted to a probability of transmission:
Insert formula P(t,si,as,n) = 1- e^l(t,st,as,n)
Insert table 5 with text Table 5. Steps in our calculation of susceptibility by age. The attack rate (the fraction of close contacts of a confirmed case infected) was merged from references. We fit to these values, and then scale them all identically to give a normalized susceptibility to infection. Parameter values match the OpenABM-Covid19 baseline parameters, April 28, 2020
insert figure 1, with text Figure 1. The attack rate, defined as the fraction of close contacts of a confirmed case infected, as a function of the contacts' age. Open circles show data merged from references. the line shows the fit A+B x (age)k.
Natural History of infection
Disease state transitions are shown in figure 2
insert figure 2, with text Figure 2. The disease status of an individual and the probability and time distribution of transitions. The _xxx(age) variables are the probability of transition to a particular state when there is a choice, where the probability depends upon the age of the individual. The _xxx are the gamma distributed variables of the time taken to make the transition.
Upon infection, an individual enters a disease progression cascade where the outcome and rates of progression depend on the age of the infected person.
Once an individual is recovered it is assumed that they have immunity and cannot be re-infected.
pre-symptomatic state= in which a person is infectious but does not have symptoms
Bluetooth
Why use Bluetooth?
For contact tracing, solutions such as WiFi MAC address sniffing, GPS, and cellular network geolocationg have hall been proposed. However, the most suitable for use in CTA is often believed to be Bluetooth tracing. Many point to the effectiveness for proximity detection, that has already been demonstrated (Berke et al, 2020; Brack et al, 2020). They also claim that while Bluetooth has an effective range of around 25-30 metres, signal strength can be used to effectively identify whether another device is within the 2-metre rule promoted as a component of social distancing. [1]
However, for many proposing CTA, the idea of using an app instead of just network tracing via the cellular network or other means is not as much about Bluetooth being more accurate, it is about the idea of claiming to have informed consent: that by downloading the app and clicking through a privacy agreement they have received ‘informed consent’ to access and monitor an individual through their device. [1]
Smartphone apps for Bluetooth-based contact tracing, such as the European PEPP-PT project, the British NHSX, or the Swiss D3PT, can help to identify individuals that have recently had an infection-relevant contact (i.e. one that confers a risk of transmission) with known Covid-19 cases and might therefore have been infected. [2]
Since a large percentage of the world’s population carries smartphones, these approaches make use of the BLE technology. Contact advertisements regularly emitted from these devices are used to assess the proximity of encounters [4]
How does it work?
There are several different ways on how to tackle the use of Bluetooth. Below, you can see some different examples of how the process is tackled
First example
The data being collected Drawn from many of the cited papers in this work, most apps will collect and transmit some subset of the following data fields:
- MAC address of your device’s Bluetooth or Wi-Fi chip
- Your Phone number (or IMEI number if the device does not easily report the subscriber phone number)
- The MAC address of other people your phone sees (Bluetooth handshakes with everything it sees that is also Bluetooth, even when it doesn’t know the device and has never been paired with it)
- The time, date and in some cases, location data from your GPS for each new interaction with another in-range device (accurate to about 15 meters). A new interaction is when your device sees another device move into its broadcast area. Note that in a corporate office the app might see the device of someone in the next room move into and out of range tens or hundreds of times over the course of a working day.
- The Bluetooth or device name of the smartphone that is running the app, and every other Bluetooth device that crosses into its broadcast range. This last point can more easily enable re-identification as people often name their smartphone ‘Tim’s iPhone’ or similar. [1]
Second example
This second example focusses more on the “privacy by design” COVID-19 tracing approach. It is the TraceTogether app from the Singaporean government. Unlike the contact point system, it only requires users to enable Bluetooth on their phone. Pan-European Privacy-Preserving Proximity Tracing (PEPP-PT) by the European consortium , as well as Google and Apple’s recently announced joint initiative, are following a very similar concept. We present a slightly modified version below. In order to detect whether two people have come into close enough physical proximity to risk an infection, one can use Bluetooth low energy technology. The general drawback of Bluetooth—that it can only reach across a few meters—becomes an advantage here. The tracking itself would work as follows: as many people as possible voluntarily install the app on their phone. The app cryptographically generates a new temporary ID every half hour. As soon as another phone with the same app is in close proximity, both phones receive the temporary ID of the respective other app and record it. This list of logged IDs is encrypted and stored locally on the users’ phones
As soon as an app user is diagnosed with COVID-19, the doctor making the diagnosis asks the user to share their locally stored data with the central server (Figure 2). If the user complies, the central server receives information on all the temporary IDs the “infected” phone has been in contact with. The server is not able to decrypt this information in a way that allows for the identification of individuals. However, it is able to notify all affected phones. This is because the server does not need any personal data to send a message to someone’s phone. The server only needs a so-called PushToken, a kind of digital address of an app installation on a particular phone. This PushToken is generated when the app is installed on the user’s phone. At the same time, the app will send a copy of the PushToken, as well as the temporary IDs it sends out over time, to a central server. The server could be hosted, for example, by the Robert Koch Institute for Germany or by the National Health Service for the United Kingdom. This way, it would be possible to contact phones solely based on temporary IDs and PushTokens whilst completely preserving the privacy of the person using the phone.
If a phone has been in close proximity to an “infected” phone, the user of that phone receives a notification together with the request to immediately go into quarantine at home. The user will then need to contact the local health authorities to get tested for the virus as soon as possible so that, depending on the outcome, the user is either able to stop quarantining or all their contacts can be informed (Figure 2). During the entire process, no one learns the identity of the app user (eg, other users who got in close contact with them, the local health authorities, the central server) since the app is not linked to an identity. Location data is neither recorded nor stored at any point of the process [3]
[1] https://arxiv.org/ftp/arxiv/papers/2005/2005.06621.pdf
[2] https://www.medrxiv.org/content/10.1101/2020.03.27.20045237v2.full.pdf
[3] https://mhealth.jmir.org/2020/4/e19359/pdf
[4] https://arxiv.org/pdf/2004.11841.pdf
What goes in the paper
Why use Bluetooth?
For contact tracing, solutions such as WiFi MAC address sniffing, GPS, and cellular network geolocationg have hall been proposed. However, the most suitable for use in CTA is often believed to be Bluetooth tracing. Many point to the effectiveness for proximity detection, that has already been demonstrated [a,b]. They also claim that while Bluetooth has an effective range of around 25-30 metres, signal strength can be used to effectively identify whether another device is within the 1,5-metre rule promoted as a component of social distancing. [c]
However, the original Bluetooth BR/EDR protocol, while it was designed for primarily “pairing” phones with other devices such as computers, Bluetooth speakers, or keyboards for the purpose of data communication, it was a non-time sensitive process. It was not designed to have a reliable and sustainable contact tracing, as what currently is looked into as a solution for this pandemic. In the traditional pairing process, if the pairing is not successful then the user has to reset one of the devices and try again. This manual intervention is not sustainable in the context of contact tracing, where two or more phones are always expected to “pair” reliably.
In comparison, the Bluetooth Low Energy (BLE) protocol, has been designed for continuously scanning in the background and is therefore the main choice for neighbor discovery on smartphones. The main reason why contact tracing apps choose for continual transmission and listening instead of continuous is energy [d]. The energy costs would be higher when using continuous transmission and listening.
How to optimize Bluetooth?
There is however a problem that arises with the use of BLE. It can namely travel through a wall. Even though the more objects there are in between the devices, the less overall range a device will have [e], it can lead to some troubling scenarios.
One of these scenarios is tracing through your neighbors wall. Imagine your neighbor, who you don’t come in contact with, tests positive for the virus. Both phones, yours and theirs, connect with each other via Bluetooth through the wall, it can lead to possible quarantine for you, even though you haven’t come in contact with each other. This leads to some problems especially in heavily populated areas, such as in cities and apartment complexes.
One solution that we propose, would be the use of sound in combination with this BLE. While the BLE detects the phones at a continuous pace, the sound application could act as a safe switch to check whether there is an object such as a wall in between both phones.
References
[a] Berke, A., Bakker, M., Vepakomma, P., Raskar, R., Larson, K., & Pentland, A. (2020). Assessing disease exposure risk with location histories and protecting privacy: A cryptographic approach in response to a global pandemic. arXiv preprint arXiv:2003.14412.
[b] Brack, S., Reichert, L., & Scheuermann, B. (2020). Decentralized Contact Tracing Using a DHT and Blind Signatures. Last accessed: 01st May, 2020. Sourced from: https://eprint.iacr.org/2020/398.pdf
[c] Mclachlan, Scott & Lucas, Peter J. & Dube, Kudakwashe & Hitman, Graham & Osman, Magda & Kyrimi, Evangelia & Neil, Martin & Fenton, Norman. (2020). Bluetooth Smartphone Apps: Are they the most private and effective solution for COVID-19 contact tracing?. Sourced from: https://arxiv.org/ftp/arxiv/papers/2005/2005.06621.pdf
[d] P.H. Kindt, T. Chakraborty, & S. Chakraborty. 2020. How Reliable is Smartphone-based Electronic Contact Tracing for COVID-19?. arXiv preprint arXiv:2005.05625. DOI: https://arxiv.org/abs/2005.05625
[e] TechWalla. (n.d.). What are the limitations of bluetooth. Retrieved May 27, 2020, from https://www.techwalla.com/articles/what-are-the-limitations-of-bluetooth
Decentralized Approach
For this app there is a choice between handling with a centralized or a decentralized approach. In a centralized approach, the government authority will control the personal data. With a decentralized approach, the collected data will be stored locally with the user [a]. The choice regarding the use of a centralized or decentralized approach lies mainly within the arguments regarding data protection and privacy.
With centralized structures, the collected data of the app is controlled by the government authority. Centralized apps follow mainly the PEPP-PT (Pan-European Privacy-Preserving Proximity Tracing) [b], but this framework is according to the technical community too academic for practical development. A decentralized structure has the data enclosed or controlled by individuals on only personal devices. Those apps follow DP-3T (Decentralised Privacy-Preserving Proximity Tracing) [c], but this is only partly decentralized. No pooled data is collected, which largely mitigates the privacy risk. The none-infected individuals’ data are decentralised based, and the infected individuals’ information will be collected anonymously to a central database. [a] Google and Apple will release an exclusive decentralized framework which will be more compatible with IOS and Android systems [d].
There would be a trade-off between the insights gained and the privacy of the data. The decentralised and no GPS solution gives one of the highest level of data protection for users because no personal data is collected unless the individual is infected with the virus. Apps cannot collect the movements and trace them geographically without GPS tracking. This means that the data can’t be traced to an individual. Bluetooth tracing does work as compatible technology for this decentralized approach. However this means that data collected can not be driven into a centralized database for analysis and the government has less information for controlling the self-quarantine and movement of the disease. [a]
In conclusion, a decentralized approach would fit well regarding data issues and be more compatible with a Bluetooth based system. This together with the fact that there is a strongly growing trend globally, and especially in Europe, which shows that the decentralised approach would be preferable [27, 28], finalizes our advice to use a decentralized approach.
[a] Li, J., & Guo, X. (2020). COVID-19 Contact-tracing Apps: A Survey on the Global Deployment and Challenges. arXiv preprint arXiv:2005.03599.
[b] Cooper, D.; Quathem, K.V.; Meneses, A.O. COVID-19 Apps and Websites – The “Pan-European Privacy Preserving Proximity Tracing Initiative” and Guidance by Supervisory Authorities. Available online: https://www.insideprivacy.com/covid-19/covid-19-apps-and-websites-the-pan-european-privacy-preserv ing-proximity-tracing-initiative-and-guidance-by-supervisory-authorities/ (accessed on 5 May 2020).
[c] GitHub. Decentralized Privacy-Preserving Proximity Tracing. Available online: https://github.com/DP-3T/documents/blob/master/README.md (accessed on 5 May 2020).
[d] Apple Newsroom. Apple and Google partner on COVID-19 contact tracing technology. Available online: https://www.apple.com/newsroom/2020/04/apple-and-google-partner-on-covid-19-contact-tracing-techno logy/ (accessed on 5 May 2020).
[27] O. Lynskey, & M. Veale. 2020. Supplementary Written Evidence on COVID-19 Tracing Apps to the Joint Committee on Human Rights. DOI: https://doi.org/10.31228/osf.io/p7kqw
[28] J. Li, & X. Guo. 2020. COVID-19 Contact-tracing Apps: A Survey on the Global Deployment and Challenges. arXiv preprint arXiv:2005.03599. DOI: https://arxiv.org/abs/2005.03599
Related works, Models
A simulation model is one of the methods that is commonly used in Operational Research. Operational research (OR) deals with the application of advanced analytic models to help make better decisions. A simulation model represents the real situation that occurs in a system and tests multiple scenarios based on different behavior [4]. Simulation models can be useful to obtain more of an understanding about a current system by testing scenarios using specific software tools [4]. It can be seen as an incorporating time that reflects to any changes that occurs over time [4].
Because of the COVID-19 pandemic, the government has to come up with a set of policies to contain the virus. Multiple simulation models are used to see what effect certain policies have on society. The mobile contact-tracing app is one of these policies which can be tested with the simulation models.
The ASSOCC model (Agent-based Social Simulation for the COVID-19 Crisis), is a simulation model that has specifically been designed and implemented by European researchers from Umeå University, TU Delft, Malmö University, Utrecht University, Caen University and Stockholm University to address the societal challenges of the COVID-19 pandemic [1]. This model studies the individual and social reactions to containment policies and it is a tool that can be used by decision makes (such as the government) to explore the different scenarios with their effects. The ASSOCC model does not generate predictions, however, it simulates the behavior of a synthetic population given a set of policies (for example the contact-tracing app) [1]. The model enables to study the possible effects on the spread of the virus, how people can be expected to react to the policies and the socio-economic effects of the policies [1]. ASSOCC is built in NetLogo, which is a multi-agent programmable modeling environment [5]. It is based on a set of artificial individuals which each have a set of given needs, attitude towards regulations and risks, and demographic characters [1]. Each artificial individuals decides at each time what they should be doing. These decisions are based on the individual’s profile, state and social, psychological and physical needs [1]. An action is selected by an individual by first making a list of all possible places it can go to with different motivations, which is called an action [1]. It then calculates the global expected effects on the needs of these actions and it lastly selects the action which satisfies the highest number of needs [1].
The ASSOCC model has looked at the effects of implementing the contact-tracing app policy into society. In this scenario, a perfect app aligned with all functional, legal and ethical requirements is assumed [2]. The effectiveness of such an app was researched by performing three experiments. First, the effect of the app depending on different percentages of population (0%, 60%, 80% or 100%) using the app was studied. According to the ASSOCC model, using the app does result in a lower infection peak, however, these differences are not significant and increasement of app users results in a sharp increasement of needed testing [2].
Next, the effect of using the app was compared with random studied of a percentage (0% or 20%) of the population. According to the ASSOCC model, random testing raised the awareness of infection, even when the artificial individuals had no reason to suspect infection and is more effective than the app [2].
Third, The effect of the app depending on the percentage of risk avoiding individuals that use the app (0%, 30% or 60%) was studied. According to the ASSOCC model, the effects of risk averse people were not significantly visible [2].
It can be concluded from the model that the effectiveness of contact-tracing apps on lowering the rate of infected individuals is limited and lower than that of random testing and that the app makes no significant contribution to the spread of the virus [2].
The Dutch government based their decision of implementing a contact-tracing app on the COVID-19 agent-based model (ABM) with instantaneous contact tracing. It was developed to simulate the spread of COVID-19 in a city, and to analyze the effect of passive and active policies [6]. The demographics of this model are based upon UK national data for 2018 from the Office of National Statistics [6]. The ABM model is based on a set of artificial individuals which are categorized into nine age groups by decade. Each individual is part of a structural and transient network and is part of a household, which is an important part of their daily activities. Everyday, each individual interacts with a random subset of their connections and has random connections. The status of the infector, the susceptibility of the infected person to infection according to age and the type of interaction determine the rate of transmission of the virus [6].
The active policy of digital contact-tracing was studied in this model. When contact-tracing, a random number of interactions is assigned to the model. The usage of the app is just as the model age-dependent. According to the ABM, contact tracing is vital to control the spread of COVID-19 for infections with high levels of pre-symptomatic transmission [6]. The ABM allows to explore this policy and its effects and contains the option for recursive tracing of contacts of contacts [6].
Both the ASSOCC model and the ABM are agent based simulations. This means they are able to handle with the uncertainty and variability of the system [1]. Both models are however constructed differently, which leads to different results of the effectiveness of a contact-tracing app. In this paper, these two models are analyzed and compared to each other to give advice about the effectiveness of contact-tracing apps.
Sources
[1]ASSOCC. (2020, April 20). The simulation. Retrieved from https://simassocc.org/assocc-agent-based-social-simulation-of-the-coronavirus-crisis/the-simulation/ [2] ASSOCC. (2020b, April 21). Scenario: effect of track&trace apps. Retrieved from https://simassocc.org/scenario-effect-of-tracktrace-apps/ [3] Dignum, F. (2020, April 19). Mathematics vs. social models: how to understand the sociology of corona virus spread. Retrieved from https://simassocc.org/assocc-agent-based-social-simulation-of-the-coronavirus-crisis/news-and-publications/ [4] Sumari, S., Ibrahim, R., Zakaria, N. H., & Ab Hamid, A. H. (2013). Comparing three simulation model using taxonomy: System dynamic simulation, discrete event simulation and agent based simulation. International Journal of Management Excellence, 1(3), 54-59. [5] Wilensky, U. (2016). NetLogo Home Page. Retrieved from https://ccl.northwestern.edu/netlogo/ [6] Hinch, R., Probert, W., Nurtay, A., Kendall, M., Wymant, C., Hall, M., Lythgoe, K., Cruz, A. B., Zhao, L., STEWART, A., FERRETTI, L., ABELER-D?ORNER, L., BONSALL, D., & FRASER, C. (2020). COVID-19 AGENT-BASED MODEL WITH INSTANTANEOUS CONTRACT TRACING. BIG DATA INSTITUTE, NUFFIELD DEPARTMENT OF MEDICINE, UNIVERSITY OF OXFORD
Deliverables
The final version of the research paper can be found here: File:Final version paper.pdf
The link to the video presentation can be found here: [2]
The peer review as done by the group can be found here: File:Peer review.pdf (keep in mind that a part of the table can be found on the second page)
This results in the following adjustments to grades:
| Name | Adjustment |
|---|---|
| Ezra Leeuwenhage | -1 |
| Paulien Teuwen | 0 |
| Yorn Thijssen | 0 |
| Ries van de Ven | +0.5 |
| Kim Wintraecken | +0.5 |